
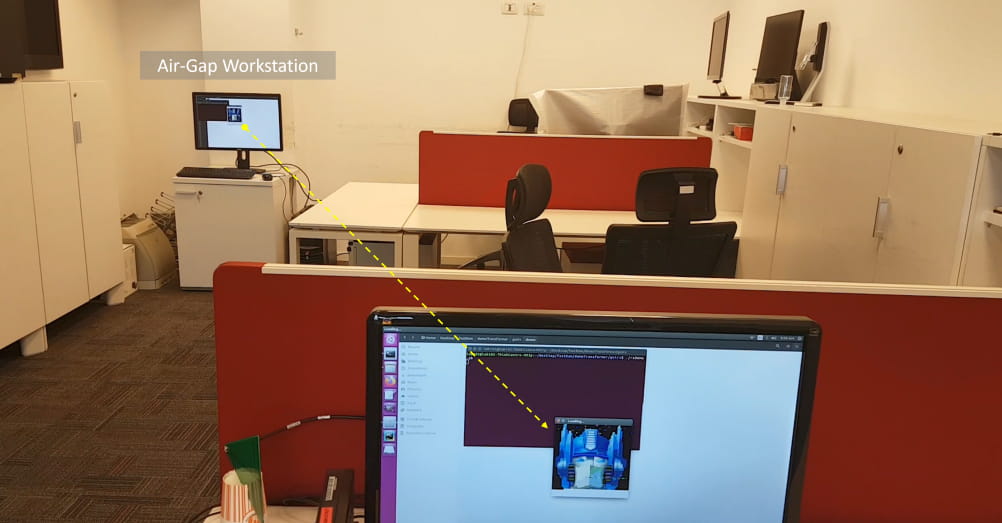
Researchers from the Ben-Gurion University of the Negev have uncovered a method to leak sensitive data from air-gapped systems, introducing a novel attack technique known as RAMBO (RAM-based electromagnetic covert channel).
The attack exploits the electromagnetic emissions generated by a computer's RAM, allowing attackers to exfiltrate information like encryption keys, passwords, biometric data, and files. This is achieved even in environments where systems are physically isolated from external networks.
arxiv.org
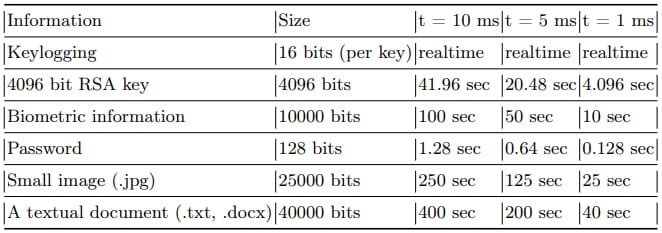
Leaking information at 7.5 kB/min
Led by Dr. Mordechai Guri, the study demonstrates how malware installed on an air-gapped system can manipulate memory operations to generate electromagnetic signals. These signals can be intercepted by a remote attacker using low-cost hardware like a software-defined radio (SDR) and a simple antenna. The attacker can then decode the radio signals to recover the leaked data. This attack can transmit data at speeds of up to 1000 bits per second (7.5 kB/min), making it a significant threat to air-gapped networks that are traditionally seen as highly secure.
arxiv.org
Air-gapped systems are often used in critical environments such as government, military, and industrial sectors where sensitive information must be safeguarded from external threats. These systems are physically separated from other networks, preventing direct or remote communication via wired or wireless means. Despite this isolation, previous attacks like Stuxnet and USB-based malware have shown that air-gapped systems are not immune to compromise. RAMBO extends this list by providing a non-contact method of data exfiltration.
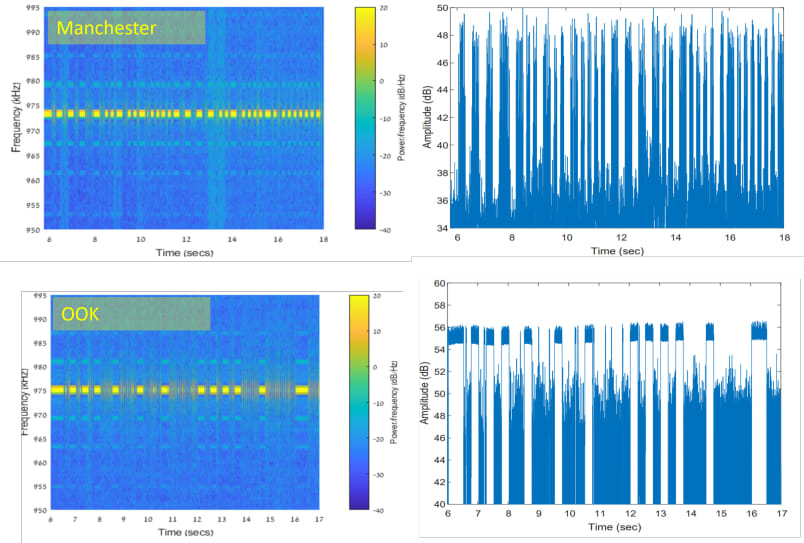
The researchers explain in the technical paper that the electromagnetic signals emitted by RAM activity can be modulated to carry binary data. By leveraging specific memory operations and modulation techniques, the malware can encode sensitive information and transmit it using the RAM's natural electromagnetic radiation. The signals are then captured by a radio receiver, which decodes the data, translating it back into its original form.
During their evaluation, the team used an Ettus B210 SDR and was able to intercept signals from distances up to 7 meters. The attack works even with the RAM inside modern workstations, and the emitted signals were detectable across various DDR generations. The ability to leak data, including real-time keylogging and encryption keys, demonstrates the practical risk this attack poses. The research highlights the importance of reconsidering the security measures for air-gapped systems, especially in environments where high-value data is at risk.
arxiv.org
Defending against RAMBO
To mitigate this new type of covert channel, the researchers propose several countermeasures. These include:
- Using Faraday cages or enclosures around critical systems to block electromagnetic emissions.
- Enforcing strict physical separation between critical systems and potential radio receivers.
- Monitoring memory access patterns that could indicate malicious signal generation.
Although effective, these countermeasures may introduce significant overhead or require costly implementations, particularly for large-scale deployments. Nonetheless, the discovery of RAMBO underscores the need for continuous vigilance in securing air-gapped systems as attackers find increasingly innovative ways to breach them.







Leave a Reply