
ESET researchers have uncovered two separate Android spyware campaigns designed to deceive privacy-conscious users by impersonating secure messaging apps Signal and ToTok.
The malware, not found in official app stores, is being distributed via phishing websites and fake app marketplaces.
The campaigns, first detected in June 2025, introduce two previously undocumented malware families, ProSpy and ToSpy. ProSpy masquerades as a Signal “encryption plugin” or an enhanced version of ToTok, while ToSpy exclusively imitates the ToTok app. Both spyware strains are engineered to exfiltrate a wide range of sensitive user data and maintain long-term access to compromised devices.
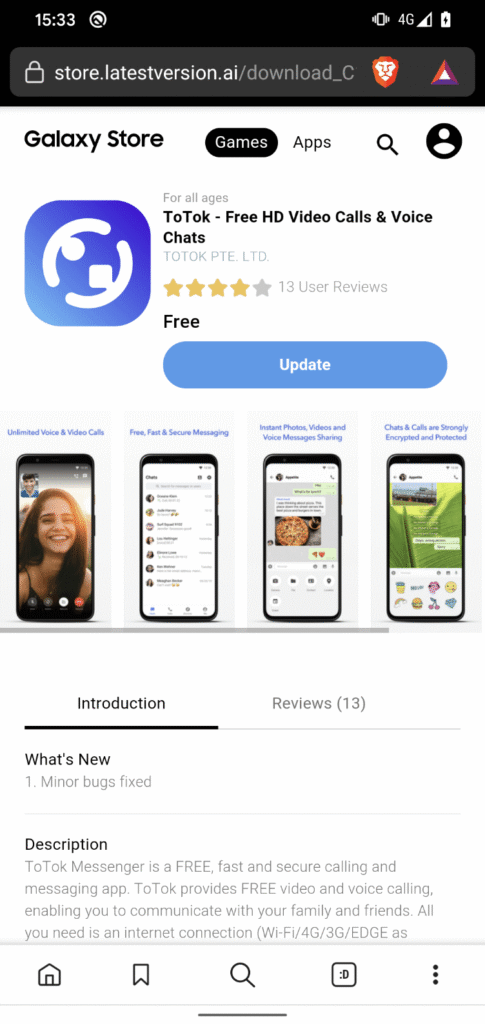
The operation appears to target users in the United Arab Emirates, leveraging the popularity of ToTok in the region and exploiting interest in encrypted communications. The distribution strategy relies on social engineering through malicious websites that mimic trusted sources. For instance, one ToSpy distribution site posed as the Samsung Galaxy Store, misleading users into downloading a trojanized ToTok APK.
