
A new wave of attacks linked to North Korea's notorious Lazarus Group targets software developers through fake job recruiter schemes, according to a recent report from ReversingLabs. In the ongoing VMConnect campaign, attackers impersonate recruiters from major financial services firms, distributing malicious Python packages disguised as coding tests. These packages, which resemble legitimate tools, aim to compromise developer systems.
The VMConnect campaign was first discovered in August 2023 by ReversingLabs, who attributed the campaign to the Lazarus Group based on research by the Japan Computer Emergency Response Team (CERT). The malicious actors were found to be using deceptive tactics, including fake LinkedIn profiles, to lure developers into downloading and running malicious code hidden in job interview-related materials.
Lazarus exploiting trust
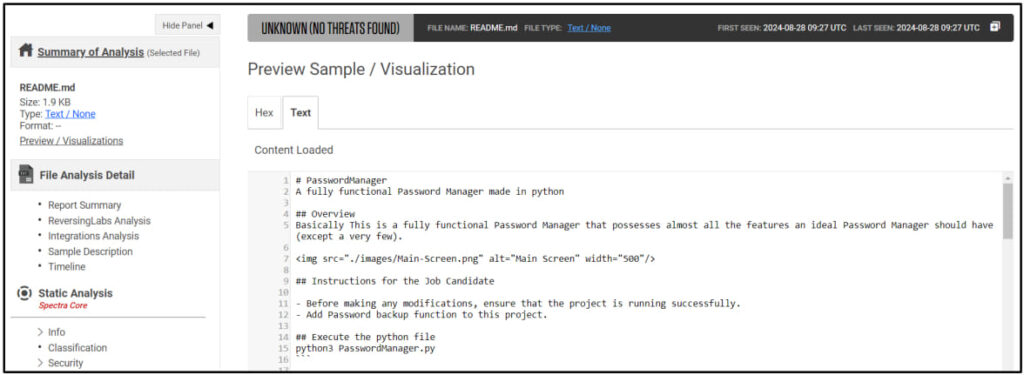
The attacks primarily exploit trust between recruiters and developers. In this latest round of attacks, developers are provided with files such as “Python_Skill_Test.zip,” which they are instructed to download and complete as part of a coding assignment. These files, containing malware, are presented as tasks to fix bugs in software such as password managers. Once the developer executes the project, malicious code embedded in the Python files is activated, giving the attacker control of the victim's system.
ReversingLabs
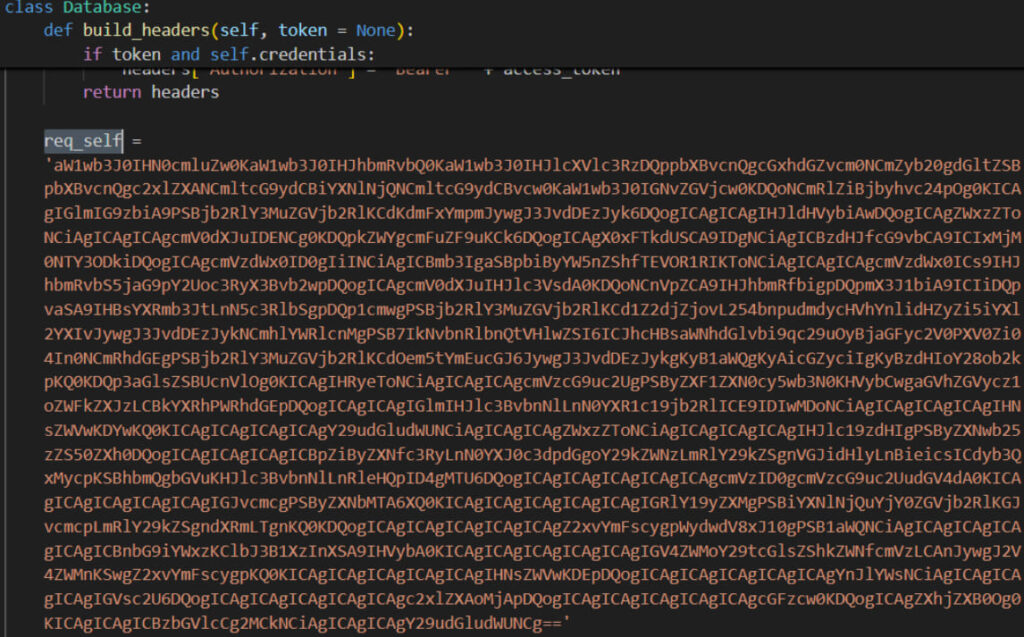
The malicious code is typically embedded in the init.py files of modules like pyperclip and pyrebase. Encoded using Base64, the malware contacts a command-and-control (C2) server to download further malicious payloads. ReversingLabs' detailed analysis revealed that the code is capable of executing Python commands on the infected machine, giving the attackers significant control over the compromised systems.
