
Check Point Research (CPR) has uncovered a new version of the Banshee macOS Stealer, an advanced malware targeting macOS users since September 2024. This updated variant evades detection using encryption borrowed from Apple's XProtect system, posing significant risks to browser credentials, cryptocurrency wallets, and sensitive data.
The latest malware variant has operated undetected for over two months, exploiting phishing websites and fake GitHub repositories to distribute itself. It impersonates popular software such as Chrome and Telegram, targeting macOS users globally. CPR's discovery underscores the growing threat landscape for macOS, which now boasts over 100 million users worldwide.
How Banshee Stealer works
Banshee Stealer is a sophisticated malware capable of operating stealthily on macOS systems. It employs advanced techniques to infiltrate and exfiltrate data without detection. Its key features include:
- Targeting popular browsers like Chrome, Brave, and Edge, stealing login credentials and cryptocurrency wallet information.
- Using fake system pop-ups to trick users into revealing their macOS passwords.
- Adopting encryption from Apple's XProtect to evade antivirus detection and employing anti-debugging tools.
- Sending stolen data to command-and-control (C2) servers using encrypted and encoded files.
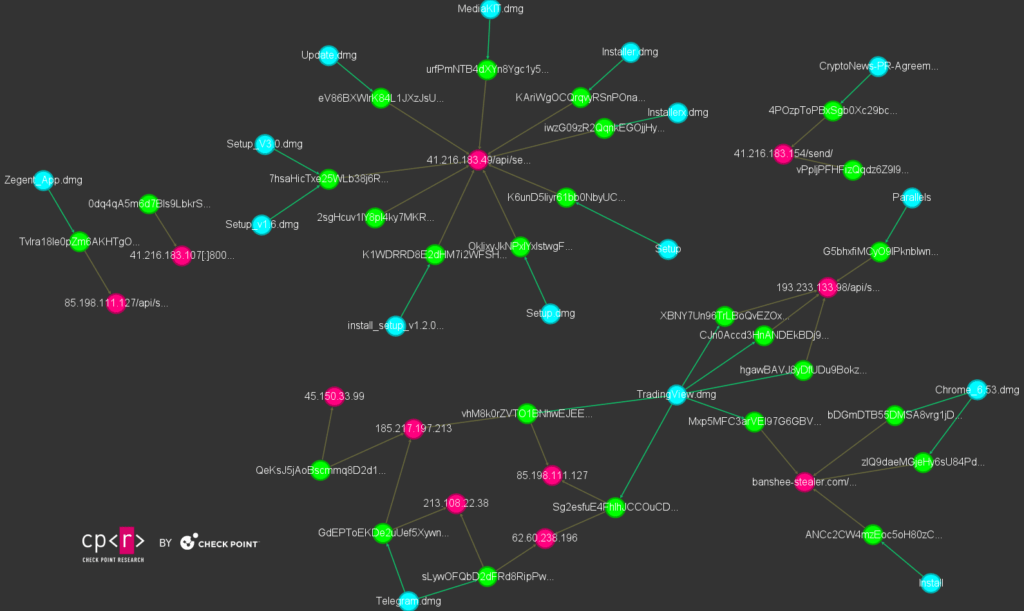
Banshee's distribution methods include phishing websites and malicious GitHub repositories designed to mimic legitimate software tools. These repositories are often well-crafted with fake stars and reviews to gain user trust before launching attacks.
Check Point Research
An expanded threat
First appearing in mid-2024 as a “stealer-as-a-service” on underground forums like XSS and Exploit, Banshee was marketed for $3,000, enabling cybercriminals to target macOS users. Its developers introduced a critical update in late 2024 by removing a Russian language check, thereby expanding its target base. Previously, the malware avoided systems set to Russian, potentially to evade law enforcement scrutiny in the region.
Banshee's operations faced a significant disruption in November 2024 when its source code leaked on underground forums. While this allowed antivirus engines to enhance detection capabilities, it also heightened the risk of new variants emerging from other threat actors, which is likely how the one spotted by CPR came into existence.
Check Point Research
Despite its shutdown as a service, ongoing campaigns leveraging Banshee indicate that threat actors remain active. CPR has observed clusters of phishing websites still distributing the malware, raising concerns about continued risks by the particular malware operation.







Wow