
A new variant of the TrickMo Android banking trojan, analyzed by Cleafy's Threat Intelligence team, has not only enhanced its stealth capabilities but also exposed a critical flaw in the attackers' infrastructure, resulting in a large-scale data leak. Originally designed to facilitate banking fraud by intercepting credentials and two-factor authentication codes, this latest version of TrickMo has evolved into a more dangerous threat, now leaking victims' sensitive data due to poor operational security on the part of the malware operators.
TrickMo discovery and analysis
In June 2024, Cleafy's team identified an unclassified Android banking trojan that was later confirmed to be a variant of TrickMo, a malware previously tied to the TrickBot group. Known for targeting financial institutions, TrickMo typically intercepts one-time passwords (OTPs) and captures user credentials. However, this variant exhibited enhanced anti-analysis features like malformed ZIP files and the use of JSONPacker to evade detection. Additionally, the malware was distributed via a dropper app disguised as Google Chrome, tricking users into granting it extensive permissions through Android's accessibility services.
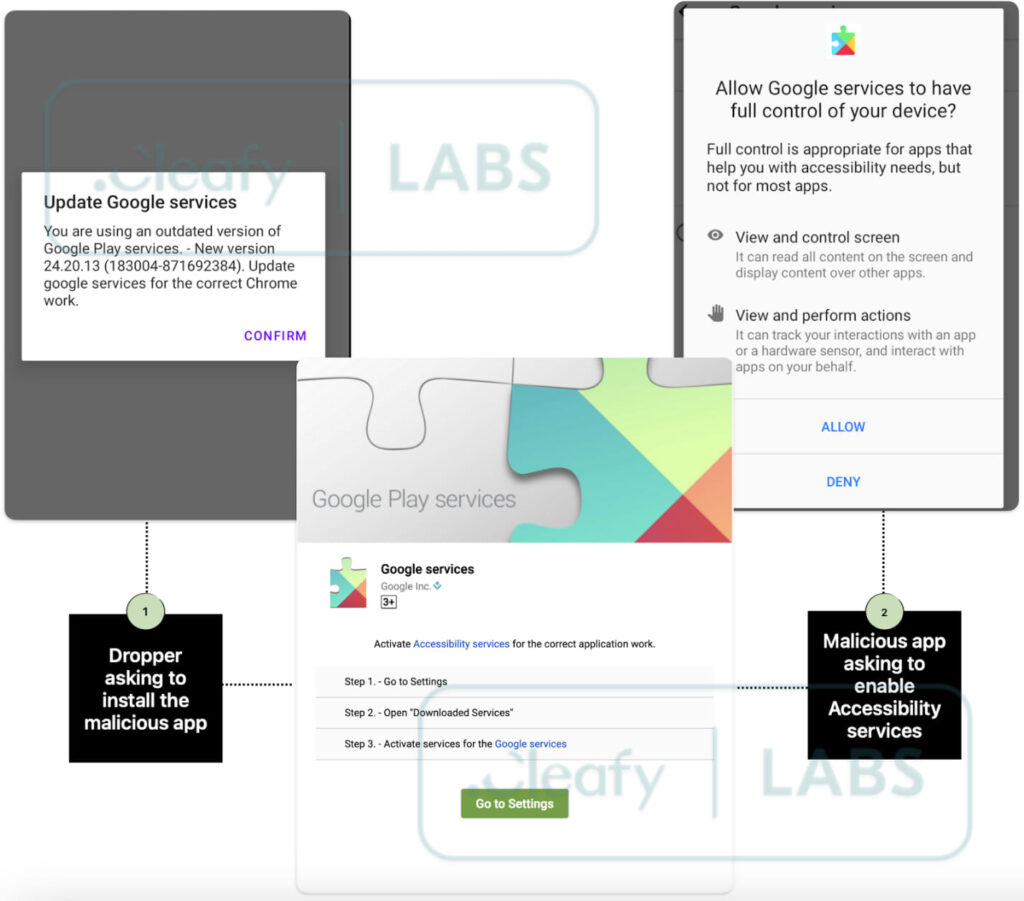
Cleafy
While the malware's technical sophistication is concerning, the team uncovered a far more alarming issue during their investigation—the misconfigured Command and Control (C2) infrastructure, which stores exfiltrated data from infected devices. By gaining access to critical C2 endpoints, Cleafy's researchers found that the stolen data, including sensitive credentials, personal photos, and device logs, was not adequately protected and could be accessed by anyone with basic knowledge of the system.