ToTok is a UAE-developed voice and messaging app that was removed from both Google Play and Apple's App Store in 2019 amid surveillance concerns. Despite this, it continues to see usage in the region, making it an ideal target for spoofing.
ProSpy campaign
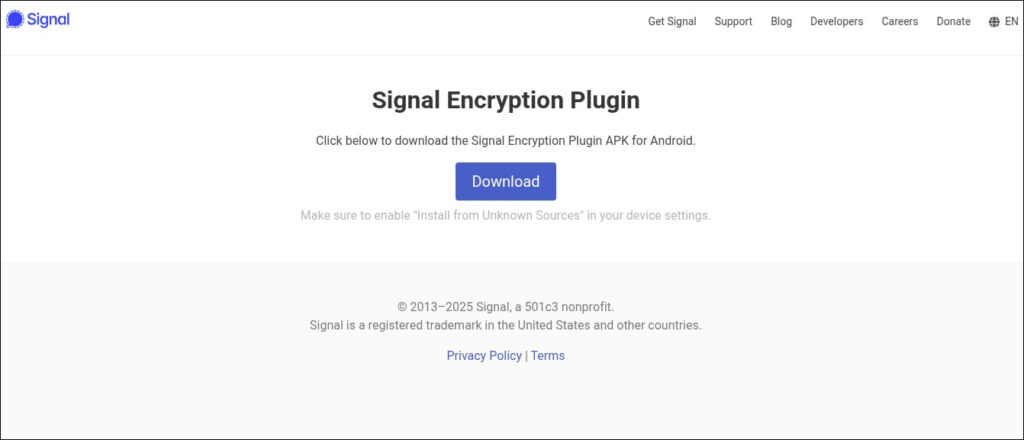
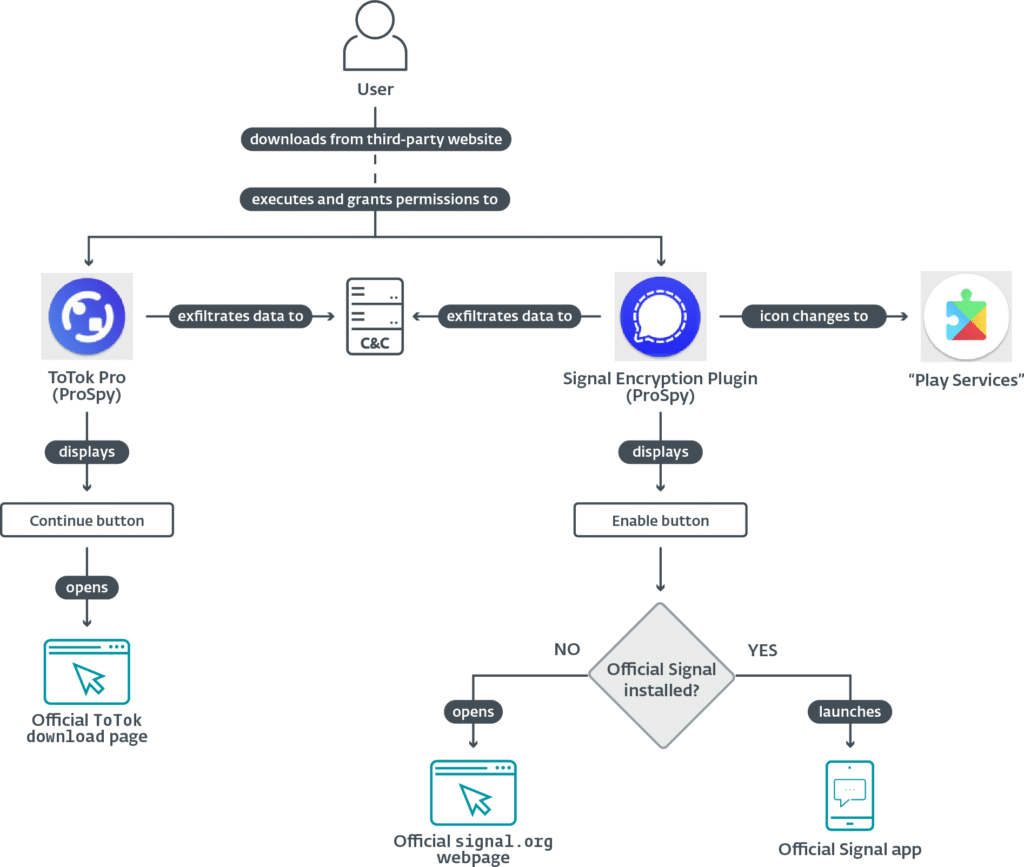
ESET traced ProSpy's origins to at least 2024. The malware has been delivered via three phishing sites that offer fake APKs such as “Signal Encryption Plugin” or “ToTok Pro.” Once installed, ProSpy requests access to SMS, contacts, and storage. If permissions are granted, it begins to collect and exfiltrate data silently.
ESET
The malware is designed to avoid detection and resist removal. After installation, it modifies its icon and name, disguising itself as “Play Services,” to blend in with legitimate system apps. Meanwhile, launching the fake app redirects users to official Signal or ToTok websites, reinforcing the illusion of authenticity.
Exfiltrated data includes:
- Device metadata and IP address
- SMS messages
- Contacts
- Media files and documents
- Archive formats and APKs
- List of installed apps
The data is temporarily stored in local JSON files before being sent to remote command-and-control (C&C) servers.
