
A groundbreaking study conducted by researchers from Ruhr University Bochum sheds light on critical flaws in the way vulnerabilities are managed in Android smartphone chipsets.
The research reveals systemic delays in patching, significant gaps in transparency, and a widespread inheritance of vulnerabilities across chipset generations. These issues affect billions of devices globally, putting users at risk of exploitation.
Evaluating Android chipset security
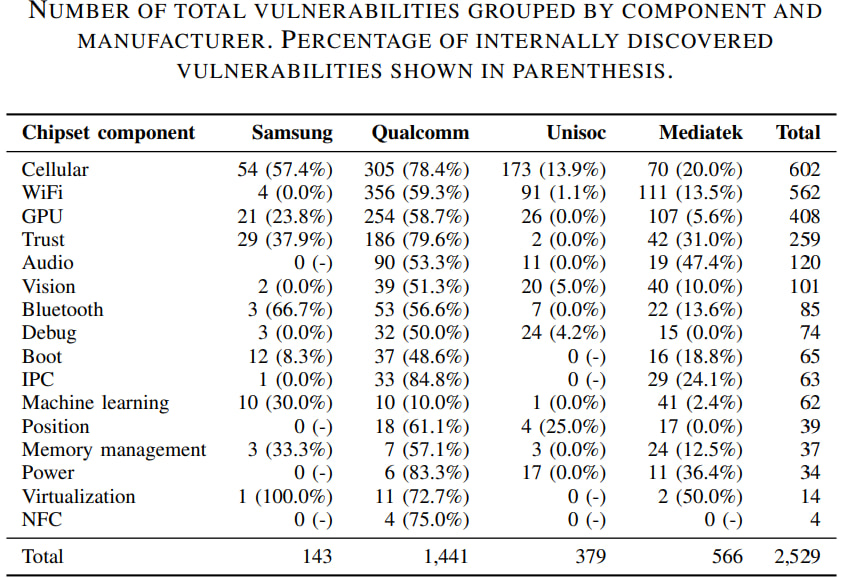
The research team conducted a comprehensive analysis of 3,676 vulnerabilities spanning 437 chipset models from the four major manufacturers — Qualcomm, Mediatek, Samsung, and Unisoc. Together, these companies dominate 99% of the smartphone chipset market. Their work included data from over 6,800 smartphone models, covering a substantial portion of the Android ecosystem.
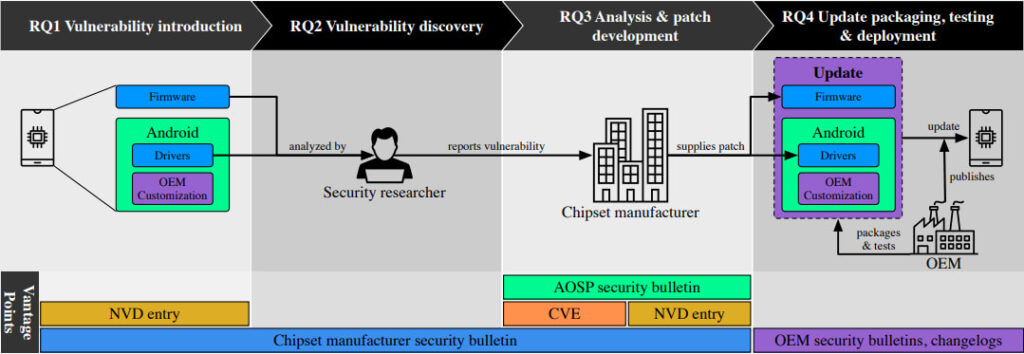
To understand the full lifecycle of chipset vulnerabilities, the team collected data from chipset manufacturer security bulletins, the National Vulnerability Database (NVD), and the Android Open Source Project (AOSP) security bulletins. This extensive dataset provided insights into how vulnerabilities are introduced, discovered, patched, and eventually reach end-users.
Vulnerability inheritance across generations
One of the study's most striking findings is the extent to which vulnerabilities are carried over across chipset generations. An overwhelming 93% of vulnerabilities in new chipsets are inherited from older models due to code reuse practices. While new chipsets tend to introduce some novel vulnerabilities — typically around 7% — the reuse of older code significantly increases the cumulative risk.
