
Black Lotus Labs at Lumen Technologies has unveiled critical insights into the NSOCKS botnet, powered by the ngioweb malware. This criminal proxy network spans 180 countries, exploiting over 35,000 bots daily, primarily small office/home office (SOHO) routers and IoT devices, with two-thirds of its proxies located in the United States.
NSOCKS is implicated in supporting malicious activities such as phishing, credential stuffing, and DDoS attacks, with infrastructure that enables both criminal groups and individual threat actors to obfuscate their identities.
The ngioweb botnet and NSOCKS operations
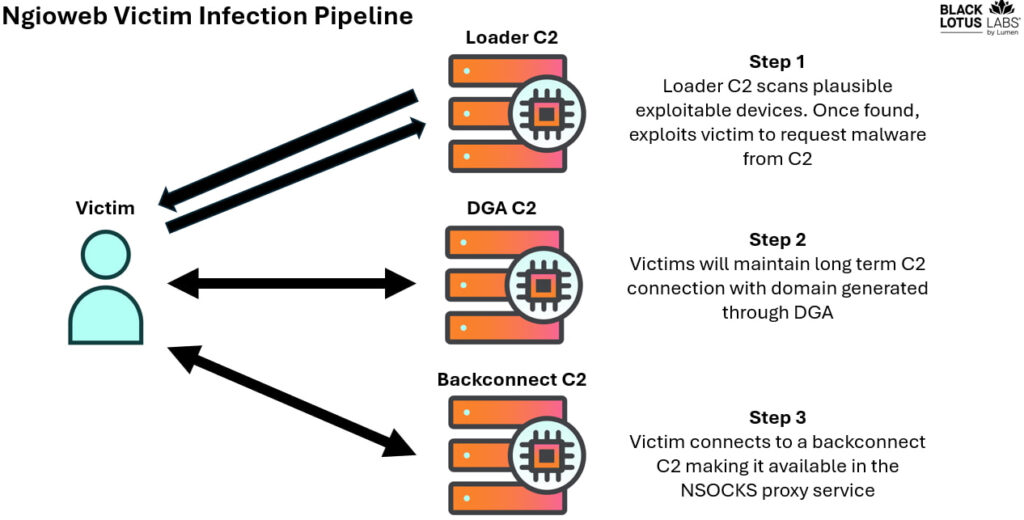
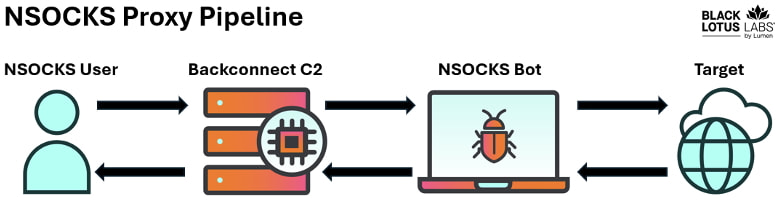
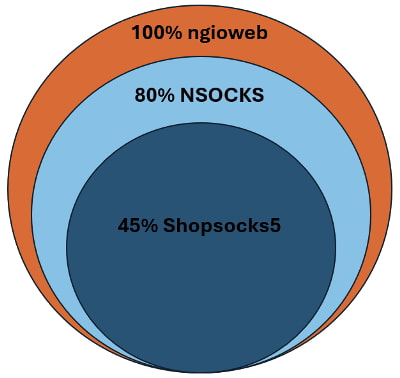
The NSOCKS proxy service is heavily reliant on the ngioweb botnet, with 80% of observed NSOCKS bots sourced from ngioweb. The botnet operates through a multi-tiered architecture that includes loader command-and-control (C2) nodes and domain generation algorithm (DGA)-generated domains to manage bots. Once a device is infected, it communicates with backconnect C2 nodes that facilitate malicious traffic routing through the proxy network.
Black Lotus Labs
Black Lotus Labs observed that ngioweb primarily infects outdated devices, exploiting known vulnerabilities in Zyxel routers, Reolink cameras, and Alpha Technology hardware. These devices, though older, often evade detection due to limited security measures.
A criminal marketplace
NSOCKS emerged in late 2022, succeeding the LuxSocks proxy service, and is frequently promoted in underground forums like Blackhatworld. The service allows users to rent proxies by the day and pay in cryptocurrency. Its user-friendly interface enables filtering by country or specific domains such as .gov or .edu, which facilitates highly targeted attacks. Key use cases include reconnaissance, fraud, and spam campaigns.
Black Lotus Labs
Additionally, NSOCKS supports broader cybercrime ecosystems, with an overlap in bot usage among other proxy services like Shopsocks5 and VN5Socks. Approximately 45% of ngioweb bots are sold through Shopsocks5, indicating a shared infrastructure that extends the network’s reach.
Black Lotus Labs
Disruption and defending
Lumen Technologies has proactively blocked traffic associated with ngioweb infrastructure and shared indicators of compromise (IoCs) to assist other organizations in mitigating the threat. Shadowserver Foundation has also begun sinkholing ngioweb DGA domains and offering public dashboards and remediation reports.
However, this disruption and its effects are expected to be short-lived, so more action is required to defend against the botnet and make its re-emergence as hard and slow as possible.
Corporate defenders are recommended to monitor for weak credential attacks and block suspicious login attempts, even from residential IPs. Additionally, they should use web application firewalls to block bots attempting password spraying, regularly update IoCs, and block IPs linked to known open proxies.
For consumers and SOHO router users, it is recommended to regularly reboot and apply firmware updates (when available), avoid default passwords, and ensure device management interfaces are secured. Finally, when devices reach end-of-life, they should be replaced immediately.







Leave a Reply