
Trend Micro and the Zero Day Initiative (ZDI) have uncovered a fast-evolving botnet campaign dubbed RondoDox, which is actively exploiting at least 56 vulnerabilities across more than 30 vendors.
The campaign has transitioned from targeted attacks to a large-scale “exploit shotgun” strategy, indiscriminately firing off a wide array of payloads at vulnerable, internet-exposed infrastructure globally.
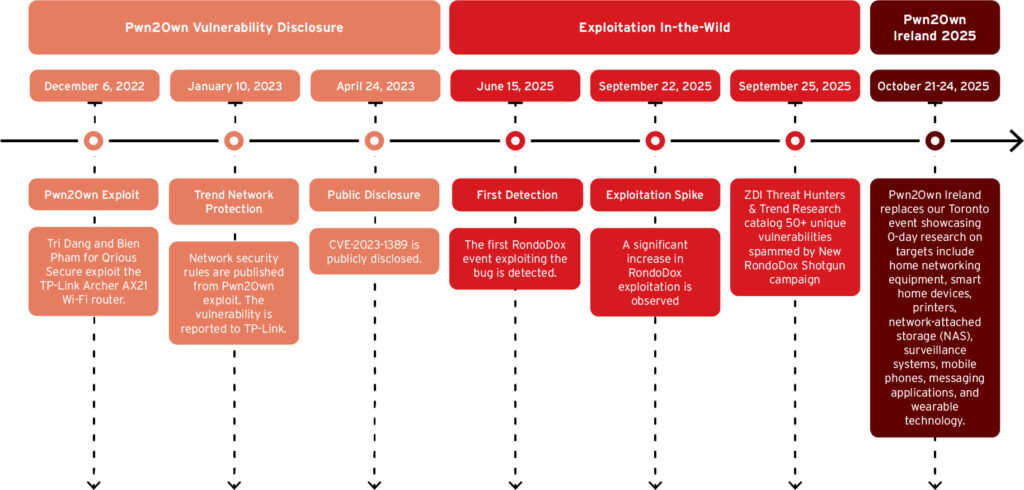
From Pwn2Own to widespread attacks
The first RondoDox-related activity was observed on June 15, 2025, when Trend’s telemetry flagged an intrusion attempt exploiting CVE-2023-1389, a TP-Link Archer AX21 WAN interface vulnerability. The flaw was originally demonstrated at Pwn2Own Toronto 2022 by Tri Dang and Bien Pham of Qrious Secure, using an authentication bypass and command injection combo.
This vulnerability, which had previously been used in Mirai-based campaigns, marked the transition of Pwn2Own research into active weaponization. Trend Micro notes that bugs first shown at its Pwn2Own consumer events continue to serve as a key source of exploitation material for botnet operators.
The research also references earlier RondoDox activity documented by FortiGuard Labs, including targeted exploitation of CVE-2024-3721 (affecting TBK DVRs) and CVE-2024-12856 (affecting Four-Faith routers). By September 2025, the botnet was observed distributing payloads at scale via a loader-as-a-service (LaaS) model, bundling RondoDox with Mirai and Morte malware strains across a rotating infrastructure set.
RondoDox is characterized by its ability to exploit command injection flaws in edge devices to gain remote shell access, which it uses to deliver multi-architecture malware payloads. Its loader supports modular delivery, helping it rapidly adapt to new targets and configurations. The latest wave shows a shift from opportunistic compromise to a coordinated, multi-vector loader operation, significantly expanding the botnet’s reach.
Between June and September 2025, Trend Micro documented a clear escalation in activity, including a September 22 exploitation spike seen in their telemetry, followed by CloudSEK’s report on September 25 detailing RondoDox’s loader infrastructure expansion.
The botnet campaign utilizes a set of 56 vulnerabilities, 38 of which have assigned CVEs. Most flaws are command injection issues, with a smaller number involving path traversal, authentication bypass, buffer overflow, and memory corruption.
Targeted devices span consumer, enterprise, and industrial use cases, including routers, digital and network video recorders (DVRs/NVRs), CCTV systems, and web servers.
Vendors and notable CVEs include:
- TP-Link: CVE-2023-1389 (Pwn2Own bug in Archer AX21)
- Four-Faith: CVE-2024-12856 (Industrial routers)
- TBK: CVE-2024-3721 (Multiple DVR models)
- QNAP: CVE-2023-47565 (VioStor NVR)
- TOTOLINK: CVE-2025-1829 and CVE-2024-1781
- D-Link: Multiple legacy and current routers affected by CVE-2023-25280, CVE-2020-25506, CVE-2015-2051, and more
- Netgear: CVE-2016-6277, CVE-2020-27867
- Linksys: CVE-2025-34037, with additional unnamed apply.cgi variants
- Cisco: CVE-2019-1663
- Apache HTTP Server: CVE-2021-41773, CVE-2021-42013
- GNU Bash: CVE-2014-6271 (Shellshock)
At least 18 vulnerabilities have no CVE assignment, suggesting ongoing exploitation of zero-days or long-standing unreported flaws in devices from brands like TVT, LILIN, ASMAX, Fiberhome, IQrouter, and BYTEVALUE.
The RondoDox campaign reflects a shift in botnet strategy toward automated, modular exploitation of aging infrastructure at scale. Its reliance on a loader-as-a-service backend and an expanding pool of N-day and zero-day exploits suggests ongoing operational development. As of October 2025, the campaign remains active.
Users are recommended to apply the latest firmware updates for their devices, apply network segmentation to isolate critical devices, and disable unused IoT devices when not needed.







Leave a Reply