
Authorities across multiple continents have taken down Danabot, one of the most prolific malware-as-a-service platforms in recent years, as part of Operation Endgame, an expansive law enforcement campaign targeting the initial access layer of the ransomware ecosystem.
The takedown neutralized Danabot's infrastructure, disrupted its botnets, and led to criminal charges against 16 alleged operators linked to a Russia-based cybercrime syndicate.
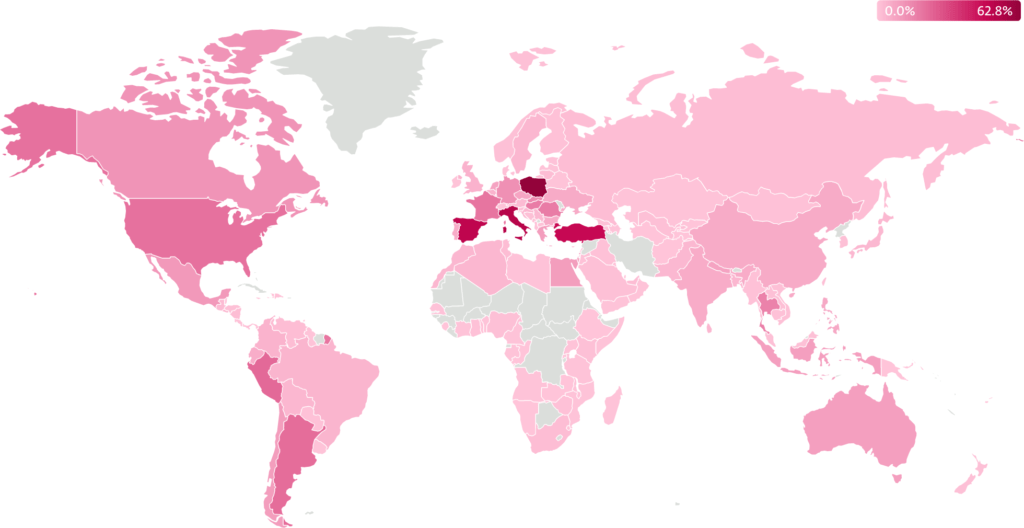
The U.S. Department of Justice revealed the charges against key figures, including Aleksandr Stepanov (alias “JimmBee”) and Artem Kalinkin (alias “Onix”), both of Novosibirsk, Russia. According to the unsealed indictment, Stepanov and Kalinkin were instrumental in developing and managing Danabot, offering it to criminal affiliates who used it to compromise over 300,000 computers worldwide. Damage from Danabot's activities is estimated at over $50 million.
ESET
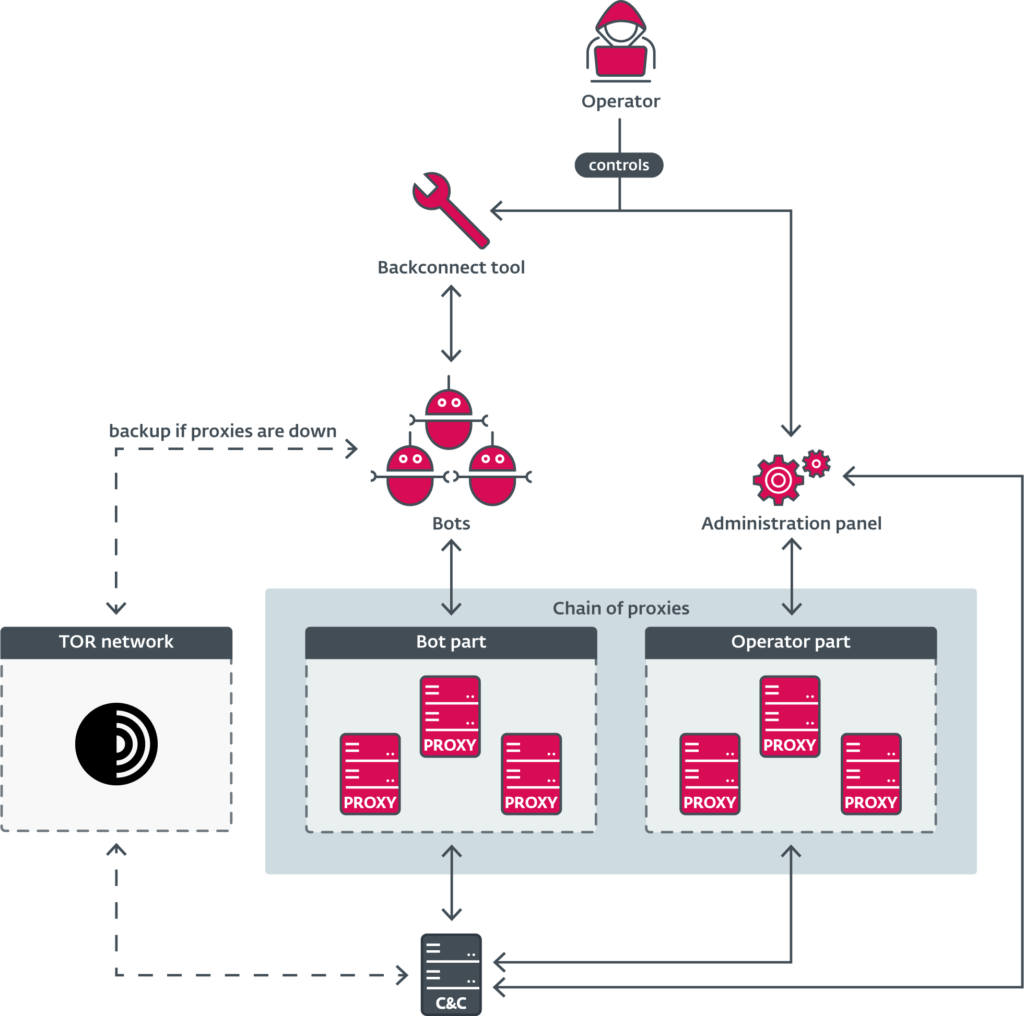
Danabot, first observed in 2018, evolved from a banking trojan into a full-fledged infostealer and malware distribution platform. Operating on a malware-as-a-service (MaaS) model, it enabled affiliates to rent access to sophisticated tools, including administration panels, backconnect utilities for real-time victim interaction, and a robust command-and-control (C&C) infrastructure. ESET, which contributed to the years-long investigation, identified over 1,000 distinct C&C servers linked to the botnet.
ESET
The malware's core functionality included browser credential theft, keylogging, screen recording, cryptocurrency wallet hijacking, and file exfiltration. It also served as a launchpad for deploying additional malware, including ransomware strains like LockBit, Buran, and Crisis. Particularly concerning was a Danabot variant used to target military, diplomatic, and government entities in North America and Europe, exfiltrating sensitive data to a separate command structure.
