
Google's Threat Intelligence Group (GTIG) has exposed a stealthy and technically advanced cyber-espionage campaign by Chinese state-aligned threat actor UNC6384.
The campaign, identified in March 2025, targets diplomatic personnel in Southeast Asia and leverages a hijacked web traffic mechanism to deliver memory-only malware designed to exfiltrate sensitive information.
According to Google’s report, the attackers used a deceptive chain involving a captive portal redirect and adversary-in-the-middle (AitM) tactics to install malware disguised as legitimate plugin updates. The final payload, an in-memory backdoor dubbed SOGU.SEC, is deployed through a complex multi-stage process, culminating in covert remote access for the attackers. The overall activity has been attributed to UNC6384, a group linked to the broader PRC-affiliated TEMP.Hex (also known as Mustang Panda).
Captive portal redirection
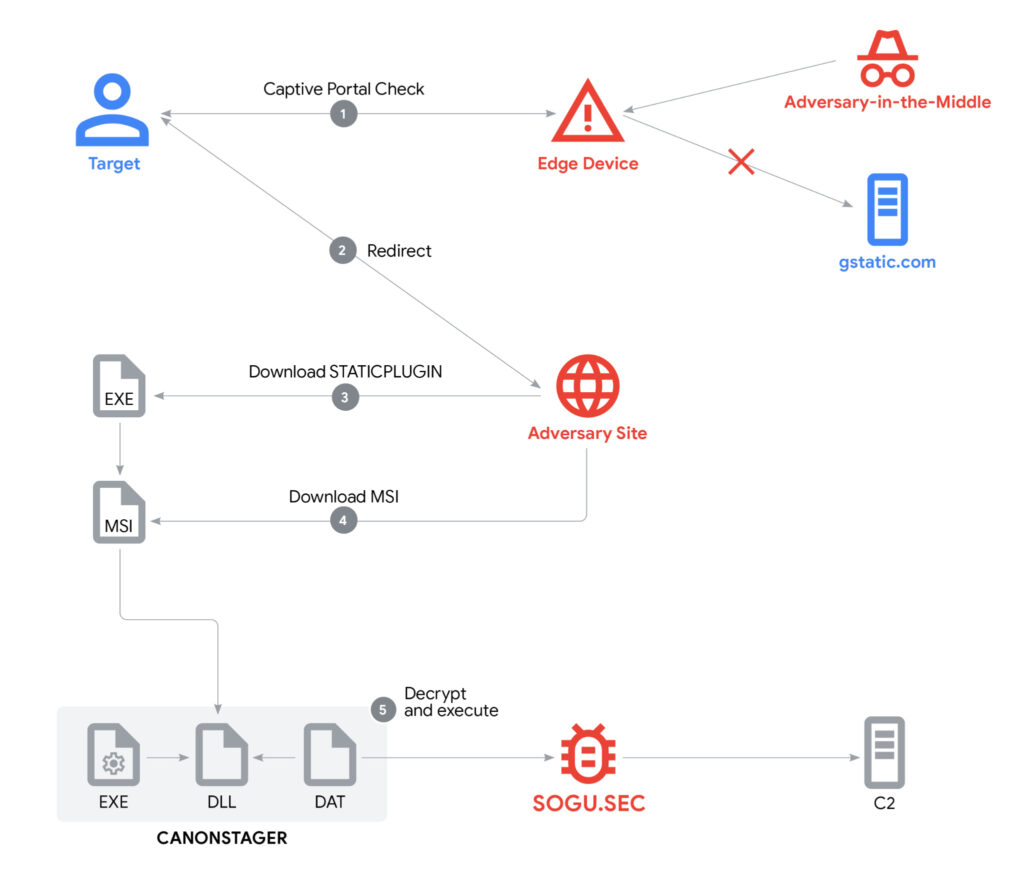
The attack starts when a target’s browser attempts to detect internet connectivity, using the standard Chrome captive portal check via http://www.gstatic.com/generate_204. The attackers intercept this request and redirect it to a fake landing page hosted on mediareleaseupdates[.]com, a domain masquerading as a legitimate plugin update service. This infrastructure was found hosted on IP 103.79.120[.]72, with HTTPS support and a valid certificate issued by Let’s Encrypt, an approach aimed at reducing suspicion from users and security tools.
