A groundbreaking study from the Indian Institute of Technology Delhi has unveiled significant privacy vulnerabilities in Android devices, dubbed AndroCon, demonstrating how semi-processed GPS data can be covertly exploited to gather detailed environmental information, track human activity, and map indoor spaces with alarming accuracy.
The findings, presented in a technical paper late last month underscore the potential for widespread misuse of location services by malicious actors, affecting up to 90% of Android users globally.
AndroCon overview
The research was led by Soham Nag and Smruti R. Sarangi, who conducted an extensive longitudinal study over the course of a year. They gathered semi-processed GPS data across a vast 40,000 sq. km area, including diverse environments such as flights, cruise ships, and high-altitude locations. The data was collected using various Android devices equipped with different GPS chipsets.
The researchers leveraged this data to develop “AndroCon,” a method that utilizes machine learning (ML) algorithms to transform semi-processed GPS signals into a powerful tool for ambient sensing, human activity recognition, and indoor mapping.
Arxiv
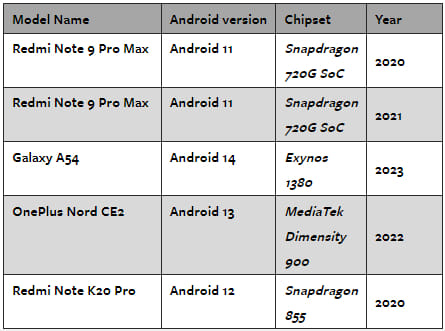
Traditionally, GPS-based sensing was limited to basic location and signal strength data. However, since the release of Android 7, apps with precise location permissions can access a wealth of semi-processed GPS data, including 39 features such as signal strength, Doppler shifts, and signal-to-noise ratio (SNR).
AndroCon exploits this data to achieve high accuracy in detecting various environmental contexts and human activities, even in challenging scenarios like metro tunnels or crowded areas.
Arxiv
Impact on user privacy
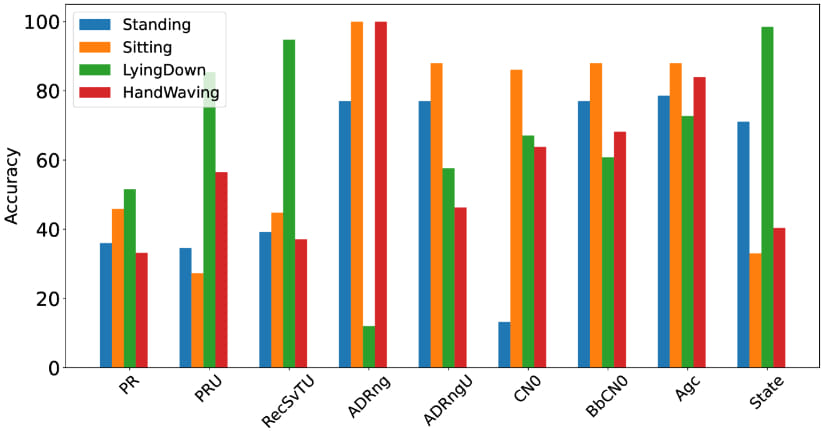
The study highlights that the semi-processed GPS data accessible to apps can be used for much more than just location tracking. By analyzing this data, AndroCon can determine whether a user is indoors or outdoors, moving or stationary, in a crowded space, or even in proximity to specific landmarks like staircases or elevators.
The method achieves a remarkable 99.6% accuracy in detecting environmental contexts and 87% accuracy in classifying human activities.
Arxiv
More concerning is AndroCon's ability to map indoor layouts with an error margin as small as 4 meters. This capability poses a significant privacy threat, as it allows attackers to reconstruct detailed floor plans of buildings without needing access to other sensors like cameras or accelerometers. This could enable malicious entities to track users' movements within buildings, identify private meetings, or even target specific individuals within crowded environments.
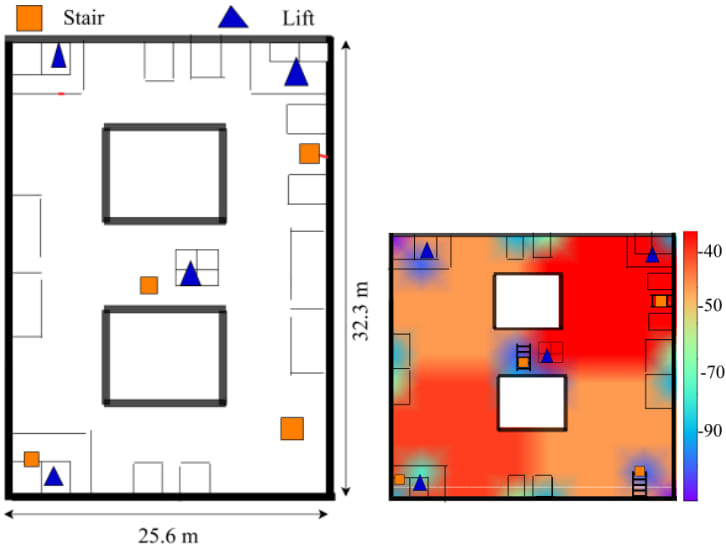
Arxiv
Broader implications for Android
This discovery reveals a critical oversight in Android's location services, leaving a vast majority of users exposed to potential privacy breaches. The researchers emphasize that this vulnerability persists even when a device is in flight mode or all communication channels are disabled, as long as apps retain access to the GPS data.
Despite Android's recent improvements in user permissions—such as the introduction of options to limit location precision—many users remain unaware of the risks posed by granting apps access to precise location data. This gap in awareness, coupled with the lack of clear disclosures in Android's official documentation, exacerbates the threat.
To mitigate these risks, the researchers recommend that Android users restrict apps to coarse location permissions whenever possible, especially for non-critical applications. Additionally, they urge Google to enhance the transparency of permission requests and provide clearer guidelines to developers and users regarding the potential privacy implications of semi-processed GPS data.
The study's findings have been responsibly disclosed to the Android security team, who acknowledged the concerns and are investigating the matter further. However, the researchers caution that until Android implements stronger safeguards, users must remain vigilant about the permissions they grant to apps.







I’m not surprised by this. Even if you disable Google’s enhanced location services, Android still leaks your actual location. I’ve tested this using various mock location apps and by running a VPN simultaneously.
While these methods can hide your location on Google Maps, they are not effective with more privacy-invasive apps like WeChat, which can bypass these protections.
As an experiment, I suggest team Alex and Heinrich run comprehensive tests using similar apps. In particular, try using the “People near me” feature, and you’ll quickly see that your actual location is revealed.
@Optimus your testing is interesting.
You think with cell phones the Sim, either hard or esim types send your location. Then isn’t the AI-centric tech guts of the phones picking up that location for recording a devices location for AI purposes. That the mock location apps fail on?
Maybe this plays into it as well.
Wi-Fi routers constantly broadcast their network name (SSID) and MAC address.
Your phone periodically sends probe requests to nearby Wi-Fi networks, including the router’s MAC address and your device’s own MAC address.
These probe requests can be intercepted by nearby routers and sent to a central database, allowing the tracking of your device’s location.