
TP-Link is advising users of its widely deployed TL-WR940N and TL-WR841N routers to replace the devices, as the company will not issue a fix for a high-severity buffer overflow vulnerability impacting both models.
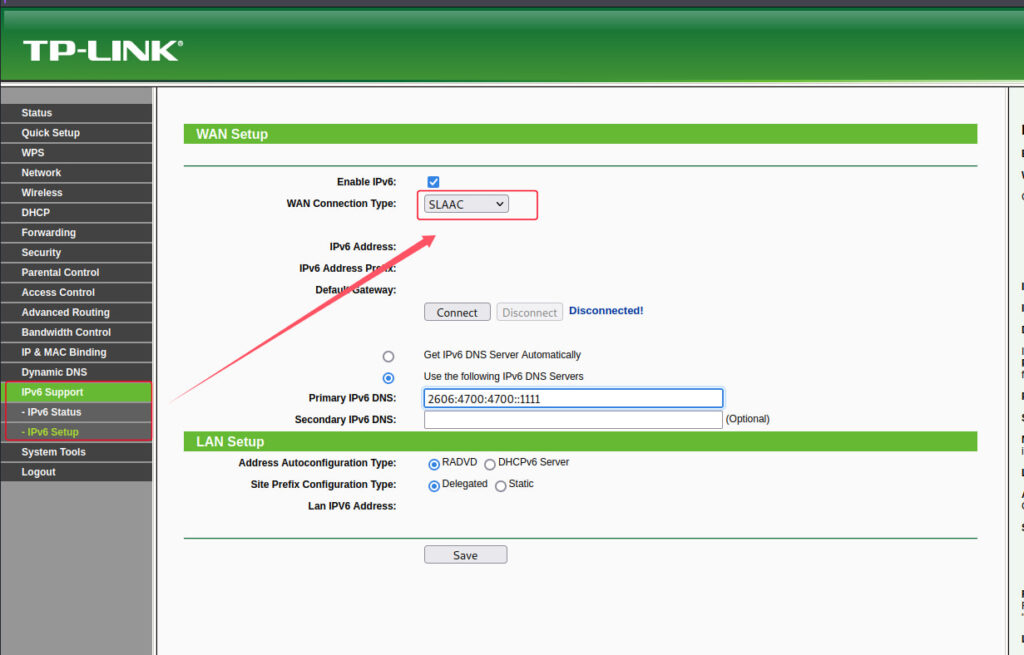
The issue, tracked as CVE-2025-6151, was publicly disclosed by security researcher WhereisDoujo in late May 2025. It affects the TL-WR940N V4 and TL-WR841N V11 routers and stems from a buffer overflow in the /userRpm/WanSlaacCfgRpm.htm component. Specifically, the flaw is triggered by the dnsserver1 parameter being processed without adequate bounds checking via an unsafe strcpy() call in the HTTP daemon's sub_44E6E0 function. The vulnerability can be remotely exploited by an authenticated attacker to crash the device's HTTP service, resulting in a denial-of-service condition.
WhereisDoujo | GitHub
The TL-WR940N and TL-WR841N are among TP-Link's most widely distributed consumer-grade routers, particularly popular in home and small office networks due to their affordability and ease of setup. The TL-WR940N V4, released around 2014, and the TL-WR841N V11, released circa 2016, have since reached end-of-life (EOL) status, meaning they no longer receive firmware updates or security support from TP-Link.
In its official security advisory published yesterday, TP-Link acknowledged the flaw and assigned it a CVSS v4.0 base score of 8.2 (High), citing its remote exploitability and low attack complexity. The advisory confirms that no patch will be provided due to the EOL status of the devices, and instead urges users to upgrade to newer models that still receive firmware updates.
The vulnerability was discovered through static analysis of the router's firmware using reverse engineering tools like IDA Pro. Researcher WhereisDoujo demonstrated the exploitability of the flaw by sending a specially crafted HTTP request containing an overly long dnsserver1 value, which led to a crash and loss of router functionality, requiring a manual reset or reboot depending on the model.
While the exploit requires prior authentication, its presence in the web management interface, commonly exposed on internal networks, could still pose a significant risk in environments where router credentials are weak, reused, or compromised through other means. Once exploited, the crash of the HTTP service disrupts device management and connectivity, potentially affecting all users relying on the router for internet access.
TP-Link's recommendation is unambiguous: affected users should replace the TL-WR940N V4 and TL-WR841N V11 with newer, supported hardware. The company disclaims any responsibility for the consequences of continuing to use the vulnerable devices.
If upgrading to a supported model is impossible, ensure the router's remote web management interface is disabled to limit exposure, change the default administrator credentials, and place the legacy devices on a separate subnet, isolating them from valuable data.







I’ve used TP-Link products. Their is not much of a gap between customer support and the engineers, at least in years past. They’re responsive. I’d recommend TP-Link, generally. Although that was with China TP-Link, and not the current US one.
But as far as I can tell.,they are consumer grade products; they do have a decent, informative security page: https://www.tp-link.com/us/landing/security-commitment/.
But what prosumer and small enterprise routers should we be using, CyberInsider? I don’t know, and like many, not wanting to buy routers all the time, my router is old with open vulnerabilities. It would be nice to know if I could buy a router with a long support lifecycle that doesn’t require an enterprise sysadmin. The issue with the article is predicated upon huge numbers of people using really old routers. You guys should help fix that with router product reviews and recommendations; buying a router can be enough of a black box for people here, much less normies. Thanks.
Can you show pictures of the routers? Thanks