
Akamai's Security Intelligence and Response Team (SIRT) has uncovered a new attack vector involving the Common UNIX Printing System (CUPS), which can be exploited to launch large-scale distributed denial-of-service (DDoS) attacks.
The new DDoS vector emerges on the heels of RCE vulnerabilities disclosed in late September by security researcher Simone Margaritelli (aka @evilsocket). Collectively, these issues highlight the risk posed by outdated versions of CUPS, many of which have not been updated since 2007, leaving a large attack surface open to threat actors.
Massive DDoS potential uncovered
The new findings indicate that an attacker could weaponize the CUPS system to flood a target with traffic, amplifying the attack by leveraging vulnerable CUPS servers exposed to the internet. Akamai researchers estimate that over 198,000 devices running CUPS are exposed online, with approximately 58,000 susceptible to this DDoS amplification abuse.
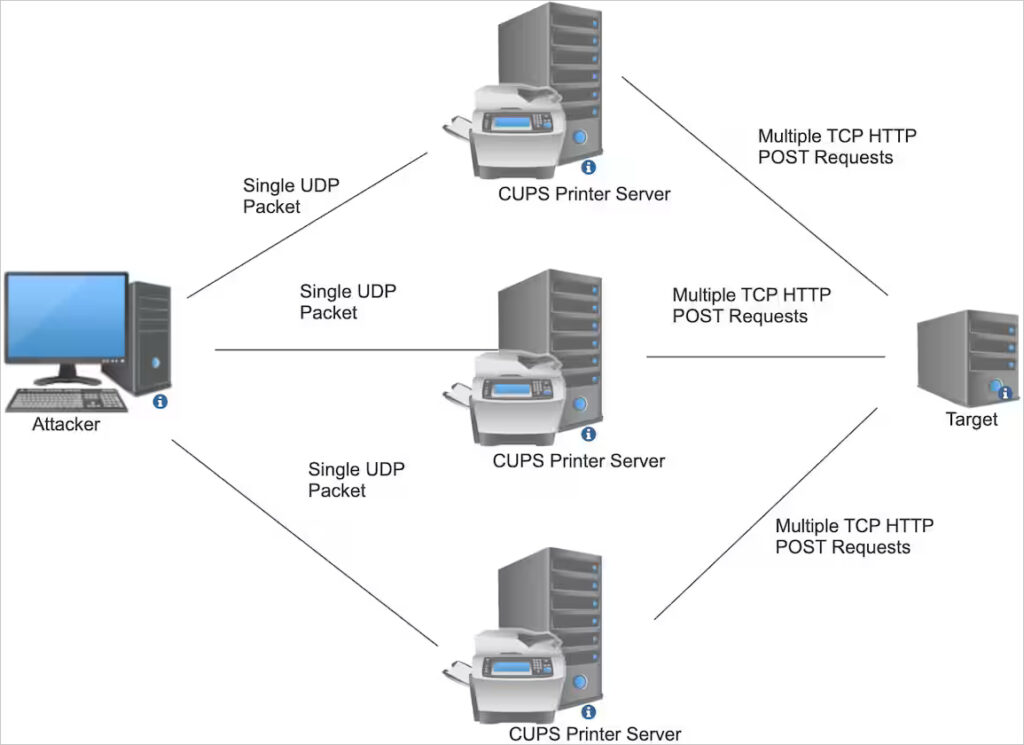
The attack is initiated by sending a single packet to an exposed and vulnerable CUPS service. The service then generates an Internet Printing Protocol (IPP) request, which can be directed to any target of the attacker's choosing. These requests consume bandwidth and resources from both the host system running CUPS and the intended victim, potentially overwhelming the target with an amplified data stream.
The attack leverages multiple vulnerabilities in different components of CUPS:
- CVE-2024-47176: A flaw in cups-browsed that allows requests to attacker-controlled addresses.
- CVE-2024-47076: A vulnerability in libcupsfilters, which fails to validate or sanitize IPP attributes.
- CVE-2024-47175: A vulnerability in libppd that does not sanitize inputs and writes them to temporary files.
- CVE-2024-47177: An arbitrary command execution flaw in cups-filters.
