
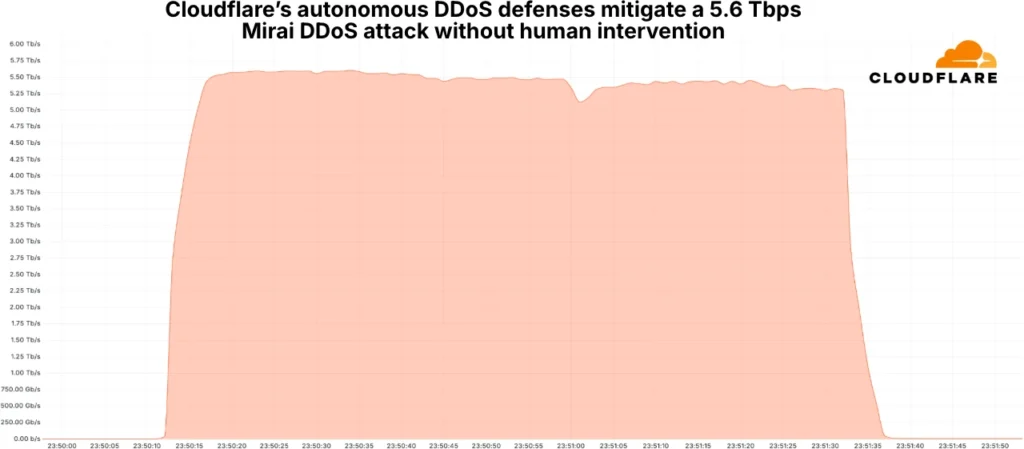
Cloudflare has revealed that it mitigated the largest Distributed Denial-of-Service (DDoS) attack ever recorded, peaking at 5.6 Terabits per second (Tbps) during the last quarter of 2024. This hyper-volumetric attack, alongside a staggering 53% annual increase in DDoS incidents, underscores the growing scale and sophistication of cyber threats worldwide.
The attack on October 29, 2024, targeted an Internet Service Provider (ISP) in Eastern Asia. It originated from a Mirai-variant botnet comprising over 13,000 compromised Internet of Things (IoT) devices. Despite its sheer size, Cloudflare’s autonomous defense systems detected and neutralized the attack within 80 seconds without human intervention or service disruptions. The event highlights the increasing prevalence of high-bandwidth, short-duration DDoS attacks that overwhelm targets before traditional mitigation methods can respond.
DDoS trends and attack vectors
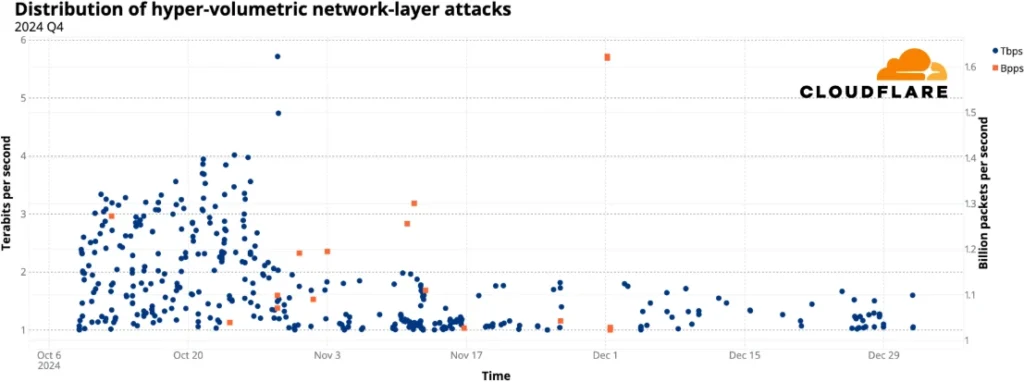
Cloudflare’s latest DDoS Threat Report provides a detailed analysis of attack trends observed in Q4 2024. Over the quarter, the company mitigated 6.9 million DDoS attacks, a 16% increase from the previous quarter and an 83% rise year-over-year.
Among these, hyper-volumetric attacks—exceeding 1 Tbps—grew by 1,885% compared to Q3 2024. Notably, 420 attacks surpassed 1 billion packets per second (pps), reflecting a shift toward high-intensity, rapid assaults.
