
Researchers have uncovered “AISURU,” a DDoS and proxy botnet responsible for generating an unprecedented 11.5 Tbps of attack traffic globally.
Active since at least 2024, AISURU has surged in scale and capability throughout 2025, and is now believed to comprise over 300,000 infected devices, primarily compromised through router exploits.
The report by XLab researchers builds on internal telemetry and insights from an anonymous informant closely familiar with the AISURU threat actors.
AISURU was first identified by XLab in August 2024 during an attack on the game distribution platform for Black Myth: Wukong. Since then, XLab's Cyber Threat Insight and Analysis System (CTIA) has captured thousands of AISURU samples. A pivotal expansion occurred in April 2025, when one of the group's members exploited a vulnerability in a Totolink router firmware update server, redirecting firmware requests to a malicious script hosted at updatetoto[.]tw. This infection campaign, visible in DNS telemetry, caused the domain to spike to a Tranco rank of 672,588 within just one month, correlating with a surge of 100,000+ new bots.
AISURU is run by a trio of actors, namely Snow (botnet developer), Tom (vulnerability researcher and exploit developer), and Forky (responsible for monetization and sales).
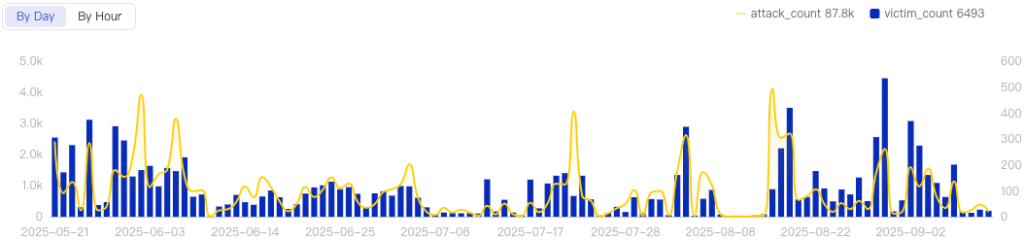
Internal conflicts and ego-driven taunts, often embedded in AISURU's own payloads, have earned the group a notorious reputation even among other botnet operators. Their attacks include record-breaking incidents, such as a May 2025 DDoS on journalist Brian Krebs' personal site, followed by the unprecedented 11.5 Tbps assault in September on the IP 185.211.78.117.
AISURU primarily targets unpatched routers and embedded systems. Notably, the group continues to exploit both N-day and active 0-day vulnerabilities. Some of the impacted vendors include Totolink (via compromised firmware update), Cambium Networks (exploited 0-day in cnPilot routers), Zyxel, D-Link, Linksys, T-Mobile, Realtek, and others.
Its attacks span industries and continents, with victims recorded in China, the US, Germany, the UK, and Hong Kong. The botnet does not appear to discriminate by sector or geography, XLab reports “several hundred” daily targets.
XLab
Technical aspect
AISURU employs a modified version of the RC4 algorithm for both string decryption and communication encryption, using a hardcoded key PJbiNbbeasddDfsc. Technical analysis reveals multiple layers of anti-analysis measures:
Environment detection to evade execution in virtualized or analysis environments
OOM killer evasion via manipulation of /proc/self/oom_score_adj
Process camouflage by renaming itself to system-like binaries such as telnetd or klogd
Persistence and stealth through unconventional methods like retaining .so libraries and renaming binaries
C2 communication uses a customized protocol with support for DDoS attacks, command execution, reverse shells, and proxy control. The infrastructure relies on obfuscated TXT records, XOR encoding, and GRE tunnels over specific IP ranges.
DDoS, proxies, and new revenue streams
The AISURU botnet has shifted from being purely a DDoS tool to a multi-use platform. New versions of the malware include proxy modules, and recent C2 instructions show increasing emphasis on residential proxy functionality. Network speed tests, performed using public Speedtest endpoints, help the botnet identify high-throughput nodes for optimal use in proxy networks.
Such a pivot is consistent with recent underground trends, where botnet operators diversify into anonymity services as a lucrative alternative to high-profile DDoS campaigns. Proxy-capable bots are typically rented out to threat actors requiring low-profile infrastructure for fraud, scraping, or command execution.
To defend against botnets like AISURU, ensure router firmware is updated to its latest version, restrict WAN access, change default admin credentials, and disable unused services on the devices.







Leave a Reply