
Cisco Talos researchers have identified eight vulnerabilities in various Microsoft applications for macOS, potentially allowing attackers to hijack user-granted permissions and exploit them for malicious purposes.
These vulnerabilities could be leveraged to perform unauthorized actions, such as accessing the camera, microphone, or sensitive files, without the user's knowledge.
macOS security background
The flaws were discovered by Cisco Talos‘ security team during an in-depth analysis of macOS applications and the platform's permission-based security model, which relies heavily on the Transparency, Consent, and Control (TCC) framework.
Apple’s macOS utilizes the TCC framework alongside a Discretionary Access Control (DAC) policy to protect user data and system resources. The TCC system manages permissions by requiring user approval before applications can access sensitive resources. Entitlements further regulate what an app can do, and sandboxing restricts apps to only the resources they have explicitly requested access to.
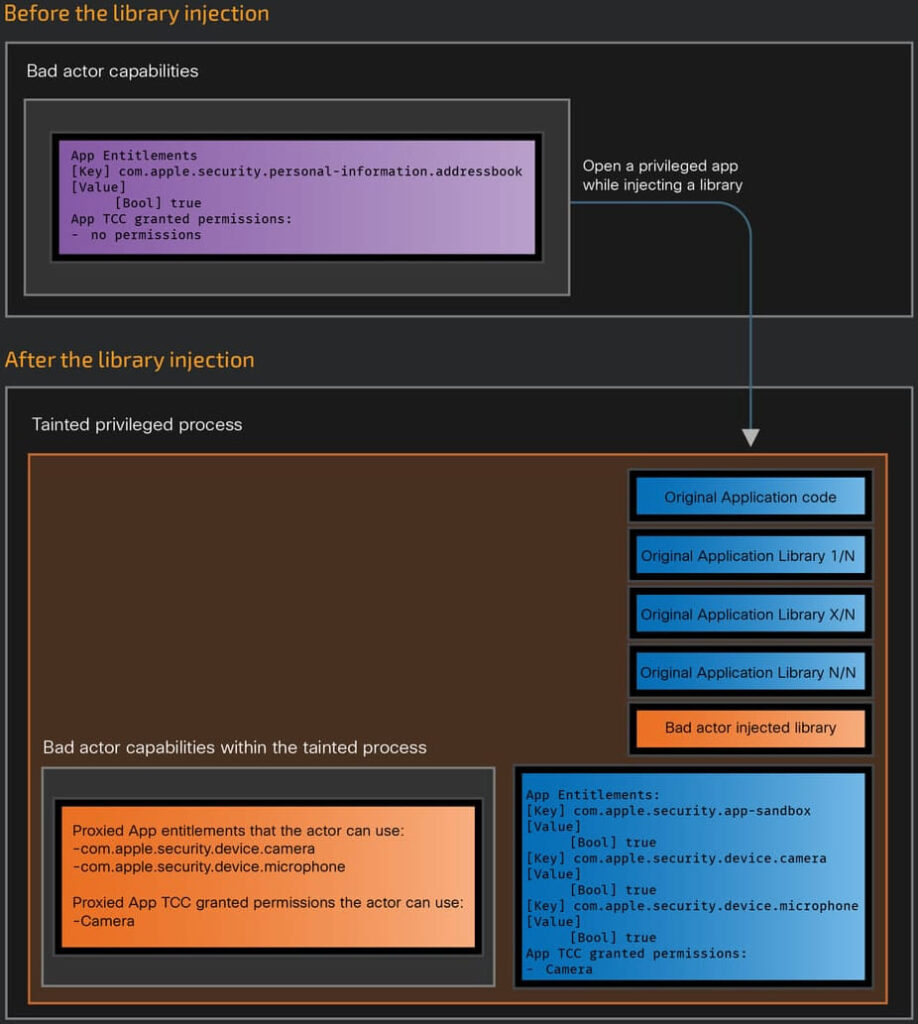
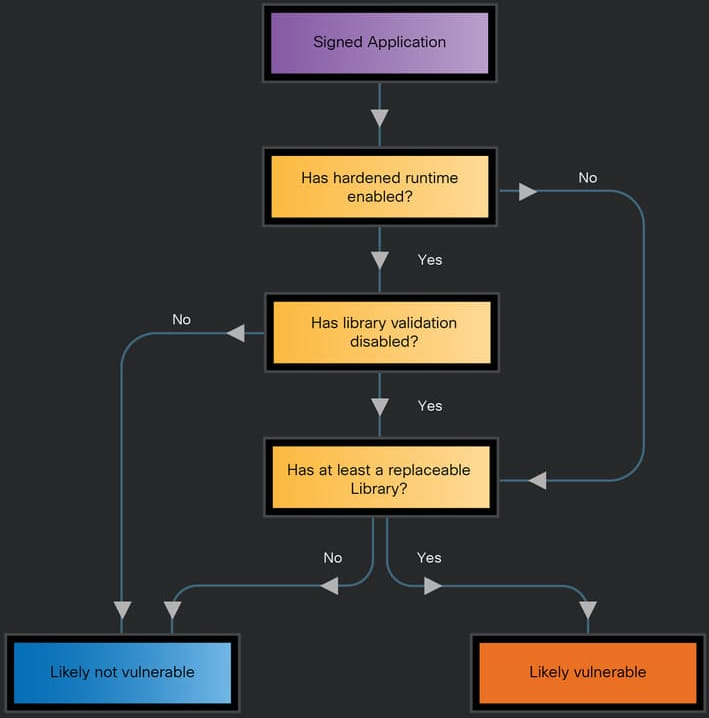
However, these protections can be undermined if an attacker successfully injects malicious code into an application with sufficient permissions. Cisco Talos highlighted that many Microsoft macOS applications use the com.apple.security.cs.disable-library-validation entitlement, which disables the hardened runtime’s default protection against code injection. This entitlement allows the loading of unsigned libraries, potentially opening the door for attackers to exploit the app's entitlements and permissions.
Cisco Talos
Impact
The affected applications include widely used programs such as Microsoft Outlook, Teams, Word, Excel, PowerPoint, and OneNote. Cisco Talos has released detailed information about these vulnerabilities, which have been assigned CVE identifiers.
The affected versions of these applications can be exploited if an attacker successfully injects a malicious library, effectively gaining the permissions granted to the compromised application. This would allow the attacker to perform actions like sending emails, recording audio, or accessing the camera without the user’s awareness.