While initial analysis focused on the potential for remote code execution (RCE), Akamai identified that these vulnerabilities also allow for DDoS amplification attacks, whereby a CUPS server generates large IPP/HTTP requests to a specified target, consuming network resources and potentially causing service disruption. In fact, Akamai's research gives a far more realistic and attainable attack vector, which proves that the importance of the recently uncovered flaws shouldn't be downplayed.
Attack flow and potential impact
An attacker sends a single crafted UDP packet to a vulnerable CUPS instance, specifying a target to which the CUPS server should send its IPP request. This packet triggers CUPS to send a larger HTTP request containing payloads controlled by the attacker. The padding in these payloads can be significant, causing further strain on the target's network.
Some CUPS servers exhibit behavior where they fall into an “infinite loop,” generating thousands of outgoing requests in response to a single trigger packet. In a worst-case scenario, the attack could cause an “infinite amplification,” severely impacting the targeted system.
Akamai's research shows that roughly 34% of exposed CUPS servers can be abused for DDoS attacks. The amplification rate is significant — with a single 30-byte probe resulting in an average of 18,000 bytes of traffic sent to the target, creating a 600x amplification factor. In instances where the payload is maximally padded, the amplification rate drops to 104x, but the bandwidth consumption rises to nearly 6 times the minimally viable payload, making the attack more taxing on the target's network and resources.
Akamai
If all vulnerable CUPS hosts were exploited in a coordinated attack, the total flood of traffic could reach up to 1 GB from a single UDP packet in a minimally padded scenario or up to 6 GB in a maximally padded scenario. Such an attack would overwhelm the target with an estimated 2.6 million TCP connections and HTTP requests.
Akamai
Mitigation tips
Defenders can mitigate this attack vector by firewalling the CUPS service ports (UDP/631) from external access, updating to the latest version of CUPS, or disabling the cups-browsed service entirely if not required.
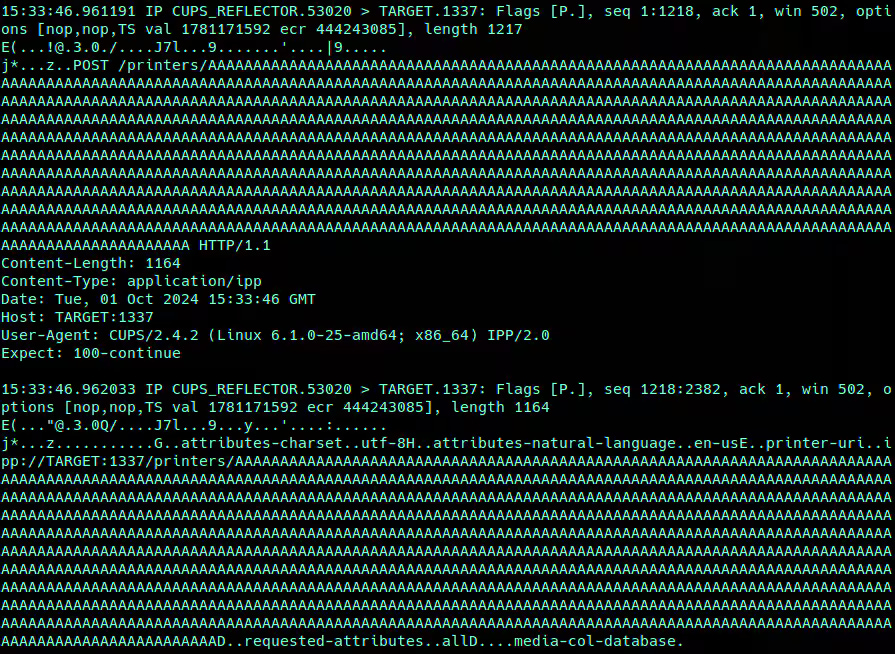
Monitoring traffic for signs of DDoS abuse, such as HTTP requests beginning with POST /printers/ or unique CUPS/[VERSION] user-agent strings, can help detect and filter out malicious traffic. A provided Snort rule can further assist in identifying CUPS-reflected DDoS IPP requests over plaintext sockets.






Leave a Reply