
Starting in February 2025, Bitwarden will implement an additional security measure for accounts that do not have two-factor authentication (2FA) enabled. Users logging in from unrecognized devices will be required to verify their identity via an emailed code before accessing their vaults. This change aims to protect against unauthorized access and mitigate the risks of credential stuffing and phishing attacks.
Bitwarden enhancing security
Bitwarden, a leading open-source password manager, is reinforcing its authentication process to address security gaps for users who have not enabled 2FA. While the platform strongly encourages users to activate a two-step login for enhanced protection, some accounts remain vulnerable. The new verification measure introduces an additional checkpoint to prevent unauthorized logins.
Given that password vaults contain sensitive credentials, they are prime targets for cybercriminals. Attackers often exploit leaked credentials in credential-stuffing attacks or use phishing to trick users into revealing their master passwords. By requiring an emailed verification code for logins from unrecognized devices, Bitwarden ensures that even if an attacker obtains a user’s password, they will still need access to the associated email account to proceed.
New verification process
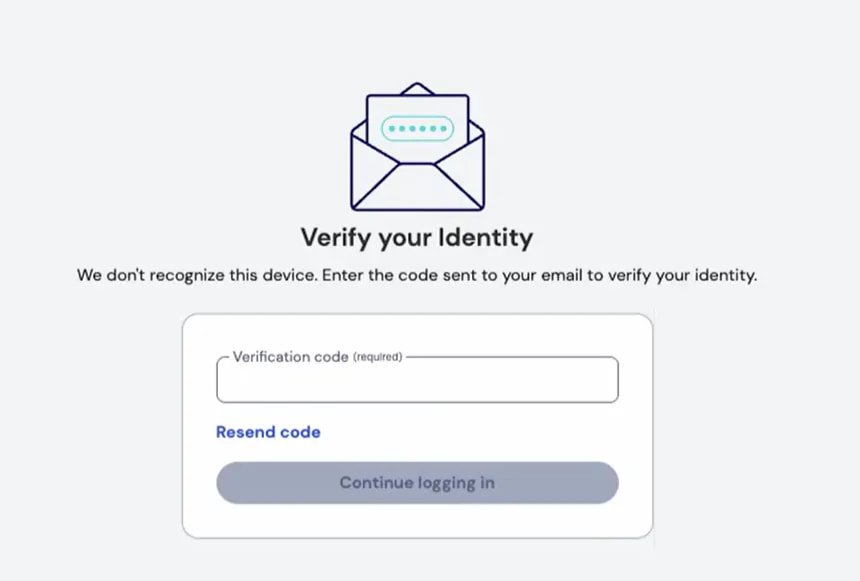
When a user attempts to log into Bitwarden from an unrecognized device and does not have 2FA enabled or enterprise Single Sign-On (SSO) configured, Bitwarden will trigger an additional verification step:
- After entering their email and master password, users will receive a verification code sent to their registered email address.
- The user must retrieve this code and enter it into the Bitwarden application to complete the login.
- Only after successful verification will access to the Bitwarden vault be granted.
This process adds a critical security layer for users who have not yet enabled two-factor authentication, making unauthorized access significantly more difficult.
Bitwarden
While email-based verification is a widely used security practice, it introduces potential access challenges. Users who store their email login credentials within Bitwarden may face difficulties retrieving the verification code if they are locked out of their vault. To avoid this issue, Bitwarden advises users to ensure they have access to their email accounts before attempting to log in or simply enable two-step login (2FA) to bypass the new verification requirement.
This new verification step should not be taken as a replacement for multi-factor authentication from hardware security keys or time-based codes from authenticator apps. Moreover, it is important for users to pick a unique, long, and complex master password for their accounts that is not used in any other service.






Leave a Reply