
Check Point Research has uncovered a sophisticated malware campaign exploiting Discord’s invite system to redirect users to malicious servers, launching multi-stage infections that deploy AsyncRAT and a customized Skuld Stealer.
The attackers hijack expired or deleted Discord invites using vanity link registration and leverage trusted platforms like GitHub, Bitbucket, Pastebin, and Discord itself for payload delivery and data exfiltration.
The campaign was discovered by Check Point's cybersecurity analysts following an in-depth analysis of live attack infrastructure and payloads. The researchers identified the abuse of Discord’s custom invite system, particularly targeting communities that lost their server “Level 3 Boost” status, making their once-valid custom links available for malicious re-registration. Additionally, regular invite codes, especially those consisting of lowercase letters and digits, were also found to be hijackable under specific conditions. This subtle yet dangerous flaw enables threat actors to replace once-trusted links with malicious destinations, tricking users into entering attacker-controlled Discord servers under the illusion of legitimacy.
Abusing Discord’s invite system
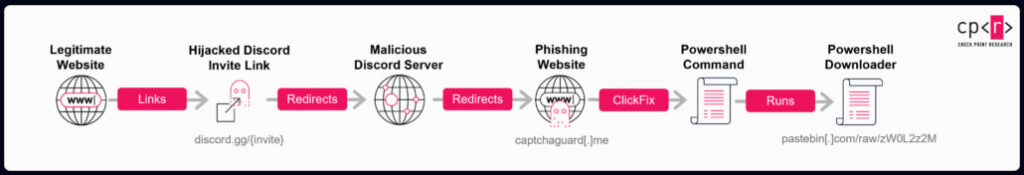
Discord, a widely used communication platform with over 150 million monthly active users, provides invite links for users to join servers. These can be temporary, permanent, or vanity links, each with distinct expiration behaviors. In this campaign, adversaries registered previously expired or deleted invites as new vanity links, effectively reassigning them to servers under their control. Victims were lured into these servers through links still listed on trusted websites, forums, or Telegram channels, unaware that the destination had changed.
Upon joining these malicious servers, users encountered a fake “verify” process driven by a bot named Safeguard, which redirected them to a phishing website (captchaguard[.]me). Here, through social engineering and the “ClickFix” technique, a deceptive user experience design that encourages manual interaction, users were duped into running a PowerShell command copied to their clipboard. This command silently downloaded and executed a script hosted on Pastebin, triggering the malware delivery chain.
Check Point Research
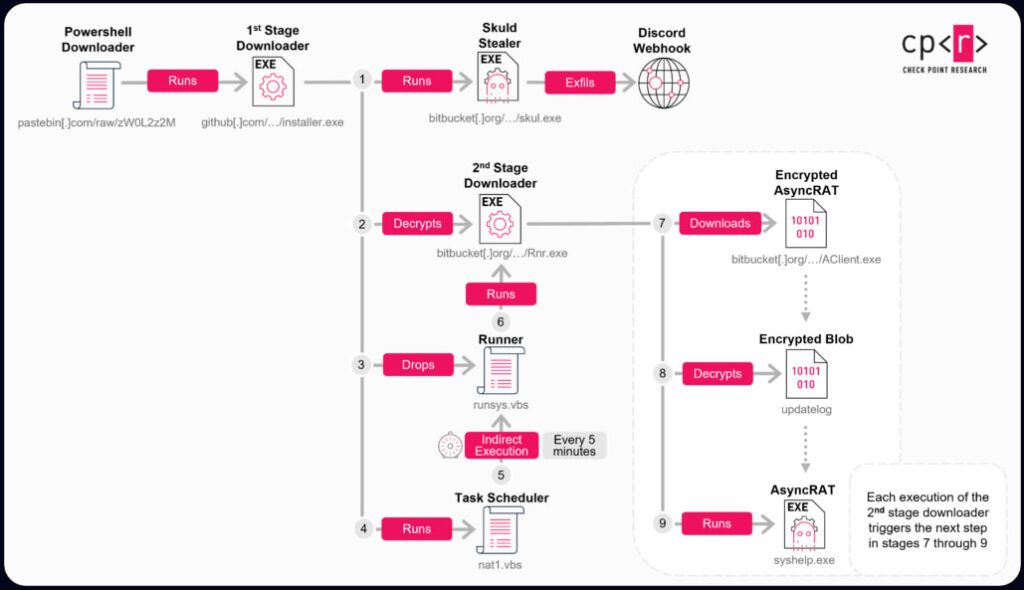
The infection sequence relies on multiple download stages and time-based sandbox evasions. The PowerShell script retrieves a loader (installer.exe) from GitHub, which fetches encrypted payloads from Bitbucket. These include:
- AsyncRAT: A remote access trojan offering full system control, keylogging, and file manipulation, configured to contact its C2 via dynamic Pastebin URLs.
- Skuld Stealer (customized variant): A Go-based stealer targeting Discord credentials, browser-stored credentials, and particularly, Exodus and Atomic cryptocurrency wallets. It injects malicious .asar files into wallet directories to capture seed phrases and passwords, exfiltrating them via Discord webhooks.
- ChromeKatz-based stealer: An advanced module adapted to bypass Chrome’s Application-Bound Encryption (ABE), extracting cookies directly from the memory of Chromium-based browsers.
Check Point Research
The attackers used sandbox evasion techniques, including multi-minute execution delays and argument-triggered behaviors. These allowed the malware to remain undetected in automated analysis environments. Each payload was encrypted using a simple but effective XOR scheme, with downloaders decrypting and executing them conditionally. Scheduled tasks ensured persistence and staged execution, giving AsyncRAT and Skuld ongoing access to compromised systems.
Bitbucket download statistics provided an indication of the campaign’s scope, showing over 1,300 downloads across various repositories. Victims were observed across multiple countries,s including the United States, Vietnam, France, Germany, and the United Kingdom. A separate lure targeting gamers used a pirated Sims 4 DLC unlocker to distribute the same malware chain.
The infrastructure involved trusted services: GitHub hosted initial loaders, Bitbucket stored payloads, Pastebin served decryption scripts, and Discord itself handled data exfiltration via webhooks. This use of legitimate services allowed the operation to blend seamlessly with normal traffic, evading many detection systems.
Check Point researchers warn that while Discord has taken steps to disable the malicious bot involved, the core issue, reusable invite codes in vanity links, remains exploitable. Users and administrators should avoid publishing temporary or lowercase-only invite links, and always verify invite link validity periodically.







Leave a Reply