
Apple has introduced Memory Integrity Enforcement (MIE), a major security upgrade that brings always-on, hardware-backed memory safety to the iPhone 17 and iPhone Air.
MIE integrates Apple’s custom silicon with OS-level protections to block entire classes of memory corruption vulnerabilities, key ingredients in many advanced spyware attacks.
The system is the result of a five-year collaboration across Apple’s silicon, OS, and security teams. Apple describes MIE as the most significant memory safety enhancement ever shipped in a consumer operating system.
MIE builds on existing defenses like type-aware memory allocators (kalloc_type, xzone malloc), Pointer Authentication Codes (PAC), and now, the Enhanced Memory Tagging Extension (EMTE).
Apple
Co-developed with Arm, EMTE improves on the original MTE design by tagging every memory allocation with a secret. The hardware enforces synchronous tag checking, so any mismatch causes the process to crash immediately. This approach eliminates exploitable timing windows that attackers could use to their advantage.
Unlike Android’s opt-in MTE, MIE is always-on and deeply integrated into both the A19/A19 Pro chips and iOS, enabling protection across the kernel and over 70 userland processes without compromising performance.
Apple
Thwarting spyware attacks
Memory corruption bugs like use-after-free and buffer overflows remain core techniques in advanced exploits, especially in spyware targeting iOS, Android, and Windows. These bugs are reusable and often chained together to achieve full system compromise.
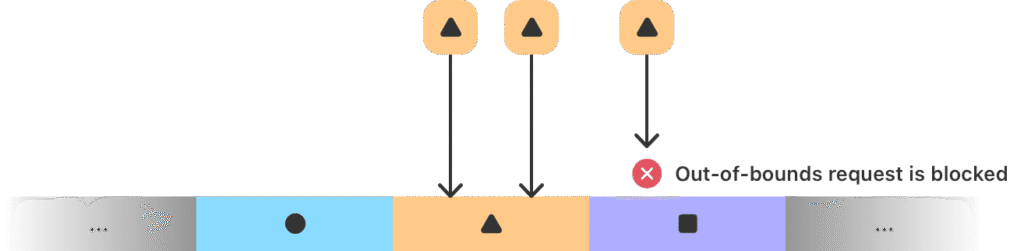
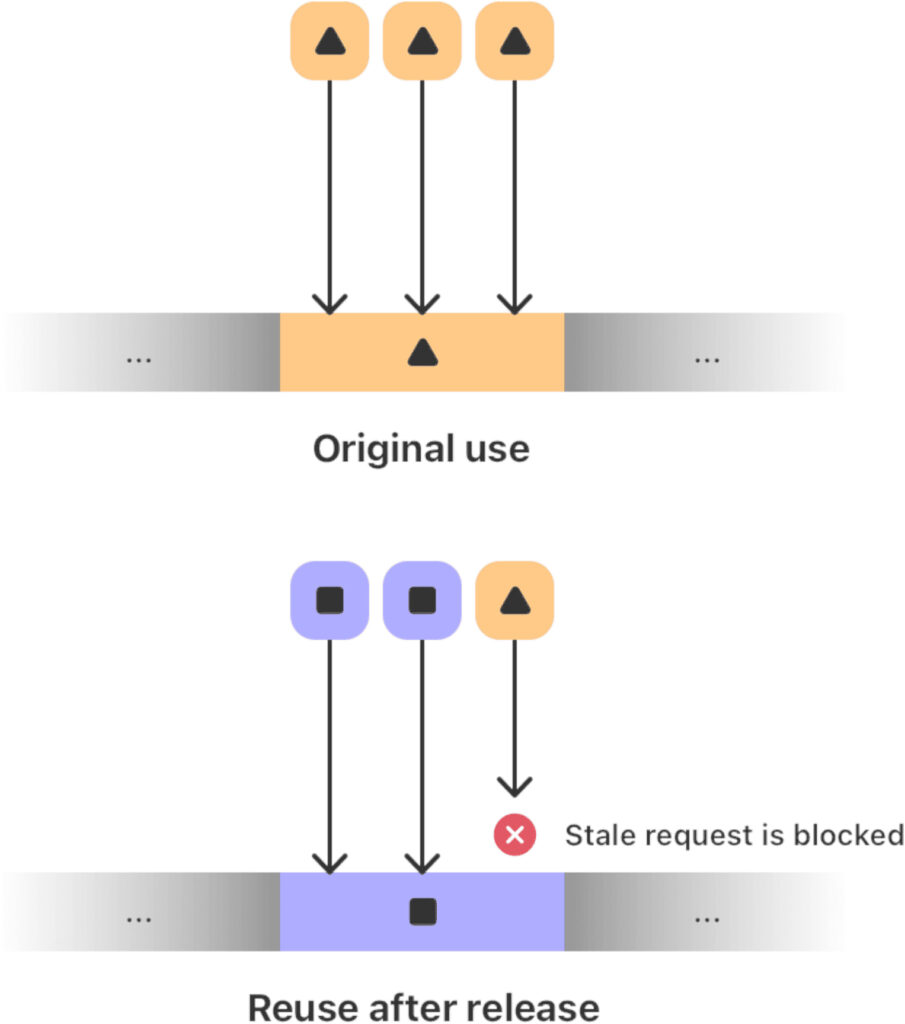
Apple’s type-aware memory allocators already isolate allocations by type, making many such attacks harder. EMTE closes remaining gaps by tagging small allocations within the same page. For example, if a memory block is reused after being freed, the new tag won’t match the old one, effectively blocking use-after-free attempts.
MIE also addresses speculative execution attacks, including Spectre Variant 1. Apple prevents speculative leakage of memory tags by combining pointer offset clamping (to under 4GB), special poisoning patterns (0x2BAD), and virtual address layout tricks. This forces attackers to navigate type isolation even on speculative paths, something previously deemed too costly for consumer-grade defenses.
Apple makes clear that MIE is aimed not at common malware, but at mercenary spyware, expensive surveillance tools used by nation-states to target high-risk individuals. These toolkits often rely on memory corruption vulnerabilities to gain persistence and control.
Third-party apps like browsers and messaging platforms can opt into MIE protections using Xcode’s Enhanced Security setting. This helps close popular entry points used in real-world attacks.
Unlike Google’s MTE implementation, available only to at-risk Android users and limited in scope, Apple’s MIE is system-wide, always-on, and purpose-built for live deployment.
Apple’s internal red team spent years testing MIE against real-world exploit chains, reporting that none survived. Even where partial primitives remained, they were too weak or unreliable to support full compromise. By fundamentally restricting attacker options, MIE disrupts long-standing exploitation tactics and dramatically raises the cost of developing effective attacks.







Leave a Reply