
Cybersecurity researchers at Trellix Advanced Research Center have unearthed Celestial Stealer, a novel Malware-as-a-Service (MaaS) offering targeting Windows 10 and 11 systems. This JavaScript-based infostealer is sold via Telegram and is designed to harvest sensitive user data from browsers, cryptocurrency wallets, and popular applications such as Discord and Steam.
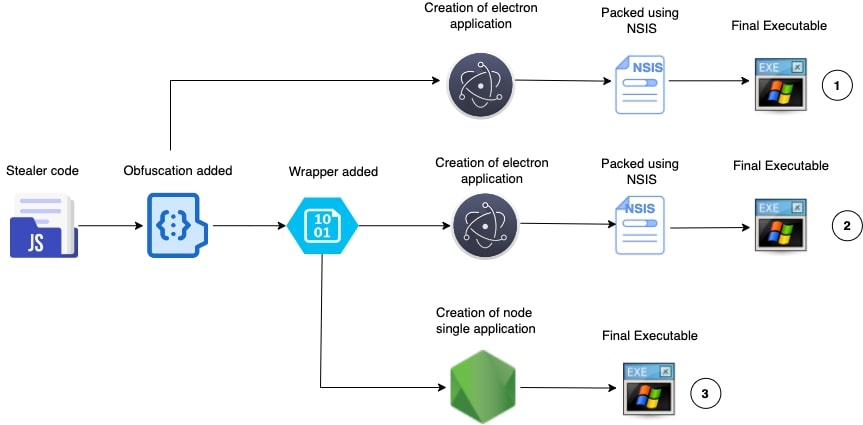
Celestial Stealer came to light during proactive threat-hunting efforts. Its distribution methods include packaging as Electron or NodeJS applications and leveraging heavily obfuscated JavaScript to remain undetected. Trellix researchers investigating the new malware revealed a range of anti-analysis techniques and capabilities aimed at circumventing detection tools and complicating forensic analysis.
Trellix
Celestial Stealer's functionality and tactics
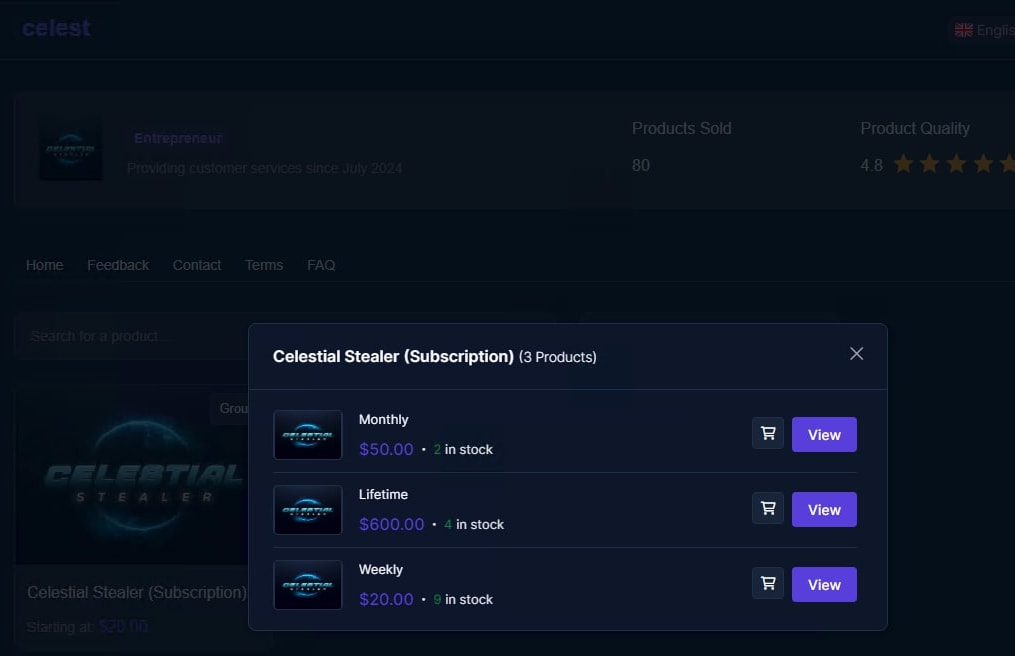
Celestial Stealer offers subscription-based services — weekly, monthly, or lifetime — marketed through Telegram groups and bots. Subscriptions allow users to customize the malware's capabilities via a Telegram bot, enabling attackers to tailor their payloads. Notably, the malware is advertised as “Fully Undetectable” (FUD) and is continuously updated to bypass detection by security tools.
