Researchers have discovered a new class of side-channel attacks that exploit electric vehicle (EV) battery consumption data to reveal sensitive user information.
The study, conducted by Francesco Marchiori and Mauro Conti from the University of Padova, demonstrates how attackers can infer driver identity, driving style, vehicle occupancy, and even trip start and end locations with a remarkable 95.4% success rate.
Battery data as a privacy threat
While EV battery consumption data is typically considered operational, this study highlights its potential to be misused for surveillance and tracking. The researchers leveraged machine learning techniques on both simulated and real-world datasets to analyze power consumption patterns. Their findings indicate that energy consumption data, even without GPS tracking, can be used to identify individual drivers and predict their routes.
This work builds on previous research that explored battery data vulnerabilities in smartphones and wireless charging devices. However, most EV-related studies have focused on charging patterns rather than real-time battery consumption while driving. The researchers argue that this oversight leaves a significant security gap.
arxiv.org
The ‘Leaky Batteries’ attack
The attack methods developed by Marchiori and Conti allow adversaries to infer:
- Driver Identity: Recognizing unique driving patterns through energy usage.
- Driving Style: Distinguishing between aggressive, normal, and defensive driving behaviors.
- Vehicle Model: Identifying EV make and model based on power consumption characteristics.
- Occupancy Detection: Estimating the number of passengers based on battery usage variations.
- Auxiliary System Usage: Inferring climate control, entertainment, and other system usage.
- Trip Start & End Locations: Predicting where an EV trip begins and ends based on habitual consumption patterns.
These inferences could be used for targeted surveillance, insurance profiling, or even coordinated cyber-physical attacks, raising concerns over regulatory and privacy implications.
arxiv.org
Real-world implications and possible countermeasures
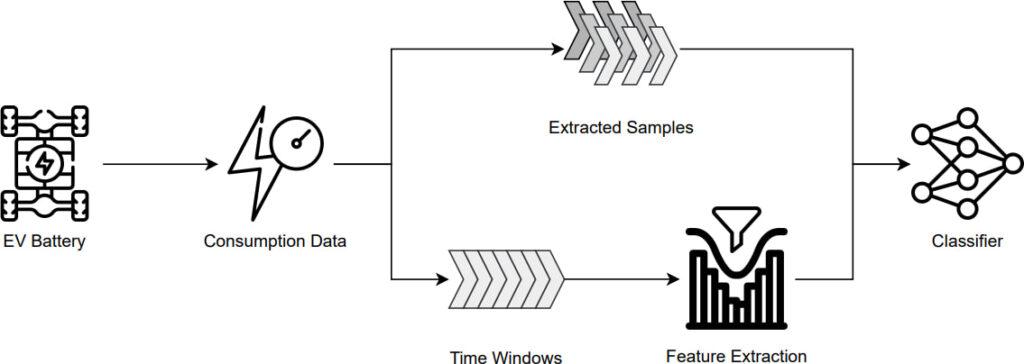
The research utilized datasets from both simulations and real-world driving tests. The real-world data included 58 trips recorded in Spain with two EV models — Nissan Leaf and Dacia Spring. The machine learning models showed high accuracy across all attack types, particularly in vehicle identification (99.9%), driving style detection (97.2%), and trip origin inference (95.5%).
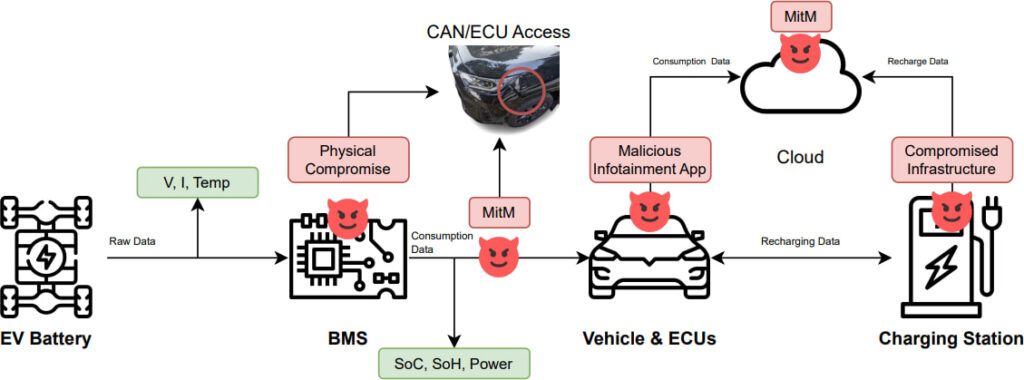
Since modern EVs continuously transmit battery telemetry to manufacturers and cloud-based services, this data could be intercepted by attackers via compromised charging stations, malicious apps, or man-in-the-middle (MitM) attacks on vehicle telematics.
To mitigate these risks, the researchers propose a time-based aggregation technique, which reduces data granularity by averaging consumption data over larger time windows. This method decreases the success rate of the attacks to approximately 45%, making inferences less reliable. However, further research is needed to balance privacy protection with maintaining essential vehicle functions.
As EV adoption grows, so do the risks associated with data privacy, and battery consumption data is just one of the multiple potential candidates for side-channel attacks. Automakers and regulatory bodies must address these risks to ensure EV user privacy and security in the evolving smart transportation ecosystem.







I wonder it this can happen to Tesla at a Tesla charger. They would have to get in somehow.
CCS is so much harder to secure with clubs, apps, credit card readers.