
Cristian Cornea, a cybersecurity expert, devised a clever honeypot trap to ensnare hackers using a fake ransomware builder. Cornea’s “Jinn Ransomware Builder,” while appearing to offer all the tools necessary to launch custom ransomware attacks, was actually backdoored, designed to collect the information of would-be cybercriminals who tried to use it.
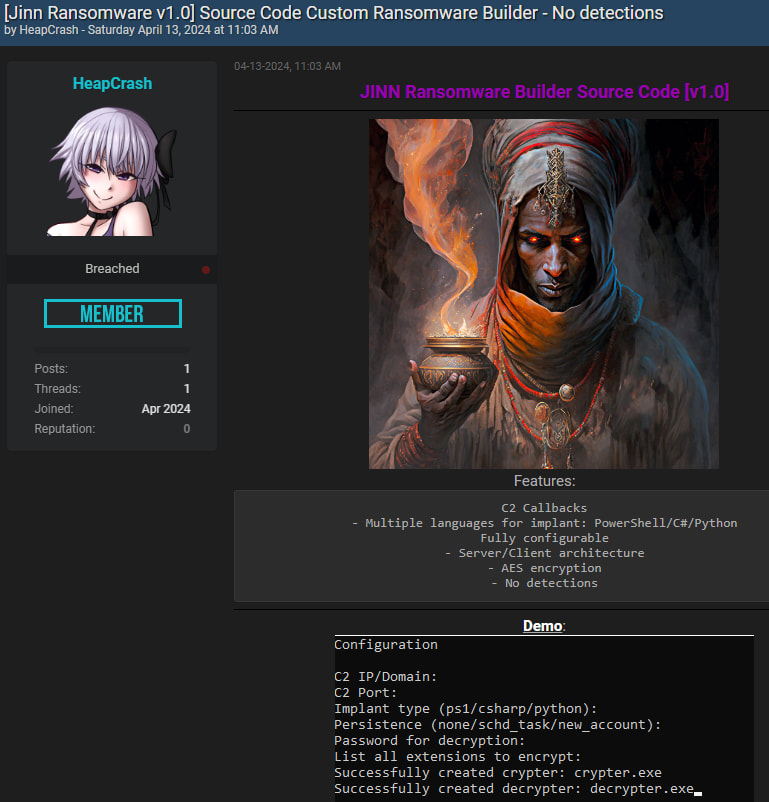
The Jinn Ransomware Builder was marketed on BreachForums as a fully-featured ransomware builder capable of creating customized malicious payloads, with claims of functionality including Command and Control (C2) callbacks, AES encryption and decryption, multi-language support across PowerShell, C#, and Python, and zero-detection capabilities.
Cornea’s aim was to draw in script kiddies and low-level hackers seeking an easy path to ransomware deployment. Unbeknownst to them, the builder came with hidden code that would leak identifying information back to Cornea’s controlled servers, essentially enabling him to “hack” the hackers.
The fake builder worked by implanting backdoors and using a method called _Tiger in the code. This method initialized a backdoor connection by starting a command process “CmD.eXE,” a spoofed command that let Cornea’s servers gain insight into the users’ IP addresses and other potentially identifying data.
Once an unsuspecting user ran the tool, it began sending back this information, revealing the approximate location and system details of each user. Over a short period, the tool accumulated over 100 C2 connections as various users tested the builder, unwittingly exposing themselves.
Cristian Cornea’s ruse gained considerable traction, placing it in the top ranks of BreachForums, a well-known space for threat actors of all levels. His insights from the campaign highlight the risks hackers themselves face when they attempt to use unvetted tools.
CyberInsider
In the source code, Cornea implemented incomplete AES encryption functions and added fake options that would appear sophisticated to untrained eyes, yet offered no real functionality. This approach hid the backdoor logic while making the ransomware builder appear legitimate enough to evade scrutiny by inexperienced hackers.
Cornea’s project is both a lesson in vigilance and a stark reminder of the ethical considerations in cybersecurity. Though the honeypot was used only in a controlled environment without targeting actual users, it demonstrates how cybercrime tools can easily backfire on attackers. His experience suggests that zero-detection rates on VirusTotal or other scanning tools do not guarantee safety, as threat actors can still hide malicious code designed to target even those who attempt to use it.
To safeguard against falling into similar traps, Cornea advises security practitioners and enthusiasts to:
- Analyze source code rigorously for any new exploit or hacking tool downloaded.
- Look for suspicious IP addresses or ports embedded in the code.
- Check for functions that initialize unexpected connections or execute remote commands.
- Approach zero-detection ratings skeptically, as this could signal the presence of new or well-hidden backdoors.






Leave a Reply