
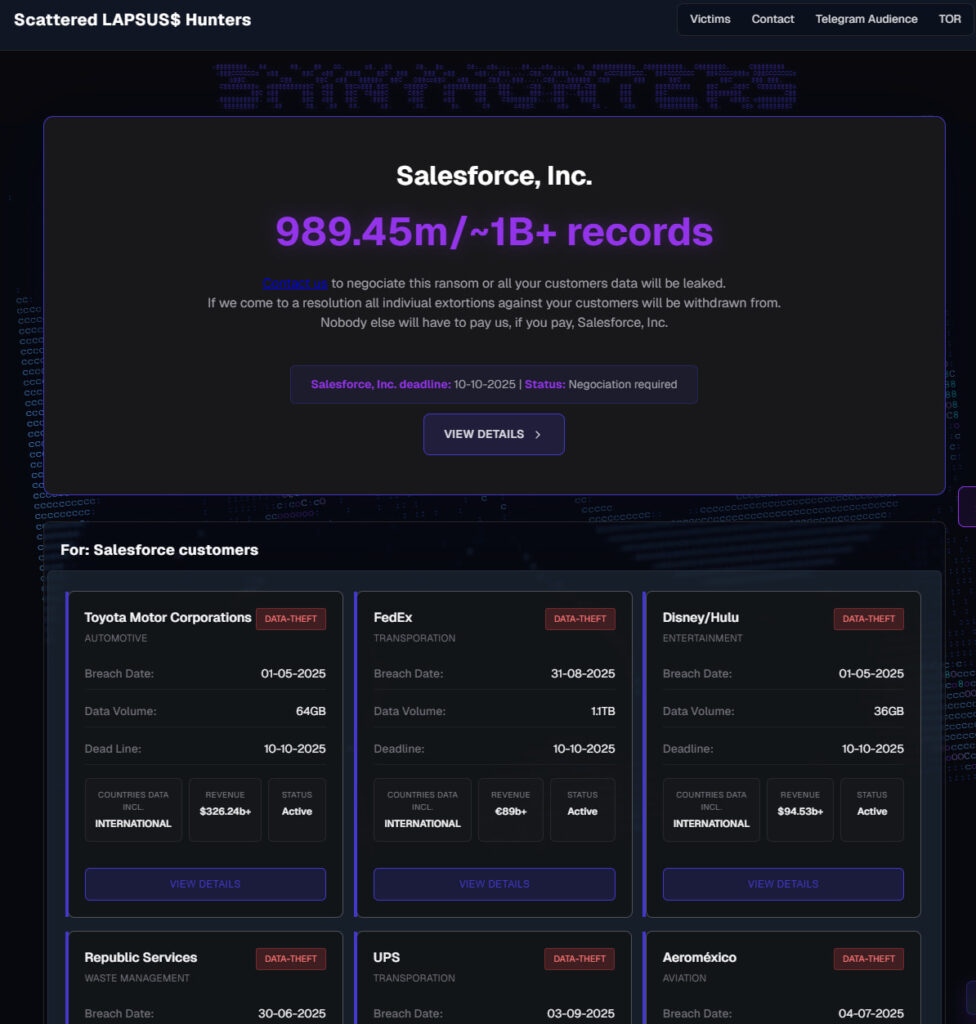
Scattered LAPSUS$ Hunters have published a dedicated online portal claiming responsibility for a wide-scale data-theft campaign involving the exploitation of Salesforce products.
The hacking and cybercrime collective posted samples tied to scores of corporate victims, including major global brands across automotive, retail, transportation, hospitality and cloud SaaS. The portal lists breach dates and sample volumes for more than 50 affected companies and sets a public “deadline” of October 10, 2025, after which the group threatens full public disclosure.
The actors explicitly connect many of the intrusions to compromises of Salesforce customer instances and claim to have exfiltrated “multiple TBs” of data and “near 1 billion records” containing sensitive PII. The portal also provides a catalogue-style victim list (Toyota, FedEx, Disney/Hulu, UPS, Aeroméxico, Home Depot, Marriott, Walgreens, Stellantis, Qantas, Google AdSense, Cisco, TransUnion and dozens more) with per-victim dates and sample sizes ranging from single-digit gigabytes to hundreds of gigabytes.
Our previous reporting, together with threat analysis reports by cybersecurity firms, chronicle a lengthy campaign that previously targeted third-party integrations (notably Salesloft’s Drift/Drift integrations and other Salesforce-connected apps) and used VPNs to mask exfiltration. The disclosure on the portal appears to be the latest escalation in that campaign. The threat actors claim to have repeatedly notified companies (they reference prior taunting emails from July 2025) and now threaten litigation support to pressure compliance.
The actors assert they exploited Salesforce customer environments (including via OAuth/third‑party apps), and they say poor enforcement of two‑factor authentication and weak OAuth protections enabled unauthorized access. The posting alleges exfiltration of raw records that include driver's licenses, dates of birth, social security numbers and other regulated fields, and claims to hold strategic corporate data that “could compromise market position.” The actors also post individual victim metadata, indicating a campaign spanning over a year.
The victim list is broad and touches firms that are data controllers and processors across jurisdictions with strict privacy laws (GDPR, CCPA, HIPAA). Many listed companies are large enterprises with global operations and substantial revenue. Some of the listed victims have publicly disclosed impact by Salesforce attacks, while others were disclosed for the first time now. It is important to underline that none of the data samples leaked by the threat actors on the portal have been confirmed as authentic by the impacted organizations as of writing.
Scattered LAPSUS$ Hunters calls all listed organizations to verify their corporate email addresses to establish a real-time communication channel with them and arrange a resolution. Typically, the arrangement would involve the payment of a ransom in exchange for a promise to delete the stolen data.







Leave a Reply