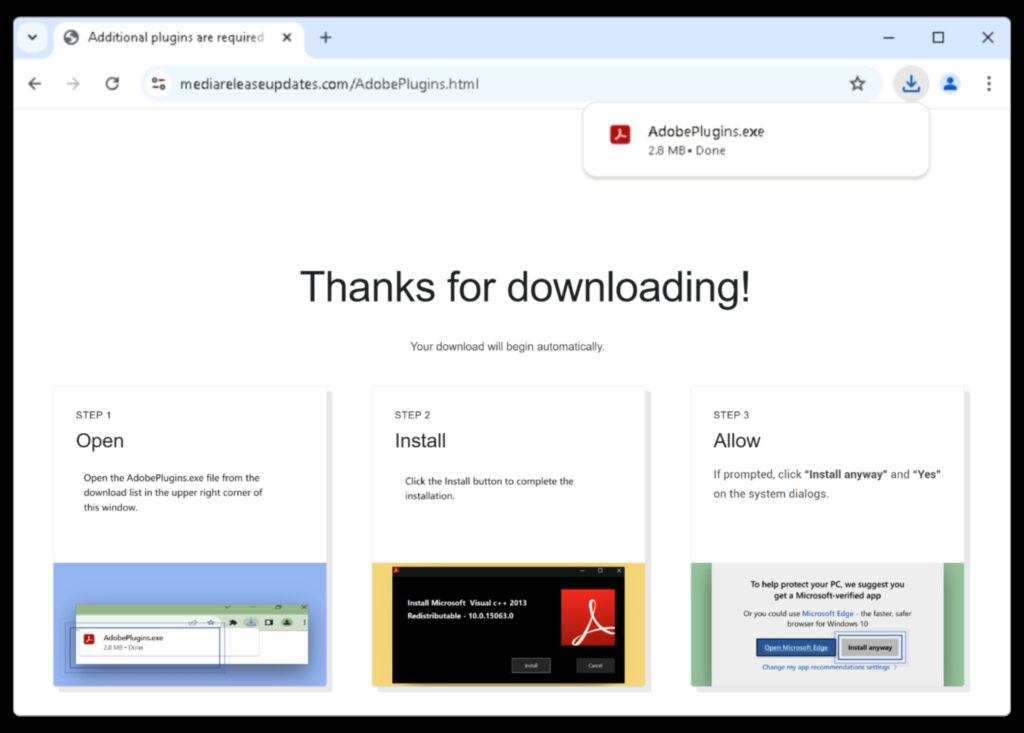
The redirect page tricks users into downloading a file named AdobePlugins.exe, which is in fact a first-stage downloader tracked by GTIG as STATICPLUGIN. The file was digitally signed using a certificate issued to Chengdu Nuoxin Times Technology Co., Ltd, giving it the appearance of authenticity. Once executed, STATICPLUGIN downloads an MSI package, unpacks three files, and triggers a DLL side-loading routine that runs the second-stage launcher CANONSTAGER.