Key observations from the report include:
- HTTP DDoS Attacks: Representing 51% of incidents, the majority originated from known botnets (73%), while others mimicked legitimate browsers (11%) or exploited suspicious HTTP attributes (10%).
- Layer 3/4 (Network) Attacks: The most common methods included SYN floods (38%), DNS floods (16%), and UDP floods (14%), with Mirai botnet variants driving a 131% increase in network-based attacks.
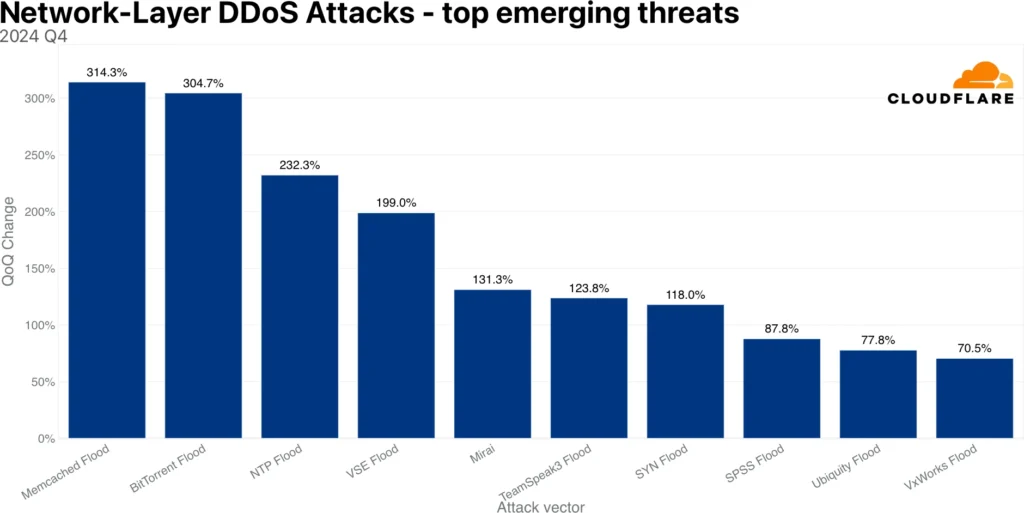
- Emerging Threats: Memcached-based amplification attacks surged by 314%, while BitTorrent-related DDoS abuse grew by 304%, demonstrating how attackers exploit network infrastructure vulnerabilities.
Geographically, Indonesia remained the leading origin of DDoS traffic for the second consecutive quarter, followed by Hong Kong and Singapore. Attackers continue to leverage botnets from high-density network regions, further complicating attribution efforts.
Regarding targeted sectors, the Telecommunications, Service Providers, and Carriers industry suffered the highest number of DDoS incidents in Q4 2024, overtaking Banking & Financial Services, which saw a significant drop. China remained the most attacked country, while the Philippines and Taiwan also emerged as primary targets.
A concerning rise in Ransom DDoS (RDDoS) attacks was also reported. In Q4 2024, 12% of targeted Cloudflare customers faced ransom demands, marking a 78% quarter-over-quarter increase. With heightened online activity during the holiday season, cybercriminals exploited this period to launch disruptive extortion campaigns.
Cloudflare’s analysis also uncovered new attack methodologies:
- User Agent Exploitation: Attackers predominantly used outdated Chrome versions (118-129) and HITV_ST_PLATFORM, a user agent linked to compromised smart TVs and set-top boxes, reinforcing concerns about IoT security.
- HTTP Methods and Paths: While legitimate traffic relied on GET (70%) and POST (27%) requests, 14% of HEAD requests and 7% of DELETE requests were associated with DDoS attacks. The /wp-admin/ path, used for WordPress administration, was the most targeted endpoint (98% malicious traffic).
Given the brevity of modern DDoS attacks—70% of HTTP-based assaults and 91% of network-layer attacks ended within 10 minutes—Cloudflare emphasized the necessity of always-on, automated defenses. The rapid execution of these attacks makes real-time human intervention impractical, necessitating AI-driven mitigation strategies.






Leave a Reply