Extent of data leak
The leaked data totaled over 12 GB, encompassing sensitive information from compromised devices. Among the files were personal photos, including identification documents such as passports and credit cards, exposing victims to severe risks like identity theft and fraud. The C2 server stored user credentials in unprotected CSV files containing usernames and passwords for various financial and online accounts, as well as logs of operations performed on the compromised devices.
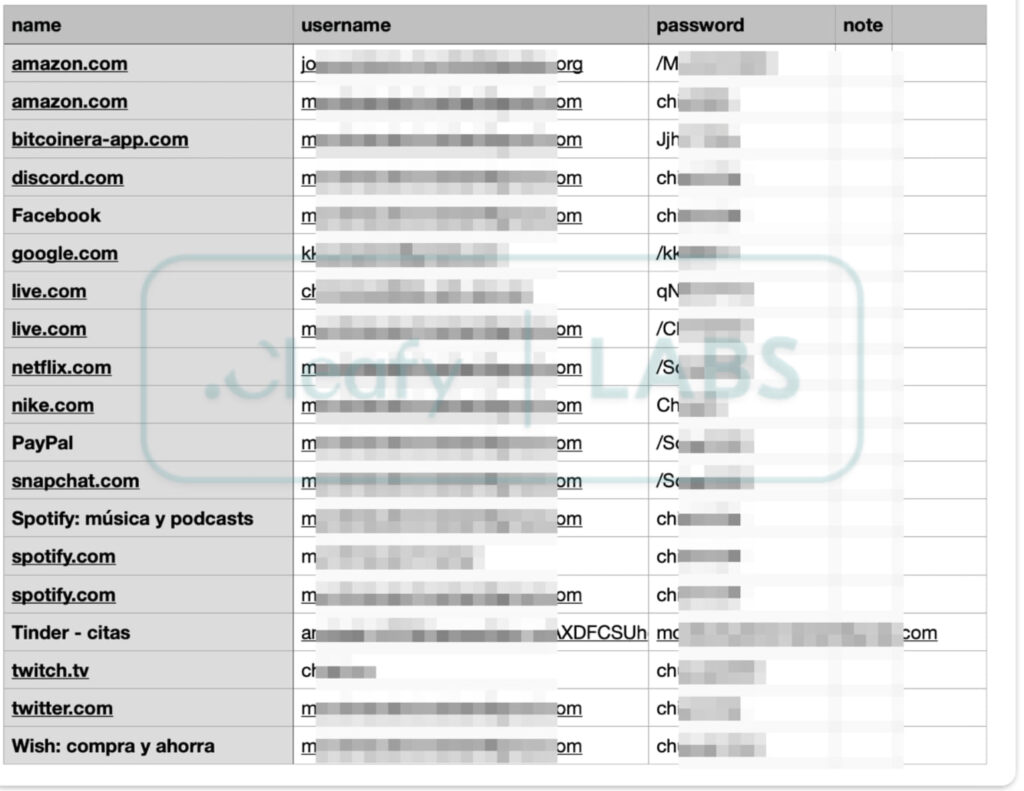
Cleafy
Moreover, TrickMo's operators created HTML overlay pages that were used for phishing attacks against services like Binance, Alpha Bank, and ATB Mobile. These files, also accessible without proper authentication, could be leveraged by third parties to conduct further malicious campaigns against the victims.
