
A threat actor has executed what is now considered the most widespread supply chain compromise in the history of the npm ecosystem, affecting 18 widely-used JavaScript packages, including chalk, debug, and ansi-styles, with a combined total of over 2 billion weekly downloads.
The breach was discovered on September 8, 2025, at 13:16 UTC, by threat intel systems at Aikido Security. Security researcher Charlie Eriksen was among the first to publicly flag the compromise, warning the affected maintainer, Josh Junon (also known as Qix), that their npm account was pushing malicious updates. Within an hour, multiple compromised versions had already propagated across the ecosystem, with Junon confirming he had fallen victim to a phishing email spoofing support@npmjs.help and lost access to his account due to a deceptive 2FA reset prompt.
The attacker modified 18 high-profile packages to include a stealthy, highly obfuscated payload targeting cryptocurrency users. The code hooks into browser environments, injecting itself into fetch, XMLHttpRequest, and wallet APIs like window.ethereum, to intercept and manipulate both web traffic and crypto wallet interactions.
Aikido
Aikido’s reverse engineering of the payload revealed that the malware executes the following behaviors:
- Monitors for Wallet Activity: It detects Ethereum, Solana, Bitcoin, Tron, Litecoin, and Bitcoin Cash wallet addresses in network traffic and app payloads.
- Rewrites Transaction Targets: It substitutes legitimate addresses with attacker-controlled ones using string similarity logic, making the altered values appear nearly identical to the original.
- Alters Unsigned Transactions: The script hijacks and silently modifies outgoing transaction parameters, such as recipients, approval amounts, and allowances, before the user signs them.
- Evades Detection: It minimizes its footprint in UI-visible areas, ensuring transaction interfaces appear unchanged while covertly altering what’s actually signed and sent.
This allows the attacker to siphon funds by exploiting the moment between a user confirming a transaction and its cryptographic signing, subtly redirecting crypto transfers and approvals without alerting the user.
Affected packages
The breach impacted a staggering number of packages, many of which are dependencies in countless downstream projects. Key compromised packages include:
- chalk (299.99 million weekly downloads)
- debug (357.6 million)
- ansi-styles (371.41 million)
- ansi-regex (243.64 million)
- supports-color (287.1 million)
- strip-ansi (261.17 million)
- wrap-ansi, color-convert, color-name, error-ex, and others
Together, these libraries form the backbone of terminal output formatting in the JavaScript ecosystem and are direct or transitive dependencies for thousands of projects, CI pipelines, and developer tools.
Attribution and maintainer response
The compromised packages were all linked to Josh Junon, a well-known open-source maintainer with a long history of stewarding popular Node.js utilities like chalk and debug. In a public statement posted on Bluesky, Junon acknowledged the breach and expressed regret for being duped by a convincingly spoofed 2FA reset email during a particularly stressful week.
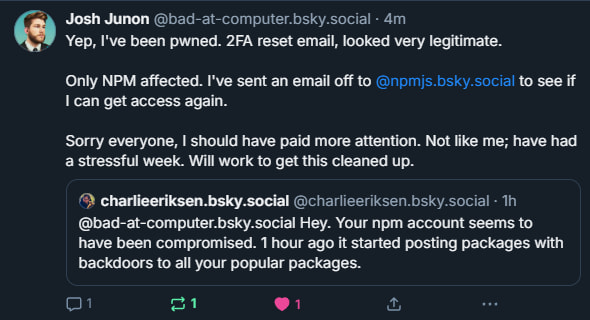
Junon confirmed that only the npm account was affected and has since contacted the npm security team in an attempt to regain control. Prior to being locked out, he was able to delete several compromised versions of the packages. However, Aikido noted that as of their last scan, some of the infected packages remained live on the npm registry.







Leave a Reply