Trellix
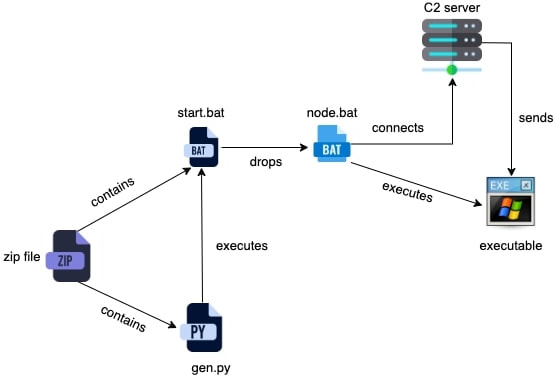
Key infection vectors include:
- Discord Promotion Generator: Fake tools embedded with malicious scripts execute the stealer payload via a series of obfuscated commands and scripts.
- VRChat NSFW Application: Deceptively labeled as adult content for VRChat, this vector lures victims into running an executable that deploys the stealer.
Trellix
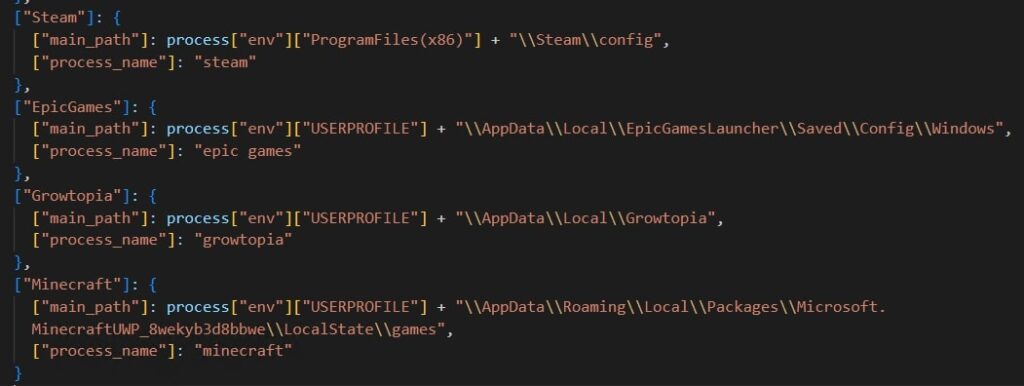
Celestial Stealer primarily focuses on stealing data from:
- Browsers: It extracts cookies, saved passwords, credit card information, and browsing history from Chromium and Gecko-based browsers.
- Cryptocurrency Wallets: It targets well-known wallets like Exodus, Atomic, and Binance.
- Applications: Telegram, Discord, Steam, and other gaming and communication platforms.
- Exodus and Discord Payload Injection: The malware downloads payloads to inject into these applications, enabling it to intercept user credentials and manipulate app behavior.
Trellix
Additional features include anti-VM and anti-sandbox techniques, file exfiltration using multiple channels, and system persistence via the Windows startup folder.
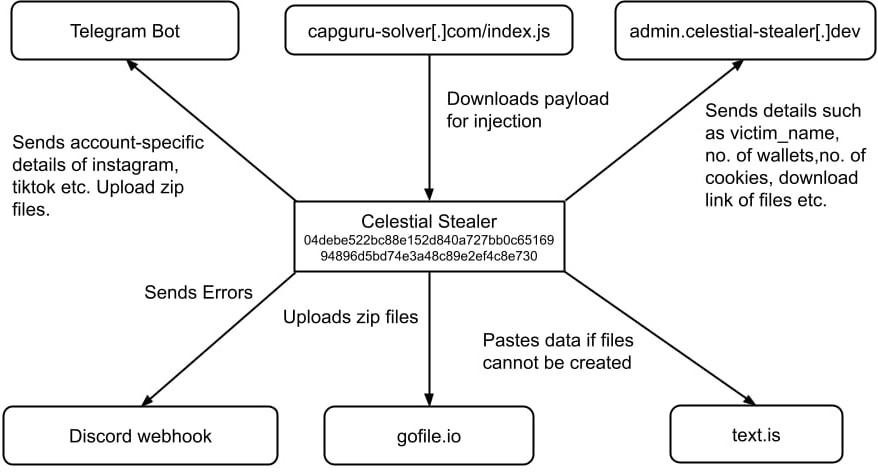
Trellix
The malware is operated via Telegram channels, which are used for advertising, user support, and sharing updates. It is sold on platforms like Sellix.io, with payments accepted through cryptocurrency and gift vouchers. The service also provides a “lite” version, stripping out advanced capabilities like persistence and payload injection to cater to less sophisticated attackers.







Wow , I always assumed attacks like this were possible . I just didnt ( still dont really ) understand how they worked . This article gave me a child like understanding of it .