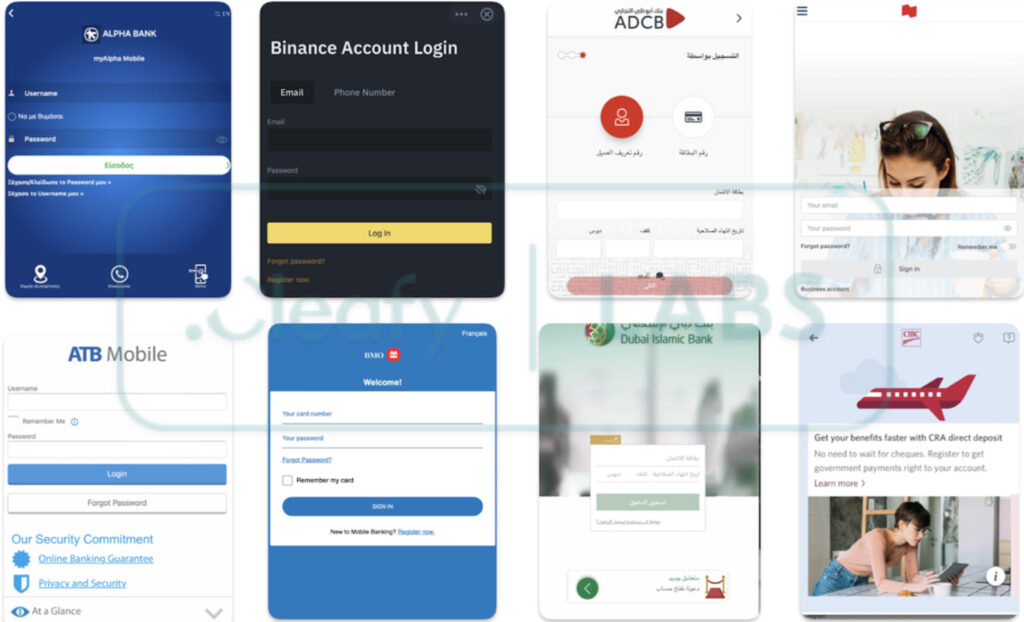
Cleafy
The operators behind TrickMo made several crucial mistakes in securing their infrastructure. While the malware itself employs advanced obfuscation and anti-analysis techniques to avoid detection, the lack of security on the C2 server means that anyone could access the stolen data. The C2 server lacked basic authentication mechanisms, and key endpoints were left exposed, allowing external parties to retrieve exfiltrated files, such as personal images, login credentials, and financial information.

Cleafy
This breach dramatically increases the risk to victims, as not only are they at the mercy of TrickMo's operators, but they also face the possibility of their data being exploited by other malicious actors who might stumble upon the exposed information. The accessibility of such sensitive data could trigger a cascade of harmful events, from financial fraud to extortion and identity theft.
A broader threat
While TrickMo was initially focused on banking fraud, the data exposed by the compromised C2 server significantly broadens the scope of the threat to affected individuals. Identity theft becomes a serious possibility when personal documents, such as passports and credit card images, are leaked. Compromised credentials could allow attackers to take over victims' bank accounts, emails, and social media profiles. In the worst cases, attackers could use sensitive photos to blackmail or coerce victims.
This leak highlights a broader issue: when cybercriminals fail to secure the data they steal, victims become vulnerable to multiple attackers. The malicious use of stolen data could extend far beyond the initial intent of banking fraud, leading to a variety of cybercrimes.
Defensive measures
To protect against malware like TrickMo, users should be cautious of apps requesting unnecessary permissions, particularly those disguised as legitimate services like Google Chrome or Google Play. Ensuring that mobile devices are running up-to-date security patches and using strong two-factor authentication (2FA) mechanisms are essential defensive steps. Additionally, organizations can integrate advanced mobile threat detection solutions like Cleafy's, which provide real-time protection against such sophisticated malware.
Individuals who suspect their devices have been compromised should immediately reset all passwords, monitor their financial accounts, and consider using identity theft protection services.







Leave a Reply