ESET
ToSpy attacks
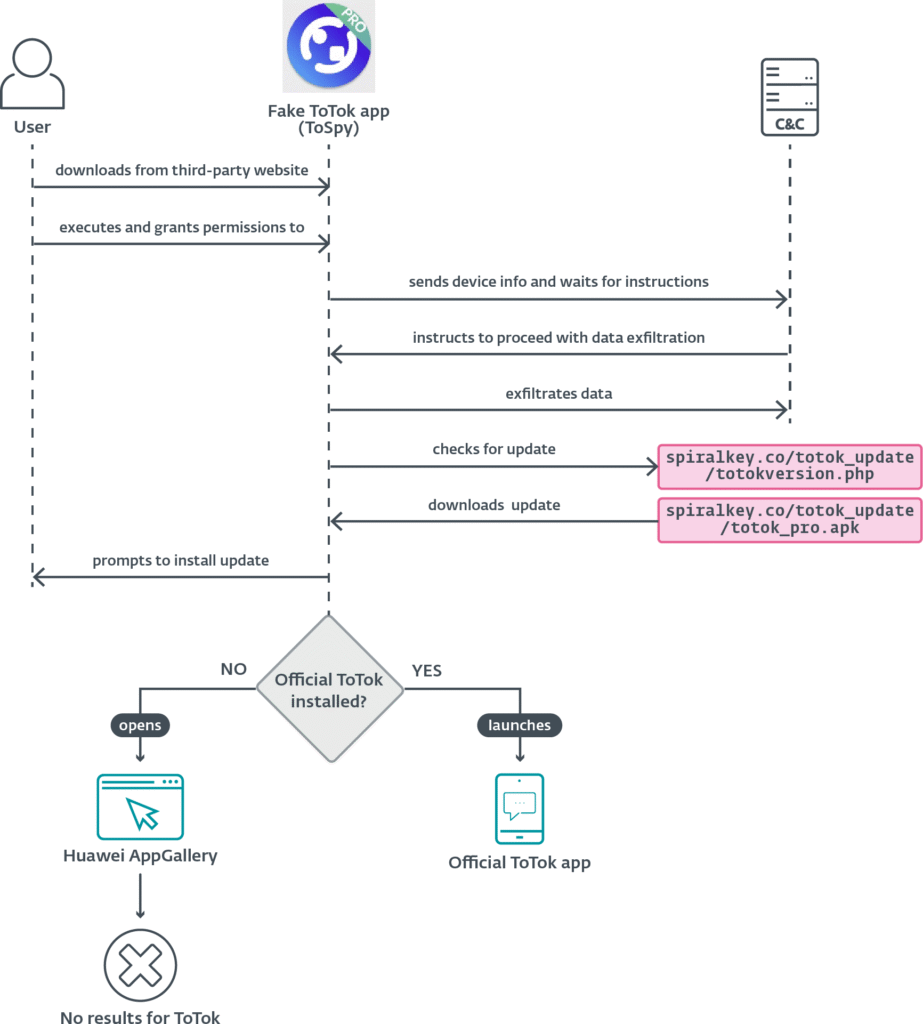
ESET also discovered ToSpy in June 2025 after its telemetry flagged a suspicious APK from a UAE device. The malware family, traced back to mid-2022 based on certificate creation dates and domain registrations, appears to be maintained by a single actor due to consistent coding and certificate reuse.
ESET
Upon installation, the app requests storage and contact permissions and then communicates with a C&C server, awaiting instructions to begin data theft.
Notably, ToSpy seeks out files with the .ttkmbackup extension which are used by ToTok for chat and settings backups, suggesting a targeted interest in extracting conversation history.
Captured data includes contact lists, PDF, DOCX, XLSX, MP3, JPG, and TXT files, as well as device information.
The data is encrypted using AES in CBC mode with a hardcoded key before being sent to the attacker’s infrastructure.
ToSpy also mimics app update behavior by querying a remote server and prompting users to manually install new APKs. While researchers were unable to retrieve these payloads, the functionality implies an update mechanism that can swap in newer spyware versions.
ESET
Both ProSpy and ToSpy employ methods to maintain long-term control over infected devices, including:
- Foreground services that keep the spyware running and harder to kill
- AlarmManager to periodically restart services if terminated
- Broadcast receivers triggered on device boot to reinitialize malicious processes
ESET notes that the ToSpy campaign is ongoing, with multiple C&C servers still live as of October 2025.
The researchers reported their findings to Google, and Play Protect now blocks known variants of ToSpy and ProSpy.







Leave a Reply