
A coordinated international crackdown has dealt a major blow to NoName057(16), a pro-Russian hacktivist group responsible for thousands of DDoS attacks across Europe and North America since the onset of Russia’s full-scale war in Ukraine.
The multinational operation, codenamed Eastwood, involved law enforcement and judicial authorities from 17 countries, supported by Europol, Eurojust, ENISA, and private cybersecurity partners.
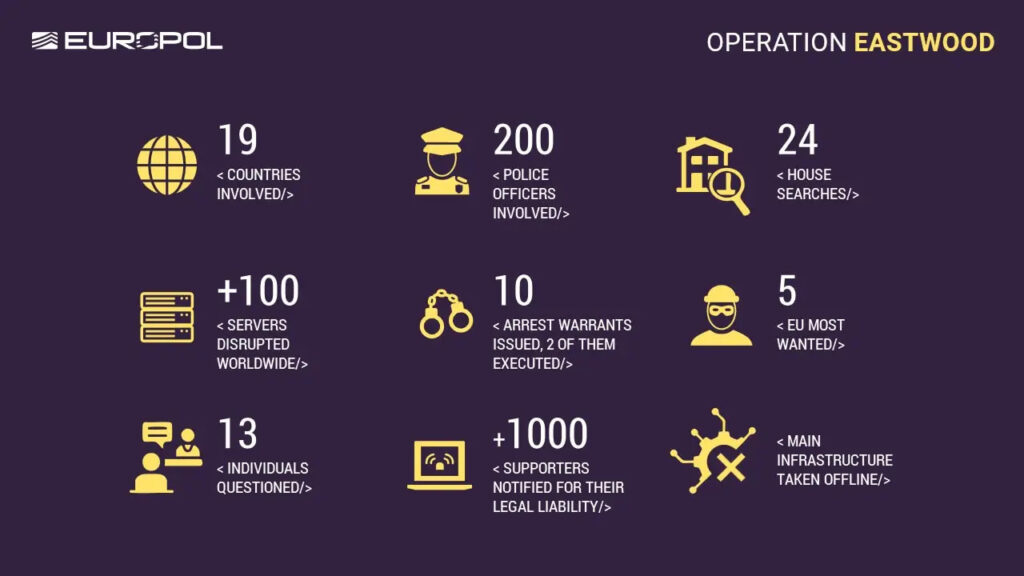
The operation culminated in an “action day” on July 15. Authorities from Czechia, France, Germany, Italy, Spain, the United States, and other countries conducted 24 house searches, issued seven arrest warrants, including six in Germany targeting Russian nationals, and took down over 100 servers comprising the group’s botnet and command infrastructure. Two individuals arrested in France and Spain face preliminary charges. Five suspects have been added to the EU Most Wanted list.
Europol
NoName057(16) first emerged in early 2022 as a loosely coordinated hacktivist network professing support for the Kremlin. The group built a following of over 4,000 sympathizers, mostly Russian-speaking individuals who participated in distributed denial-of-service (DDoS) attacks through the DDoSia platform. These volunteers used simple scripts and tools to overwhelm websites belonging to Western governments, public services, banks, and private companies seen as supporting Ukraine. Incentivized through cryptocurrency payments and gamified leaderboards, participants were rewarded with digital badges and public acknowledgments, fostering an atmosphere similar to online gaming communities.
The group lacked advanced technical capabilities or formal command structures but leveraged ideology and online propaganda to drive mass participation. Recruits were mobilized via Telegram, pro-Russian forums, and fringe chat groups, where they were provided with attack targets, tutorials, and malware downloads. Many of these actors were unaware that their participation constituted criminal conduct under international and national laws.
NoName057(16) gained notoriety through opportunistic cyberattacks tied to high-profile events. In Germany, 14 attack waves since November 2023 targeted over 250 organizations, including defense manufacturers and public institutions. Swedish authorities and financial services were hit during national events, while in Switzerland, attacks coincided with a Ukrainian address to Parliament and the 2024 Peace Summit at Bürgenstock. Dutch officials confirmed a similar disruption effort during the recent NATO summit. These attacks, though mitigated, underscored the group’s intent to disrupt diplomatic and political events aligned against Russia.
The group was also highlighted last year by Mandiant in a broader threat assessment of the 2024 Paris Olympics. Analysts flagged NoName057(16) as a significant hacktivist threat capable of DDoS campaigns intended to embarrass France and NATO allies during the games.
To limit future participation in similar campaigns, authorities sent formal warnings to over 1,000 individuals identified as supporters of NoName057(16), including at least 15 administrators. These messages, delivered via messaging platforms used by the group, informed recipients of their criminal liability under national and international law.







Leave a Reply