
Proton has come under fire for suspending accounts affiliated with Phrack, a long-running hacker publication, after the group published a detailed exposé on North Korean cyber-espionage operations.
The suspension, which Proton attributed to terms of service violations, has ignited controversy over transparency, censorship, and the boundaries of responsible disclosure.
Founded in 1985, Phrack is one of the oldest and most respected hacker zines in circulation. Over the decades, it has been a platform for both theoretical and practical research in infosec, often blurring the lines between underground and academic contributions.
The Phrack article, titled APT Down: The North Korea Files, details a significant breach into systems allegedly operated by Kimsuky, a state-sponsored threat group linked to the North Korean regime. The release included source code, phishing infrastructure, backdoors, stolen credentials, and operational notes purportedly obtained from a Kimsuky-affiliated operator referred to as “KIM.”
According to Phrack, the whistleblower behind the disclosure used Proton Mail accounts solely for the purpose of responsibly notifying affected South Korean institutions. The publication claims that these accounts were first suspended on August 15 and 16, after attempts to contact the Korea Internet & Security Agency (KISA), the Korea Computer Emergency Response Team (KrCERT), the Ministry of Unification, and other governmental bodies.
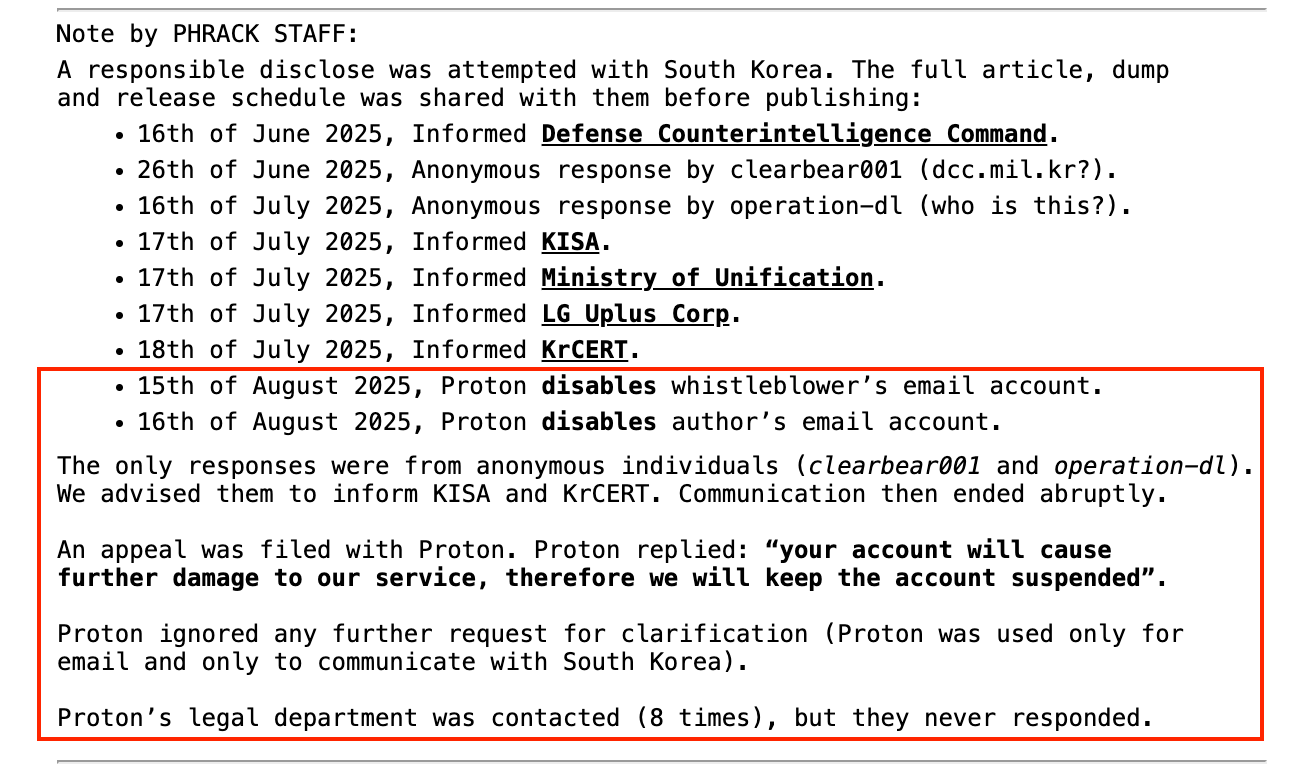
Despite these efforts to disclose the breach, Proton disabled the accounts, citing concerns about potential damage to its service. In its initial response on social media, Proton stated:
“We were alerted by a CERT that certain accounts were being misused by hackers in violation of Proton's terms of service. This led to a cluster of accounts being disabled.”
In a follow-up, Proton CEO Andy Yen further clarified that “hacking is against ToS because it's illegal in Switzerland,” and emphasized the platform's policy of neutrality, stating, “It doesn't matter if you hack for the ‘right' side or ‘wrong' side.”
In an email to CyberInsider after this story was first published, a Proton spokesperson further clarified that the accounts in question were “suspended due to a ToS violation related to multiple incidents of hacking which is illegal under Swiss law which we operate.”
Phrack has categorically denied that any hacking was conducted through Proton's infrastructure, stating that the accounts were only used for whistleblower communication. The group filed an appeal with Proton, which was initially rejected, with the company responding that the account “will cause further damage to our service.” Proton reportedly ignored subsequent attempts for clarification, including eight separate emails to its legal department.
The suspension has triggered criticism from privacy advocates and members of the infosec community, many of whom argue that Proton's actions contradict its stated mission of defending privacy, free speech, and whistleblower protections. Some users noted that Proton's appeal process appears opaque and ineffective, with decisions communicated in vague terms and little recourse for those affected.
In a public message to Proton shared on X, Phrack demanded transparency, asking the company to disclose the specific government request or CERT report that led to the suspension, and to make all government data requests public in full rather than via annual transparency summaries. The publication also called on Proton to create a meaningful appeal process and emphasized the importance of creating a “safe” environment for whistleblowers and researchers.

Although Proton ultimately reinstated two suspended accounts after widespread outcry on social media, Phrack expressed concern about the process and warned that the incident sets a dangerous precedent. “It is concerning that the accounts got disabled in the first place,” Phrack wrote, adding that Proton ignored emails for over three weeks before the group resorted to public pressure.
We reached out to Proton multiple times, requesting clarification on which exact terms of service were violated. As of publication time, the company has not responded.
Update 15 September 2025: Proton has provided a bit more clarification on this topic in a Reddit post here. We have also updated the article to include more clarification from a Proton spokesperson on the situation and reason for the account suspensions.







Protons suspension of Phrack raises serious concerns about privacy and transparency. Its disappointing to see a service known for defender privacy taking such drastic, unclear actions against a group exposing cyber threats. Their response lacks the clarity needed to rebuild trust.
I dislike so much this proton thing that each time I see something revealing their true colors I am very content!
They absolutely do not deserve to be the lead in privacy area.
Awake people are aware and see what they are
and that they recommend migrating to another mail service? I think they violated Proton’s rules or something happened internally that you don’t know to have your accounts suspended. (insult, hacking attempt, knocking down servers, divulging sensitive information. I can’t think of anything else) they would have to look at ProtonMail’s Terms of Use