
Google's Threat Intelligence Group (GTIG) has uncovered a new espionage tool called LOSTKEYS, attributed to the Russia-linked threat group COLDRIVER.
The malware, observed in active campaigns throughout early 2025, marks a shift in the group's capabilities — from credential theft to direct data exfiltration from infected systems.
Google's analysis outlines a multi-stage attack chain used to deliver LOSTKEYS, a Visual Basic Script-based payload capable of stealing files, capturing system metadata, and monitoring active processes. This new strain was deployed against high-value targets such as advisors to Western governments, journalists, think tanks, and non-governmental organizations, especially those connected to NATO and Ukraine.
COLDRIVER, also known by the aliases UNC4057, Star Blizzard, and Callisto, has a long track record of targeting email accounts of diplomats, security officials, and NGO workers. Historically, the group used spear-phishing to steal credentials and access sensitive correspondence. However, since 2024, it has occasionally delivered malware like SPICA to access files directly from victims' systems. The emergence of LOSTKEYS suggests an increasing focus on full device compromise for intelligence collection.
LOSTKEYS infection chain
GTIG observed the new campaign in January, March, and April 2025. Each incident followed a layered infection chain beginning with social engineering. The initial lure is a fake CAPTCHA hosted on a malicious site, which tricks users into copying and executing a PowerShell script from their clipboard. This script fetches a second-stage payload from the IP address 165.227.148[.]68. This approach, known as “ClickFix”, has been used by several APT actors to bypass traditional security barriers.
The second stage includes a VM evasion mechanism that hashes the screen resolution of the host machine. If the hash matches a known sandbox profile, execution halts; otherwise, the chain proceeds to download a third stage. This third stage, delivered again via PowerShell, decodes into scripts that fetch two additional files: a “decoder” script and an encoded payload. Using two unique keys per infection chain, the decoder uses a substitution cipher to unpack the final payload, LOSTKEYS.
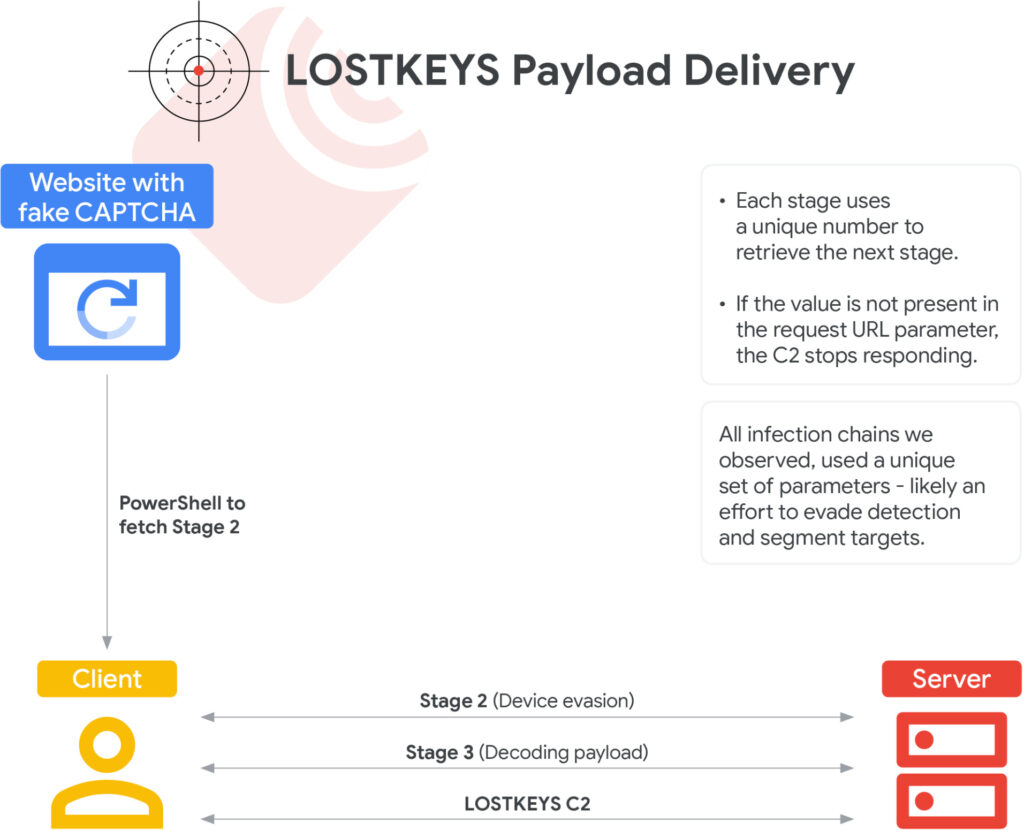
LOSTKEYS focuses on exfiltrating documents from specific folders and file types, as well as sending system telemetry to command-and-control infrastructure. Google noted that the malware is deployed sparingly, likely reserved for high-value intelligence targets. Notably, older versions of the malware dating back to December 2023 were found masquerading as files related to the Maltego OSINT tool, though it remains unclear if COLDRIVER also operated those early variants.
Google has taken steps to disrupt this campaign by flagging malicious domains and files in Safe Browsing and alerting targeted Gmail and Workspace users. Affected or at-risk users — such as those in NGOs, journalism, or policy — are urged to enroll in Google's Advanced Protection Program, enable Enhanced Safe Browsing in Chrome, and ensure all software is fully updated.
For enterprise defenders, enforcing least privilege policies and disabling script execution by default are essential mitigations against this and similar ClickFix-style campaigns. GTIG has shared IOCs and YARA rules to help the security community detect and neutralize LOSTKEYS deployments.







Leave a Reply