Danabot's infrastructure included proxy relays, Tor modules, and private C&C server deployments to obscure operator identity and ensure resilience. Affiliates could customize and deploy builds via a centralized system operated by the malware's core developers, receiving precompiled binaries and full configuration capabilities through a dedicated GUI-based panel.
The operation against Danabot was part of a broader enforcement wave from May 19 to 22 under the banner of Operation Endgame. Coordinated by Europol and Eurojust, and supported by agencies from the U.S., Canada, the UK, Germany, France, the Netherlands, Denmark, and Australia, the crackdown targeted multiple initial access malware strains, including Qakbot, Trickbot, Bumblebee, Warmcookie, and Latrodectus. Nearly 300 servers were taken down globally, with cryptocurrency assets worth €3.5 million seized and international arrest warrants issued for 20 suspects.
The infrastructure takedown and arrests were made possible through collaboration between law enforcement and private sector partners, including Amazon, Google, Intel471, ESET, Team Cymru, and others.
As part of the cleanup, U.S. authorities, working with nonprofit cybersecurity organizations like the Shadowserver Foundation, have begun notifying victims and assisting in system remediation.
In a related announcement the same day, the U.S. indicted Rustam Rafailevich Gallyamov, a Russian national accused of orchestrating the Qakbot botnet. Gallyamov, also linked to ransomware deployment, faces charges of conspiracy and wire fraud, with a parallel forfeiture complaint seeking over $24 million in cryptocurrency.







Leave a Reply