The vulnerabilities are tracked as follows:
- Microsoft Outlook: TALOS-2024-1972 (CVE-2024-42220)
- Microsoft Teams (work or school): TALOS-2024-1973 (CVE-2024-42004)
- Microsoft PowerPoint: TALOS-2024-1974 (CVE-2024-39804)
- Microsoft OneNote: TALOS-2024-1975 (CVE-2024-41159)
- Microsoft Excel: TALOS-2024-1976 (CVE-2024-43106)
- Microsoft Word: TALOS-2024-1977 (CVE-2024-41165)
- Microsoft Teams (work or school) WebView.app helper app: TALOS-2024-1990 (CVE-2024-41145)
- Microsoft Teams (work or school) com.microsoft.teams2.modulehost.app: TALOS-2024-1991 (CVE-2024-41138)
Microsoft won’t fix
Microsoft has categorized these vulnerabilities as low-risk, stating that certain applications require the loading of unsigned libraries to support plugins. Consequently, the company has declined to fix these issues for most affected applications, although they did update some, including Microsoft Teams and OneNote, to remove the risky entitlements.
These updates have addressed the vulnerabilities in those apps by eliminating the problematic com.apple.security.cs.disable-library-validation entitlement, which allowed the loading of unsigned dynamic libraries.
Cisco Talos
Although Microsoft considers these issues low risk, the presence of the com.apple.security.cs.disable-library-validation entitlement in some applications leaves them vulnerable to serious exploits. Users and organizations using Microsoft Office apps on macOS should remain vigilant and consider the risks posed by these vulnerabilities. While some applications have been updated to address the issue, others remain susceptible.
To mitigate these risks, users should:
- Ensure that all Microsoft applications are updated to the latest versions where possible.
- Restrict permissions granted to applications, particularly those not regularly in use.
- Consider alternative software solutions where appropriate, especially for high-security environments.
- Monitor for any unusual application behavior that may indicate an exploit attempt.







Leave a Reply