A newly uncovered cyber campaign, tracked as Green Nailao, has been targeting European organizations, particularly in the healthcare sector, using ShadowPad and PlugX malware to deploy NailaoLocker, a previously unknown ransomware strain.
Researchers from Orange Cyberdefense CERT and Trend Micro have independently analyzed the campaign, revealing links to China-nexus threat actors and an evolving malware toolkit.
Ransomware attack leveraging vulnerable VPNs
The campaign was active between June and October 2024, with threat actors exploiting CVE-2024-24919, a critical vulnerability in Check Point Security Gateways. This flaw, patched in May 2024, allowed attackers to extract password hashes from vulnerable VPN appliances and gain access using legitimate credentials.
Once inside, the attackers conducted network reconnaissance and lateral movement using Remote Desktop Protocol (RDP), deploying ShadowPad and PlugX through DLL side-loading. In many cases, ShadowPad was injected into registry keys to ensure persistence, with some backdoors remaining undetected for over two weeks before further exploitation.
Trend Micro
Espionage tools also deployed
ShadowPad, a modular backdoor, has been associated with Chinese espionage groups since at least 2015. In this campaign, a heavily obfuscated variant of the malware was deployed, making detection difficult. Researchers noted new anti-debugging features, DNS over HTTPS (DoH) for stealthy communication, and encrypted payload storage within the Windows registry, tied to the system’s volume serial number.
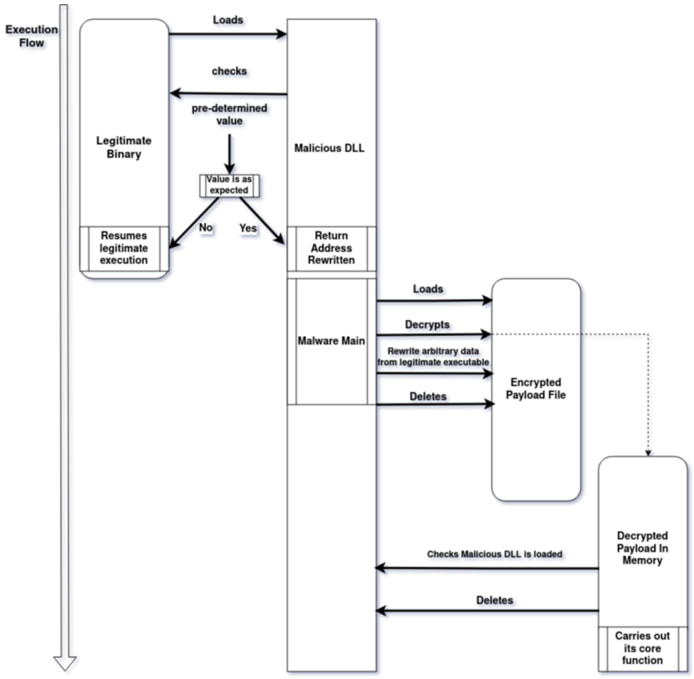
PlugX, another well-known implant often linked to Chinese APTs, was deployed in a three-file execution chain involving a legitimate McAfee executable (mcoemcpy.exe), a malicious DLL (McUtil.dll), and an encrypted payload (Mc.cp). The malware abused Windows services for persistence and performed process hollowing to inject shellcode into legitimate processes.
NailaoLocker ransomware encrypting data
In at least two observed cases, the campaign escalated beyond espionage to deploy NailaoLocker, an undocumented ransomware strain. The attackers used Windows Management Instrumentation (WMI) to distribute three files across infected systems:
- usysdiag.exe – A legitimate executable signed by Beijing Huorong Network Technology Co., Ltd
- sensapi.dll – A malicious DLL loader (NailaoLoader)
- usysdiag.exe.dat – The encrypted NailaoLocker payload
Orange
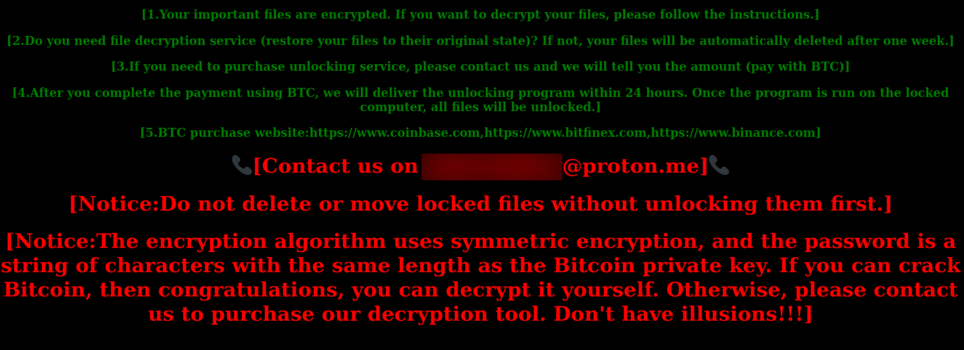
The ransomware was relatively unsophisticated, lacking key features found in more advanced ransomware strains. It did not scan network shares, stop critical processes, or include anti-debugging protections. Files were encrypted using AES-256-CTR, renamed with a “.locked” extension, and a ransom note was dropped into affected directories. Victims were instructed to contact attackers via a disposable ProtonMail address to pay in Bitcoin for decryption.
Interestingly, the ransom note closely resembled those used by Kodex Softwares (formerly Evil Extractor), a low-tier cybercriminal operation. However, forensic analysis found no code overlaps between NailaoLocker and Kodex ransomware, suggesting the attackers deliberately copied the ransom note format as a false flag.
Orange
Bizarre attacks by Chinese APTs
Orange Cyberdefense CERT and Trend Micro both noted tactical overlaps between Green Nailao and past Chinese cyber operations, particularly those associated with APT41 (BRONZE STARLIGHT) and Cluster Alpha (STAC1248). However, NailaoLocker’s deployment was an anomaly, as ransomware is rarely used alongside ShadowPad, a tool typically linked to state-backed espionage.
Three potential motivations for the ransomware deployment were proposed:
- False Flag Operation – The ransomware may have been used to distract from espionage-related data theft.
- Dual-Purpose Attack – The attackers may have sought both financial gain and intelligence collection, similar to North Korean cybercrime tactics.
- Moonlighting APT Activity – Some threat actors with access to state-sponsored tools may have been running a side operation for personal profit.
Despite these theories, analysis of cryptocurrency wallets tied to NailaoLocker showed no ransom payments, indicating low financial success.
Organizations, particularly those in the healthcare, manufacturing, and critical infrastructure sectors, should ensure CVE-2024-24919 is mitigated, implement multi-factor authentication (MFA), and use threat intelligence feeds to detect known Indicators of Compromise (IoCs). It is also recommended to limit remote desktop connections and implement network segmentation.







You should always be able to start over from scratch via onsite backups . You should be able too see that something is wrong . If I suspect I ran bad code , I would hold down the power button and kill it immediately , then insert my Linux Mint bootable and start over .