ReversingLabs
Lazarus Group, known for high-profile cyberattacks, including the 2014 Sony Pictures hack, is heavily involved in financial and cryptocurrency theft operations. They have increasingly targeted developers in their campaigns. The VMConnect campaign leverages this expertise, using LinkedIn and GitHub as delivery mechanisms to distribute malware via job recruitment schemes. Attackers use the names of reputable companies like Capital One to lend credibility to their outreach, which further entices victims into running the malicious tests without suspicion.
The compromised packages analyzed by ReversingLabs showed clear links to previous attacks by the Lazarus Group. These Python packages imitated legitimate open-source tools while hiding their true functionality in compiled Python files (PYC files). These compiled files make the malicious code harder to detect as they are stored in a binary format, preventing easy scanning by typical security solutions.
Developers' plight
One developer, who was identified as a victim, shared details of how he was tricked into participating in the scheme. He had been contacted by a recruiter impersonating a Capital One employee in January 2024. Following instructions, the developer downloaded a GitHub repository that contained the malicious package and was asked to fix a bug. The task was engineered to ensure the malware was executed on the victim's system before any changes could be made, granting the attacker access.
The attackers further cement their schemes by instilling urgency. README files included in the malicious projects emphasize the need for quick turnarounds, which reduces the likelihood of developers reviewing the code thoroughly before executing it.
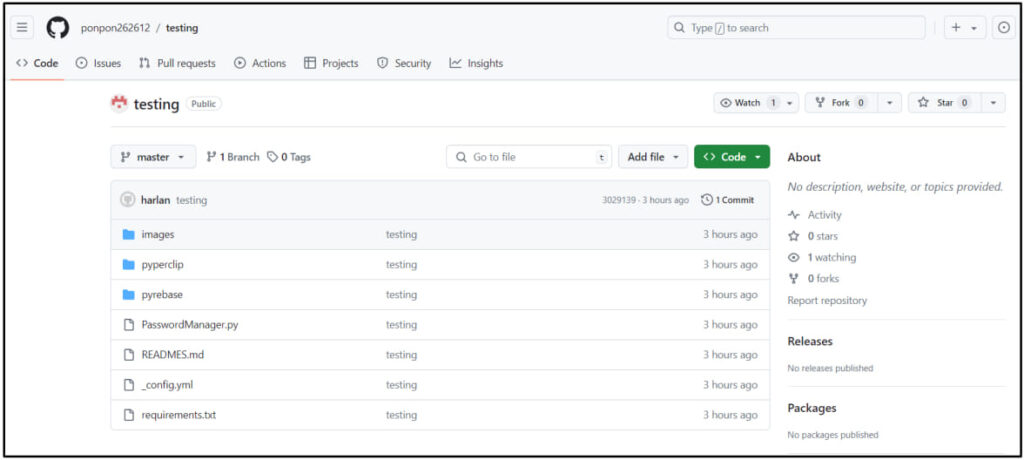
Despite initial reports surfacing over six months ago, the VMConnect campaign remains active. On July 31, 2024, ReversingLabs discovered a new GitHub repository containing the same malicious code. The project was published under a new account just as ReversingLabs made contact with one of the targeted developers, suggesting the attackers are still operational and aware of the research into their activities.
ReversingLabs
ReversingLabs has reported the malicious repositories to GitHub, but as of the report's release, some still remain online. Given the persistence of new samples surfacing, it is clear that the campaign is ongoing and continues to pose a serious threat to the developer community.
Defense suggestions
To defend against such threats, organizations with IT teams and independent software developers should:
- Consider the risks of downloading and executing files from unverified sources, even if they appear to come from reputable recruiters.
- Verify recruiter identities from independent sources.
- Implement stringent security protocols for reviewing and executing code, especially when handling unfamiliar packages, like executing them on isolated virtual machines.
- Monitor for unusual activity on developer machines and review any third-party code, particularly when downloaded from platforms like GitHub or PyPI.
- Use advanced threat detection systems, such as YARA rules and behavior-based monitoring, to identify and block malicious files before they can be executed.





Leave a Reply