
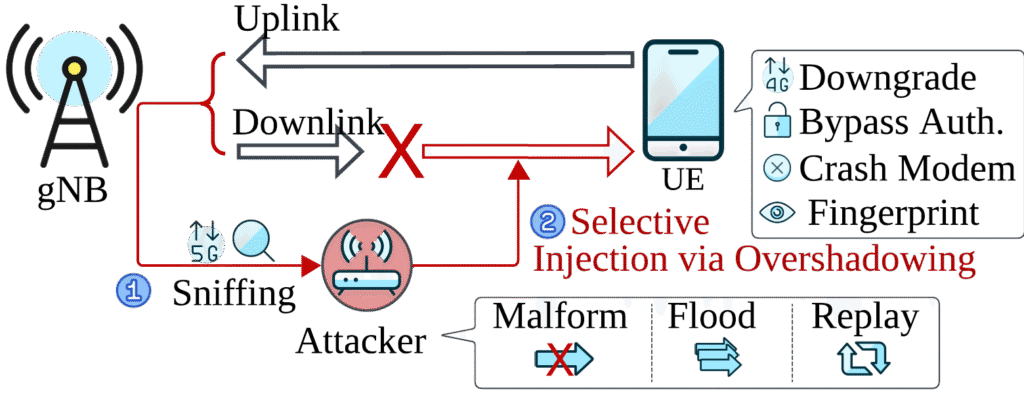
A powerful open-source framework called SNI5GECT can sniff and inject messages into pre-authentication 5G NR communication without relying on rogue base stations.
The tool, which was developed by researchers from the Singapore University of Technology and presented at the 34th USENIX Security Symposium, enables practical exploitation of vulnerabilities in commercial 5G devices, including denial-of-service, connection downgrades, and identity leaks.
The framework addresses the limitations of existing 5G attack models that rely on rogue gNBs (base stations), which are complex to deploy, easier to detect, and require forcing user equipment (UE) to connect to them. Instead, SNI5GECT operates as a passive third party, silently monitoring 5G traffic and injecting messages at specific protocol states using a software-defined radio (SDR) setup. It is accompanied by a GitHub release providing the full 5G Sniffer and Downlink Injector Framework, offering researchers and defenders a practical testbed for real-world 5G attack analysis.
How SNI5GECT works
SNI5GECT targets the pre-authentication window, the critical moment during initial 5G connection when control-plane messages are unencrypted. This window, triggered during common scenarios like exiting airplane mode or emerging from tunnels, allows attackers to eavesdrop and manipulate protocol flows without knowing UE credentials.
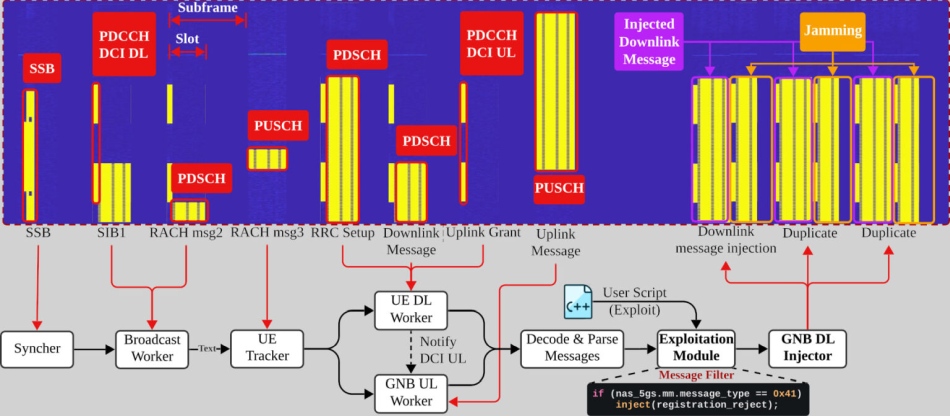
The system comprises several components:
- Syncher: Aligns with the target 5G cell, decodes the Master Information Block (MIB), and maintains subframe synchronization.
- Broadcast Worker: Extracts and decodes the SIB1 (System Information Block), then monitors for new UEs via the Random Access Response (RAR) message.
- UETracker: Actively tracks each detected UE through dedicated downlink and uplink sniffers, determines protocol state, and manages attack payload injection.
- GNB DL Injector: Crafts and transmits spoofed downlink messages that mimic legitimate gNB transmissions, carefully timed to avoid CRC rejections or collision with actual base station traffic.
By sniffing both downlink (PDSCH) and uplink (PUSCH) traffic and decoding the control channels (PDCCH), SNI5GECT enables precise, stateful injection, whether during Registration, RRC Setup, or NAS procedures. It uses clever timing adjustments via Timing Advance Command (TAC) values to decode misaligned uplink messages and inject payloads effectively up to 20 meters away.
Attacks and capabilities
SNI5GECT was tested on five commercial 5G devices, namely OnePlus Nord CE 2, Huawei P40 Pro, Google Pixel 7, Samsung Galaxy S22, and a Fibocom USB modem, with both open-source (srsRAN) and commercial (Effnet) base stations.
In the researchers’ evaluation, the sniffing accuracy surpassed 80% uplink/downlink coverage with >95% for downlink alone. Injection success reached a rate between 70% and 90%, increasing with message duplication and precise calibration.
Attack categories presented in the paper include:
- One-Shot Crashes (via malformed RRC/RLC): Reproduced 5Ghoul vulnerabilities (e.g., CVE-2023-20702).
- Downgrade Attacks: Leveraged a single Registration Reject to force UEs onto 4G.
- SUCI Catching: Injected Identity Request messages to capture encrypted identifiers.
- Multi-Stage Downgrades: Discovered a new replay-based downgrade attack acknowledged by GSMA (CVD-2024-0096), using forged Authentication Request messages to trigger blacklisting of the 5G cell.
The replay-based downgrade attack manipulates the T3520 timer in UEs by sending a spoofed Authentication Request with an invalid sequence number. If the attack is repeated, the UE may blacklist the 5G cell and permanently fall back to a 4G network, even ignoring subsequent attempts by the gNB to reconnect.
In one demonstration, researchers successfully forced downgrade to 4G, then used a rogue 4G base station to perform an IMSI-capture attack, undermining 5G’s privacy guarantees.
Real-world implications
Unlike lab-only attacks, SNI5GECT works against commercial gNBs and at realistic distances. It does not rely on GPSDO for timing precision, instead using iterative delay calibration to align message injection. With hardware like USRP B210 SDRs and the srsRAN stack, the team ran successful attacks in practical environments, showcasing reproducibility and scalability.
Their comparison with other frameworks (NR-Scope, Falcon, AdaptOver) shows that SNI5GECT uniquely combines passive sniffing with arbitrary, state-aware message injection, across both uplink and downlink. The entire stack is built in C++ on top of srsRAN, with ≈10,950 lines of code and integration with the WDissector protocol analyzer.
For researchers and defenders, SNI5GECT provides an open and extensible testbed to evaluate the security posture of 5G deployments. All assets were made freely available through this GitHub repository.






Leave a Reply