Delays in patching further exacerbate this pattern. The study found that only 9% of vulnerabilities are resolved before the next chipset generation is released, meaning that most vulnerabilities persist across multiple generations. These findings underline the systemic nature of the issue, as the very foundation of modern chipset design prioritizes continuity over proactive security fixes.
Arxiv.org
Delays in patching
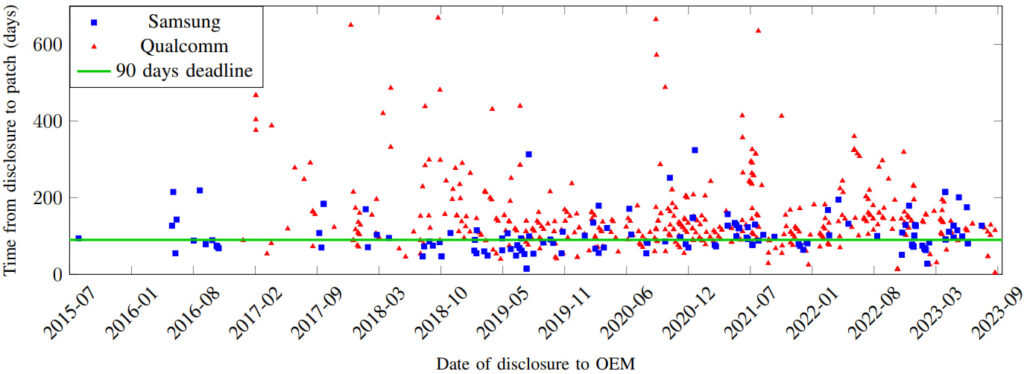
The study revealed that Qualcomm and Samsung, the two largest chipset manufacturers, frequently fail to adhere to the industry-standard 90-day responsible disclosure period for patching vulnerabilities. Qualcomm, for instance, patched less than 20% of vulnerabilities within the 90-day window, while Samsung managed 47%. Some vulnerabilities took over a year to be resolved, with outliers stretching into several years.
Mediatek and Unisoc, which cater to budget and mid-tier smartphone markets, had a different challenge. Their internal discovery rates were strikingly low, with external researchers accounting for the vast majority of identified vulnerabilities. Qualcomm, by contrast, discovered 57% of its vulnerabilities internally, highlighting a significant disparity in the internal security practices across chipset manufacturers.
Arxiv.org
Incomplete and inconsistent update information
Another critical finding was the inconsistency in communicating vulnerability updates. While vulnerabilities discovered by Qualcomm and Samsung are often reported in multiple databases, including the AOSP security bulletins, this is not the case for Mediatek and Unisoc. The study found that over 75% of vulnerabilities affecting their chipsets were missing from AOSP bulletins.
This lack of transparency poses a major problem for end-users, as AOSP bulletins are a primary source of information for determining whether a device has received a security update. In addition, many vulnerabilities affecting Android devices appear to have never been addressed. For example, 41% of vulnerabilities in the study dataset showed no evidence of being included in any updates or changelogs, leaving end-users unaware of whether their devices remain exposed.
Broader implications
Android is the dominant mobile operating system worldwide, holding a 70.5% market share. The four chipset manufacturers analyzed — Qualcomm, Mediatek, Samsung, and Unisoc — power the vast majority of Android devices, spanning from premium flagship models to budget-friendly options.
Chipsets are critical components in modern smartphones, as they handle sensitive operations, including storing cryptographic keys and processing unencrypted data. The exploitation of these vulnerabilities can have severe consequences.
The research highlights that vulnerabilities in chipsets typically impact hundreds to thousands of smartphone models, with ripple effects felt across the entire Android ecosystem. In one instance, a single Mediatek vulnerability affected over 2,200 smartphone models — a stark example of the widespread consequences of chipset security lapses.
The study underscores the urgent need for systemic improvements in chipset vulnerability management on Android. With billions of devices reliant on these technologies, the current gaps in patching, transparency, and communication represent significant risks to user privacy and security.







Leave a Reply