
A critical flaw in Google's OAuth implementation could expose millions of Americans' sensitive data to attackers who purchase defunct domains of failed startups. This issue, which Google initially dismissed as “working as intended,” allows malicious actors to take over user accounts across various SaaS platforms using Google's “Sign in with Google” authentication flow.
The OAuth security loophole
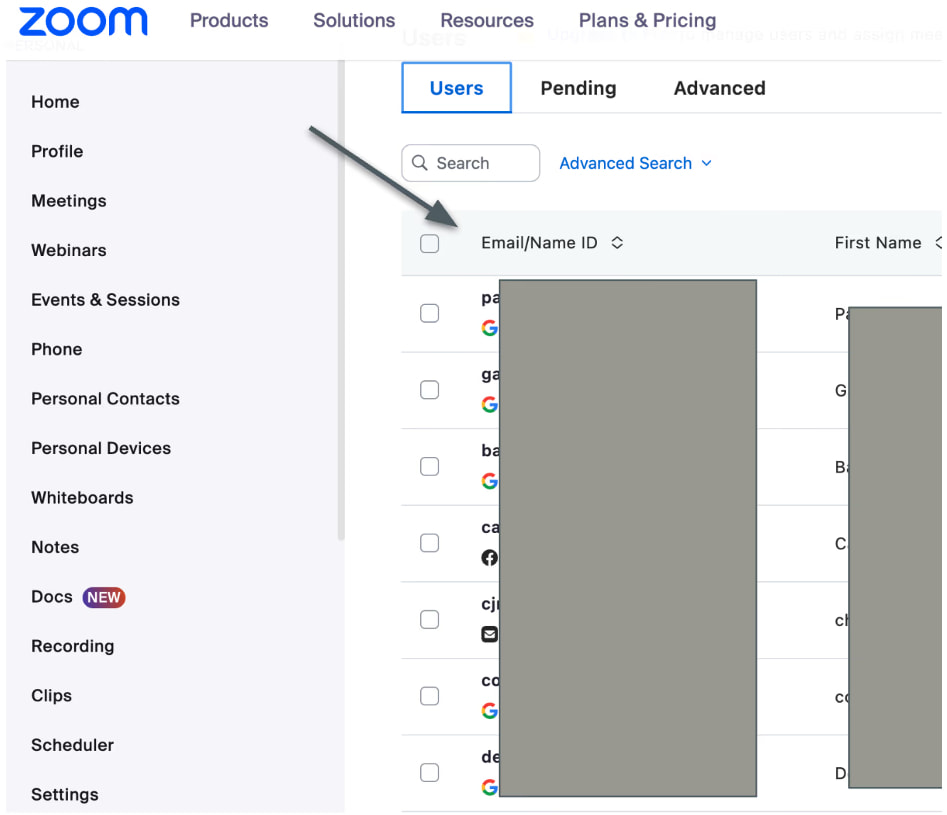
Security researchers at Trufflesecurity who discovered the flaw demonstrated its potential by purchasing the domain of a failed startup and using it to re-create email addresses for its former employees. Through Google's OAuth mechanism, these email accounts could then be used to log in to services like Slack, Notion, Zoom, HR systems, and other SaaS platforms without the need for the original user's credentials. This vulnerability stems from the way Google's OAuth protocol interacts with domain ownership.
Trufflesecurity
The key issue lies in the reliance of OAuth on domain-based claims, such as hd (hosted domain) and email, which verify user identity. When a domain is purchased by a third party, these claims remain valid and allow access to accounts tied to the domain, effectively bypassing safeguards. Even though the old email data cannot be accessed, the ability to log into connected services grants access to sensitive information such as:
- Social Security numbers and tax documents in HR systems.
- Confidential candidate feedback in interview platforms.
- Private messages and sensitive documents in chat tools like Slack and Notion.
The researcher demonstrated the issue to Google, but the tech giant initially classified it as a “fraud and abuse” issue rather than an OAuth vulnerability. However, after the researcher's talk on this flaw was accepted for Shmoocon, Google reopened the case, paid a $1,337 bounty, and began investigating a fix. As of writing, a fix hasn't been implemented yet, so the issue remains exploitable.
Millions at risk of exposure
Trufflesecurity highlights the following numbers in its report to reflect the staggering scale of the problem:
- Six million Americans currently work for tech startups.
- 90% of startups fail, leaving their domains vulnerable.
- 50% of these startups rely on Google Workspace for email and account management.
- Over 100,000 defunct domains were found available for purchase using Crunchbase's startup dataset.
With an average of 10 employees per startup using 10 SaaS tools, this vulnerability potentially affects over 10 million user accounts. Many of these accounts contain highly sensitive information, making them a lucrative target for attackers.
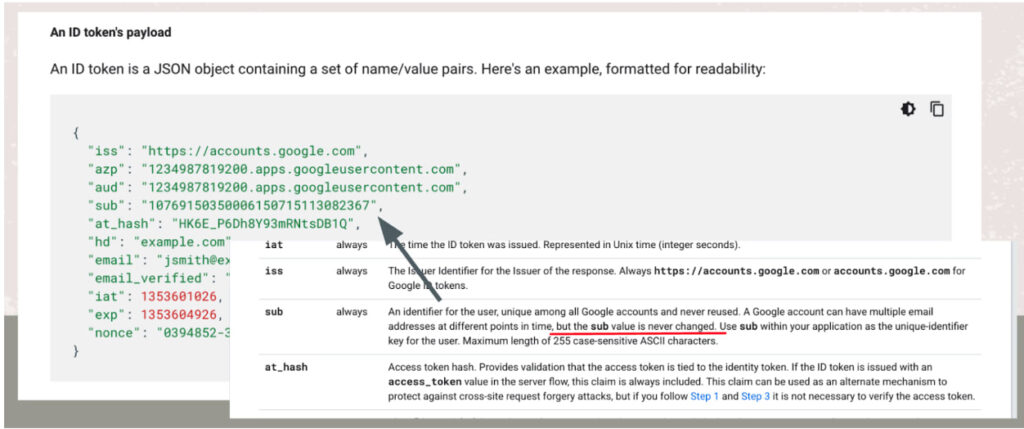
Google's OAuth framework includes a unique user identifier (sub claim) that could theoretically prevent this issue. However, this identifier is inconsistent in 0.04% of logins, making it unreliable for many downstream services. As a result, most SaaS providers rely on email and hd claims to verify accounts, both of which are compromised when a domain changes ownership.
Trufflesecurity
The researcher proposed a solution involving two immutable identifiers, namely a unique user ID that remains consistent over time and a unique workspace ID tied to the domain, ensuring continuity even if the domain changes ownership.
While Google has acknowledged the issue and is working on a fix, no specific details or timelines have been provided.
Beyond OAuth, re-acquired domains also expose users to password reset attacks. If accounts on SaaS platforms allow password recovery through email, attackers can use their control of the defunct domain to reset passwords and gain access. While this risk can be mitigated through two-factor authentication (2FA) and SSO enforcement, it highlights the broader risks of domain-based authentication models.
Until Google implements a permanent fix, both service providers and users can take steps to reduce the risk:
For SaaS providers:
- Require additional verification for domain-based logins (e.g., SMS codes or credit card verification).
- Implement stricter checks for domain ownership and changes.
- Transition to using unique, immutable user identifiers for authentication.
For startups and employees:
- Disable password-based authentication and enforce SSO with 2FA during operations.
- Offboard former employees properly, ensuring sensitive data is removed or secured.
- Monitor domains post-failure to prevent unauthorized ownership.







Leave a Reply