
North Korea–linked hacking group Kimsuky has launched a spear-phishing campaign against South Korean military institutions, leveraging deepfake ID cards generated by ChatGPT to trick recipients into opening malicious files.
The campaign, detailed by Genians Security Center, marks one of the first documented uses of AI-generated identification in cyber espionage operations.
The attack began on July 17, 2025, when emails spoofed to resemble official military communications were sent with an attached archive labeled Government_ID_Draft.zip. Inside was a shortcut (.lnk) file disguised as a sample ID card. When executed, the file launched obfuscated commands through cmd.exe and PowerShell, downloading both a malicious batch script and a forged identification image. Deepfake analysis software confirmed with 98% certainty that the ID card had been AI-generated.
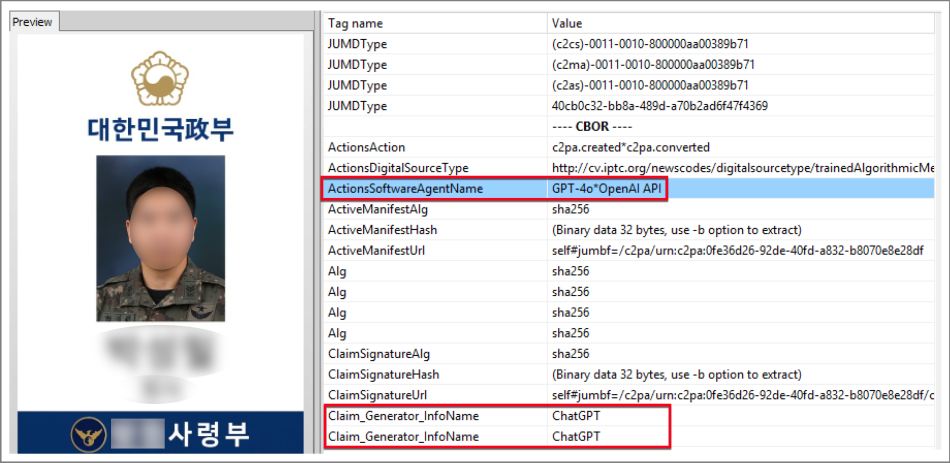
Genians Security Center
Technical analysis revealed extensive obfuscation methods, including string slicing through environment variables, delayed execution to evade sandbox analysis, and the use of deceptive filenames. The downloaded batch scripts connected to a remote command-and-control server, enabling further code execution. Genians noted the tactics strongly resemble earlier Kimsuky spear-phishing waves, including the group’s so-called “ClickFix” operation, which impersonated portal security alerts and government research institutions.
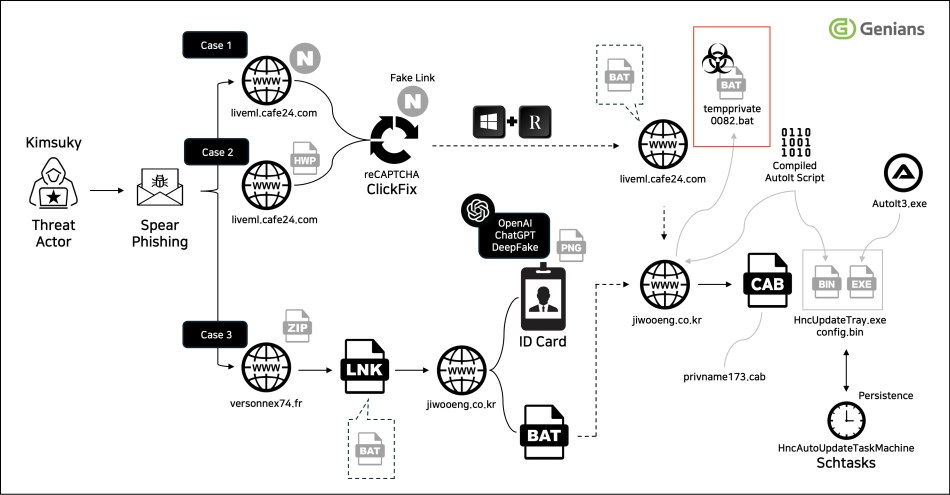
Genians Security Center
The adoption of deepfakes introduces a new layer of social-engineering sophistication. By presenting seemingly authentic government IDs, attackers increase the likelihood of bypassing initial scrutiny by human targets. The operation also underscores the growing weaponization of generative AI in cyberattacks, raising concerns about how identity-based trust systems can be undermined.
Genians warns that organizations, especially in the defense and public sectors, should prepare for more frequent misuse of deepfake imagery. Strengthened email defenses, behavior-based detection tools, and awareness training are recommended to counter increasingly deceptive phishing attempts.







Leave a Reply