
Since Windows expanded native support for additional archive formats in November 2023, cybercriminals have increasingly used unconventional file types to bypass Secure Email Gateways (SEGs) and deliver malware. This trend, highlighted in a recent Cofense report, demonstrates how attackers adapt their tactics to exploit new vulnerabilities in enterprise security measures.
Exploiting archive file formats
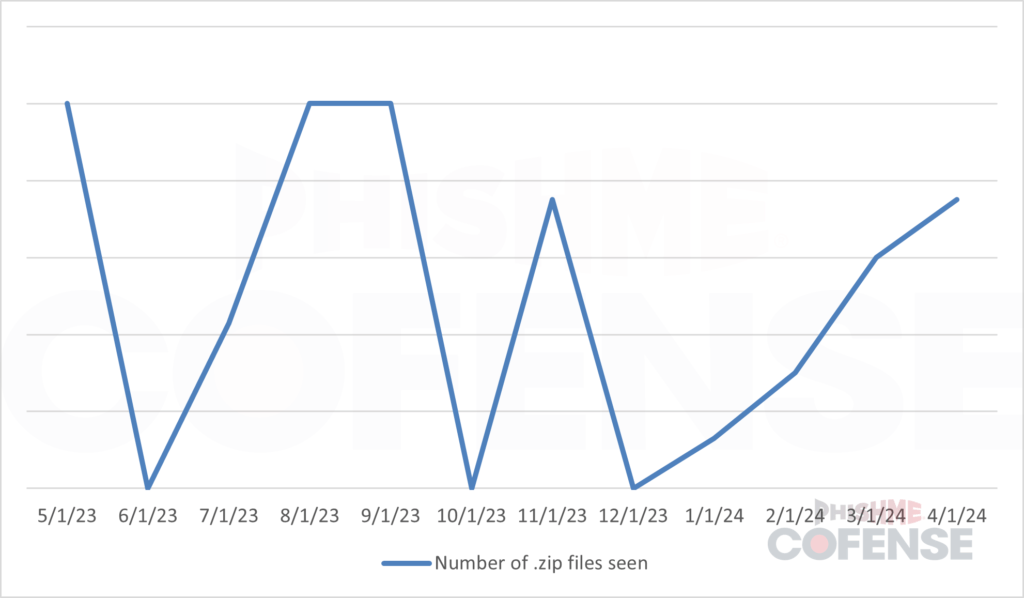
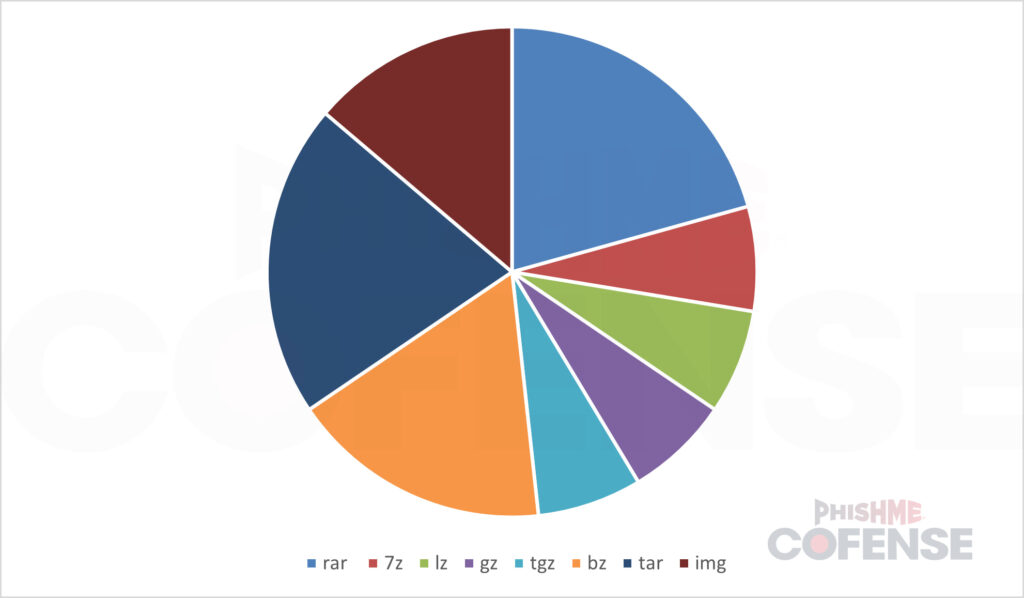
Cofense Intelligence analyzed data from May 2023 to May 2024 to understand how the new Windows functionality has impacted malware delivery via email attachments. While .zip files remain the most common format, representing over 50% of all observed malicious archives, threat actors have embraced newer formats like .rar, .7z, .tar, and .gz, which are now natively supported on Windows systems. These formats accounted for over half of non-.zip archives analyzed during the study.
