
Researchers from cybersecurity firm OneKey have uncovered severe vulnerabilities in eCharge EV charging station controllers, allowing unauthenticated attackers to remotely execute arbitrary commands. The vulnerabilities, tracked as CVE-2024-11665 and CVE-2024-11666, expose critical risks for both local and wide-area networks.
The research highlights insecure design choices and negligent software practices that leave both the physical devices and their associated cloud infrastructure open to compromise. Despite efforts to report these issues, researchers describe the disclosure process as frustratingly ineffective, with poor communication from eCharge Hardy Barth GmbH and inconsistent patching of devices in the field.
eCharge Hardy Barth GmbH is a provider of EV charging station controllers widely used in Europe.
Despite their broad customer base, their failure to address critical vulnerabilities promptly has left over 313 devices exposed on the Internet, according to OneKey. Additionally, the lack of an automatic update mechanism means many devices remain on outdated, vulnerable firmware versions.
The company released partial fixes in April 2024 and more comprehensive patches in May 2024, but OneKey states that the disclosure process was fraught with delays and poor coordination. No public advisories or customer notifications were issued, further compounding the risks.
Uncovering critical vulnerabilities
The vulnerabilities were first highlighted by Offensity, which discovered authenticated remote command execution issues in the cPH2 charging stations manufactured by eCharge Hardy Barth GmbH. Building on this, OneKey’s researchers downloaded the firmware for analysis using their PHP static analysis tool. This led to the identification of several alarming flaws, including unauthenticated command execution, insecure communication channels, hardcoded credentials, and leaked cloud infrastructure data.
To deepen their analysis, the team emulated the full system using the raw filesystem and kernel extracted from the firmware. They identified three main attack surfaces:
- Web administration interface – Weakly secured PHP scripts allow unauthorized access.
- MQTT broker and connected clients – No authentication required, enabling full device control.
- Internet communications – Insecure firmware update mechanisms and cloud interactions.
The vulnerabilities identified in the said systems are now tracked as follows:
- Local Network Command Execution (CVE-2024-11665) – Attackers on the same LAN can exploit vulnerable PHP scripts to execute commands as root due to improper input validation and lack of authentication. Affects systems running firmware versions ≤ 2.0.4.
- Remote Command Execution (CVE-2024-11666) – Devices communicate with the cloud over insecure channels, enabling man-in-the-middle (MitM) attacks to inject malicious commands, due to SSL peer verification being disabled across the firmware. Affects systems running firmware versions ≤ 2.0.4.
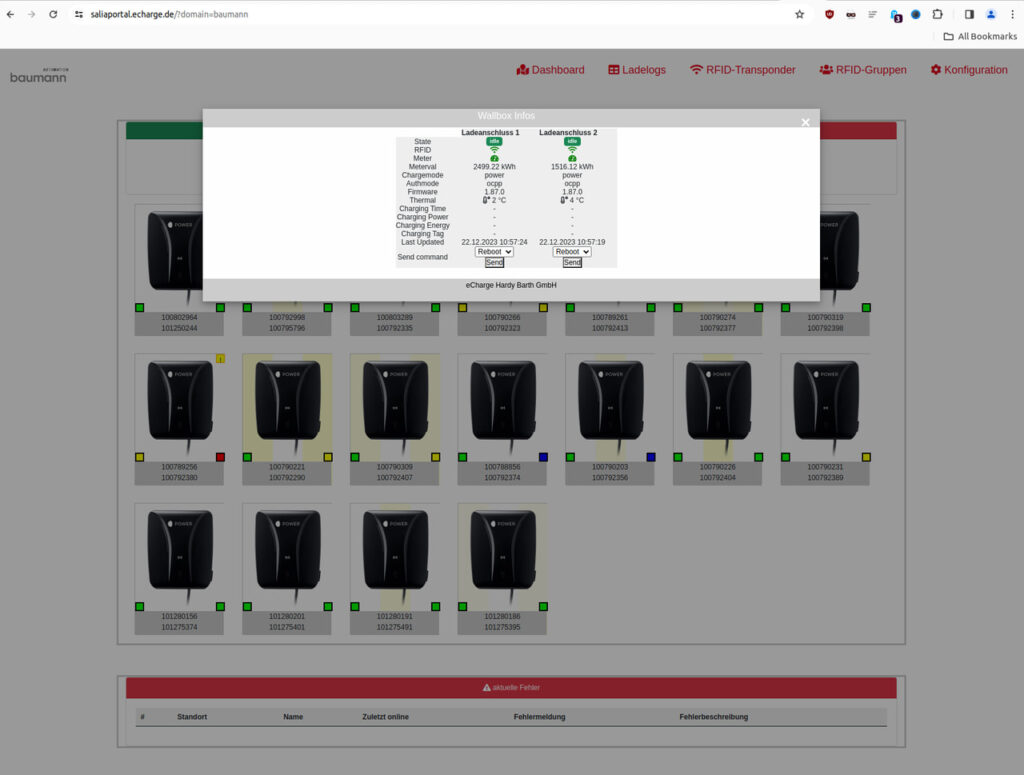
OneKey
- Hardcoded Credentials and Infrastructure Leaks – Embedded SSH keys and plaintext SMTP/API credentials expose all devices to remote access. Directory listings in the cloud infrastructure reveal sensitive device and customer data. Weak multi-tenant protections enable cross-customer data access.
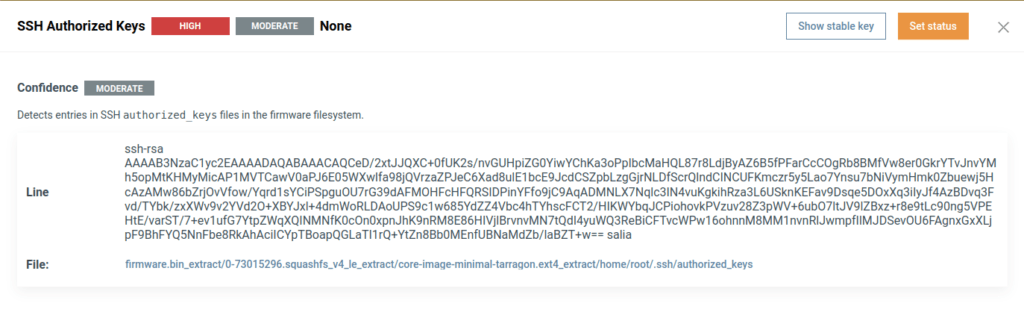
OneKey
Recommendations for mitigation
To minimize exposure to these vulnerabilities, OneKey recommends the following immediate actions for users of eCharge devices:
- Place the devices behind firewalls and restrict access to trusted networks only.
- Explicitly block connections to eCharge cloud infrastructure unless required for updates.
- Upgrade to the latest firmware versions (≥ 2.2.0). Verify fixes are applied to address known vulnerabilities.
- Shut down unused network services like MQTT to reduce the attack surface.
For organizations considering new EV charging station solutions, OneKey advises conducting rigorous penetration testing on firmware prior to deployment.







Leave a Reply