
A new phishing campaign is impersonating LastPass in an attempt to steal user credentials by claiming a breach and urging recipients to update their desktop app.
First detected on October 13, 2025, the campaign uses lookalike domains and social engineering tactics to deceive users, mirroring a similar attack that targeted 1Password users just last week.
The malicious emails are being sent from spoofed addresses such as hello@lastpasspulse[.]blog and hello@lastpassgazette[.]blog, using alarming subject lines like “We Have Been Hacked – Update Your LastPass Desktop App to Maintain Vault Security.” The emails direct victims to phishing domains, including lastpassdesktop[.]com and lastpassgazette[.]blog, which host fake update pages designed to harvest login credentials. Another domain, lastpassdesktop[.]app, has also been registered by the attackers, likely to support future waves of the campaign.
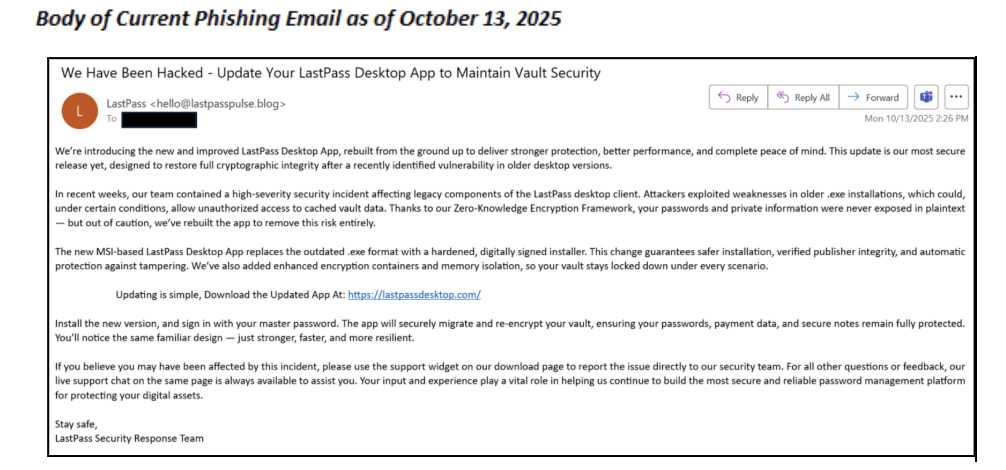
Mike Kosak of LastPass confirmed that the company has not suffered a security breach. Rather, attackers are exploiting users’ trust in the password manager and inducing panic to drive engagement with fraudulent links.
This campaign appears well-resourced and deliberate, evidenced by several factors. The phishing infrastructure is hosted on IP addresses 172.67.147[.]36, 172.67.219[.]2, and 84.32.84[.]32, with bulletproof hosting provider NICENIC reportedly involved in keeping the malicious domains online.
LastPass, one of the most widely adopted password managers, serves millions of individual users, families, and businesses, managing encrypted vaults that store login credentials, sensitive notes, and digital certificates. Due to the high value of these vaults, password managers have become prime targets for cybercriminals seeking maximum impact from credential theft.
This campaign closely follows a similar phishing attempt uncovered on October 2, which targeted a Malwarebytes employee using a fake 1Password breach alert. In that case, the attackers mimicked 1Password’s Watchtower system to lure victims into visiting onepass-word[.]com, a site hosting a replica login page for vault credential harvesting. That campaign also leveraged legitimate infrastructure, Mandrillapp, for redirection, further complicating detection.
Taken together, the LastPass and 1Password phishing campaigns suggest an ongoing and possibly coordinated effort to hijack password manager accounts, possibly using recycled phishing kits or templates that are easily adapted for different platforms.
At the time of writing, Cloudflare has intervened by placing warning interstitial pages in front of the known malicious domains, alerting visitors that they are phishing sites. However, users who received the phishing emails before this mitigation may still be at risk.







Leave a Reply