
ESET researchers have uncovered HybridPetya, a novel strain of ransomware resembling the infamous Petya/NotPetya family, with a dangerous modern twist.
The new ransomware targets UEFI-based systems and leverages a Secure Boot bypass vulnerability (CVE-2024-7344) to disable critical security protections.
The malware was first identified on VirusTotal in February 2025, with samples uploaded from Poland under filenames like notpetyanew.exe. These early clues pointed toward a deliberate link to the original Petya (2016) and NotPetya (2017) malware. While NotPetya was designed purely for destructive purposes, HybridPetya appears to function as actual ransomware, supporting decryption via a victim-specific installation key, a trait more closely aligned with the original Petya.
Modern UEFI attacks
ESET researcher Martin Smolár analyzed multiple HybridPetya variants and noted a significant advancement over its predecessors, which is the ability to compromise modern systems using UEFI firmware. Specifically, HybridPetya installs a malicious EFI application onto the EFI System Partition to execute its payload during the early stages of system boot.
ESET
Petya and NotPetya were known for overwriting the Master File Table (MFT) on NTFS partitions, making file recovery nearly impossible. HybridPetya continues this approach but introduces greater technical depth by deploying a UEFI-compatible bootkit capable of running outside the traditional OS environment.
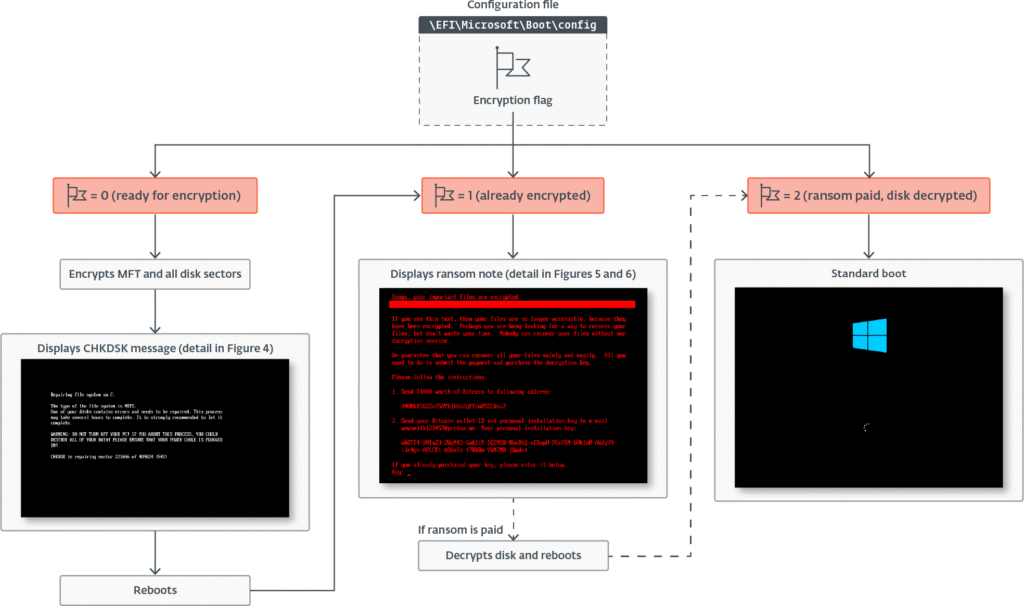
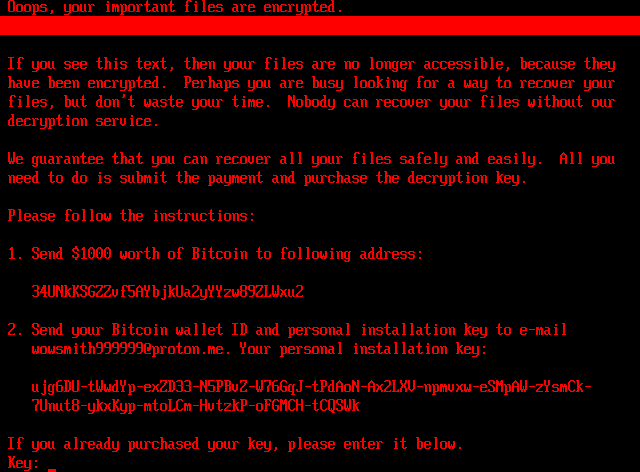
The ransomware initiates by dropping a configuration file (\EFI\Microsoft\Boot\config) containing encryption keys and status flags. It then encrypts the MFT using the Salsa20 algorithm and displays a fake CHKDSK screen to obscure its malicious activity. Once encryption is complete, the system reboots and presents a ransom note during pre-boot execution, requesting payment in Bitcoin and providing an email address for victim contact.
ESET
HybridPetya variants use different contact emails depending on the deployment method, including wowsmith999999@proton[.]me and wowsmith1234567@proton[.]me. While both variants share the same Bitcoin address, they appear to stem from distinct build chains or operators.
HybridPetya exploits CVE-2024-7344, a vulnerability in UEFI Secure Boot that was disclosed by ESET earlier in 2025. This flaw allows a malicious cloak.dat file to be loaded by a signed but revoked Microsoft EFI binary (reloader.efi), bypassing integrity checks and enabling unsigned code to run at boot.
ESET has seen no evidence of HybridPetya's widespread deployment in the wild, nor any indication of the aggressive worm-like propagation used by NotPetya. This suggests that HybridPetya may currently be in a proof-of-concept stage or limited to targeted testing by its authors, who could be either cybercriminals or researchers.






Leave a Reply