Cofense
Attackers frequently mislabel these files to disguise their true nature, further complicating SEG defenses. Many SEGs fail to correctly identify these mislabeled formats, allowing malicious archives to slip through undetected. The report also notes that some SEG and Endpoint Detection and Response (EDR) tools lack the sophistication to analyze the true file type, rendering them ineffective against such tactics.
Cofense
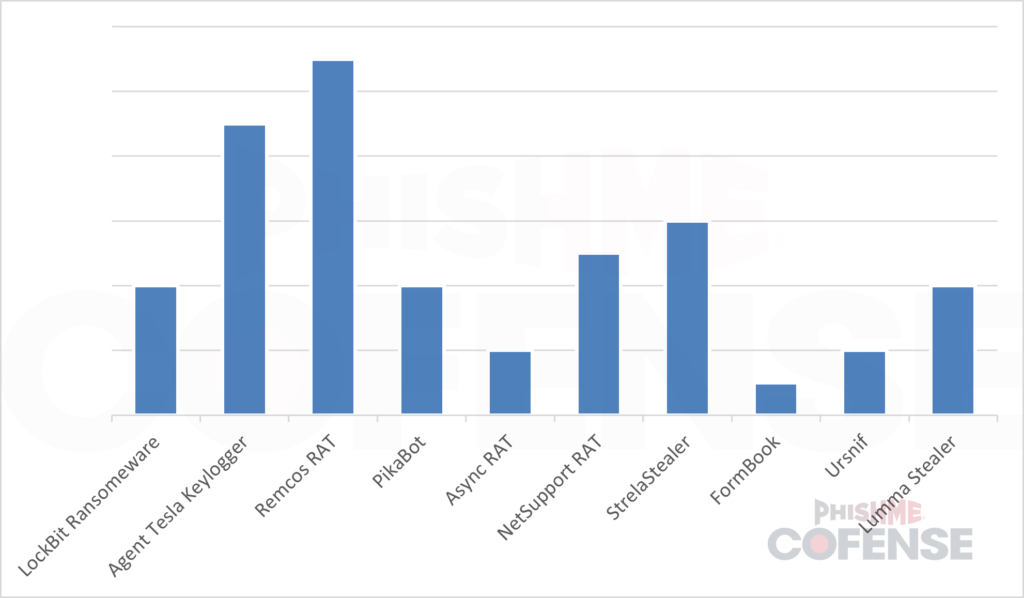
Threat actors deliver a variety of malware families through these archives, often leveraging .zip files for their versatility and near-universal compatibility across operating systems. Among the most frequently delivered malware are information stealers like StrelaStealer and remote access trojans (RATs) such as NetSupport RAT, both of which rely heavily on .zip archives.
Key trends highlighted include:
- Password-protected archives: About 5% of malicious archives were password-protected, a tactic used to bypass SEG content scanning. The password is typically included in the body of the email.
- Shift in archive types post-Windows update: A significant uptick in formats like .rar and .7z occurred after Microsoft rolled out native support for these types in October 2023. Before this update, such formats were rarely seen in SEG-protected environments.
Other archive formats, such as .img, .iso, and .vhd, were rarely observed as direct email attachments. These formats are often delivered through alternative mechanisms like embedded URLs. This reduced prevalence may be attributed to more stringent SEG filtering policies for such less-common file types, as they serve little legitimate purpose in email communications.
Cofense
Defending tips
To mitigate the risks posed by malicious archive files, organizations should adopt a multi-layered security strategy:
- Update SEG and EDR configurations to ensure these tools can accurately detect and analyze archive file types, even when mislabeled.
- Restrict certain file types and block email attachments with uncommon or unnecessary file extensions (.iso, .img, etc.).
- Strengthen password-protection detection by means of AI-driven tools to identify and flag emails containing archive files and potential passwords in the same message.
- Train staff to recognize phishing attempts and avoid opening unexpected file types.







Leave a Reply