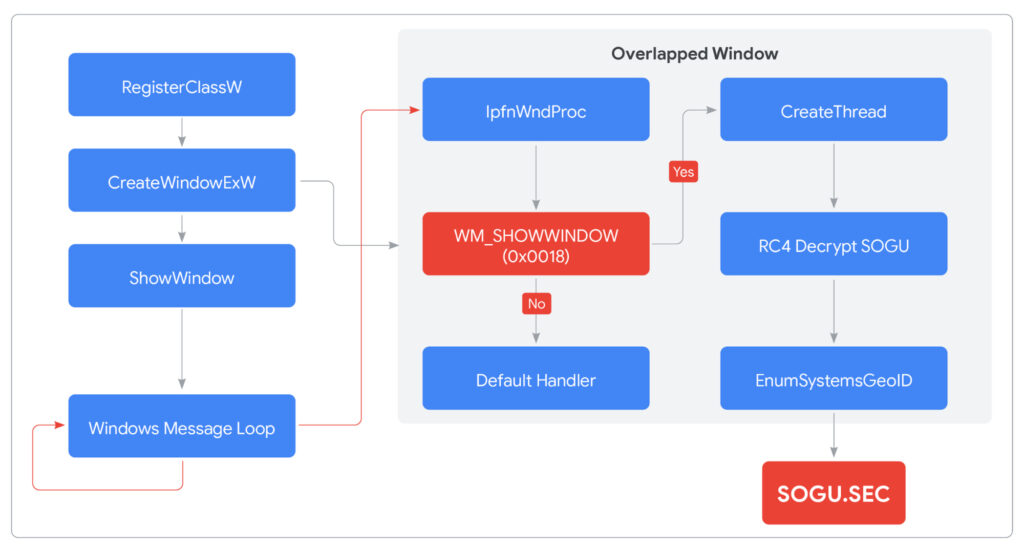
CANONSTAGER, embedded within cnmpaui.dll, is a stealthy launcher that uses unconventional execution methods to avoid detection. The launcher exploits Thread Local Storage (TLS) and custom API hashing to hide its system interactions, then creates a hidden window and abuses Windows message queues to indirectly execute its payload. This indirect control flow culminates in the decryption and in-memory execution of SOGU.SEC, a variant of the PlugX malware family.
SOGU.SEC, which has no persistent file on disk, provides remote operators with command shell access, file exfiltration capabilities, and system reconnaissance functions. In this campaign, it communicated with a command and control (C2) server at IP address 166.88.2[.]90 over HTTPS, using a crafted User-Agent string to blend in with legitimate browser traffic.
Signs of Chinese involvement
UNC6384 is a China-linked espionage group with a history of targeting Southeast Asian governmental entities. The group is known for deploying SOGU variants and conducting operations in alignment with the strategic priorities of the People's Republic of China. GTIG’s attribution to UNC6384 is supported by technical overlaps with TEMP.Hex, shared infrastructure, and repeated use of similar techniques, including DLL side-loading, fake update lures, and memory-only payloads.
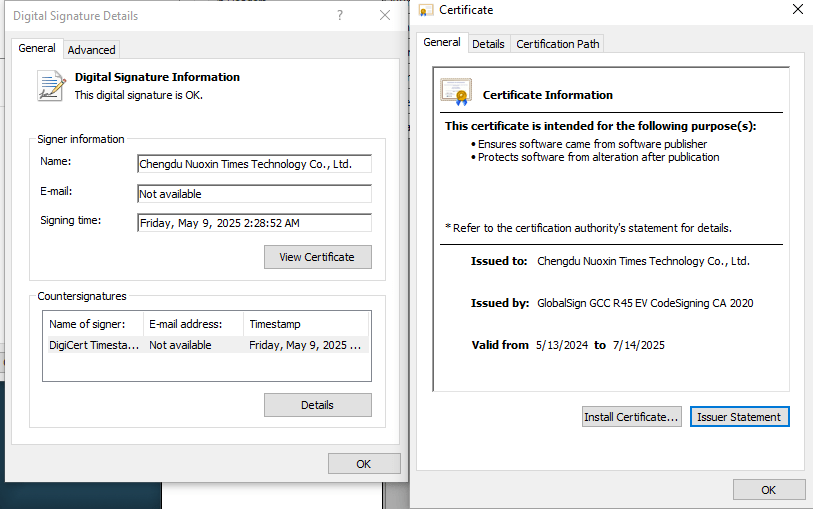
Google also revealed that Chengdu Nuoxin Times Technology Co., Ltd has been the source of at least 25 malware samples tied to PRC-nexus actors since 2023. While it remains unclear whether the firm is complicit or compromised, their certificates have been repeatedly used to sign malicious executables.







Leave a Reply