
Flaws in several popular home WiFi mesh networks allow guest users to retain network access indefinitely, access sensitive data, and even execute commands on connected devices.
The issues, which stem from weaknesses in the synchronization of network access policies (NAPS) across multiple devices in a mesh network, were discovered by researchers from the University of California, Riverside, who presented their findings during the recent Black Hat conference. The implications of these vulnerabilities are severe, posing risks to both network integrity and user privacy.
Attack methodology
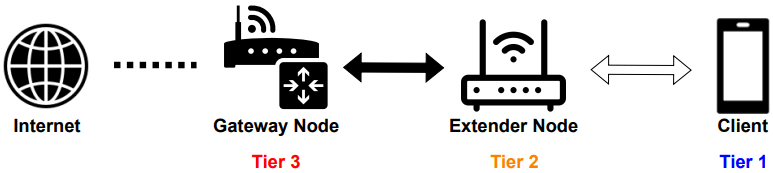
The attack exploits how mesh networks synchronize network access policies between the gateway and extender nodes. Typically, in a mesh network, the gateway node is the central authority that manages network access, and extender nodes, which expand the network's reach, rely on the gateway to enforce these policies. However, flaws in how different vendors implement this synchronization process create opportunities for malicious actors.
cs.ucr.edu
In practice, an attacker with guest access to the network could exploit these flaws to:
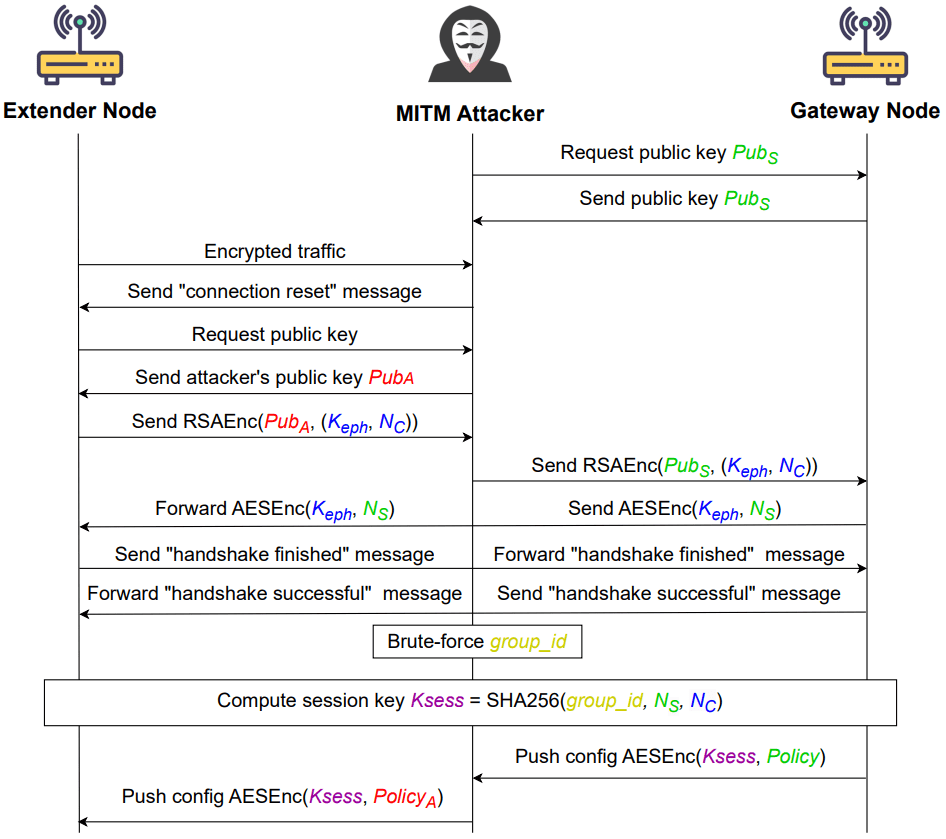
- Retain network access: Even after the network owner revokes access by changing the WiFi password, the attacker can maintain access by intercepting and decrypting updated credentials.
- Execute commands: In some cases, attackers can obtain shell access to the network devices, allowing them to execute arbitrary commands, potentially compromising the entire network.
- Intercept and manipulate traffic: Attackers can redirect traffic within the network, inspect sensitive data, and manipulate it for malicious purposes.
cs.ucr.edu
These vulnerabilities are primarily due to poor coordination across different protocol layers, where the trust established in lower layers (such as the link layer) does not carry over to higher layers (such as the NAPS protocols). As a result, malicious clients can masquerade as legitimate devices within the network.
cs.ucr.edu
Impact and vendor response
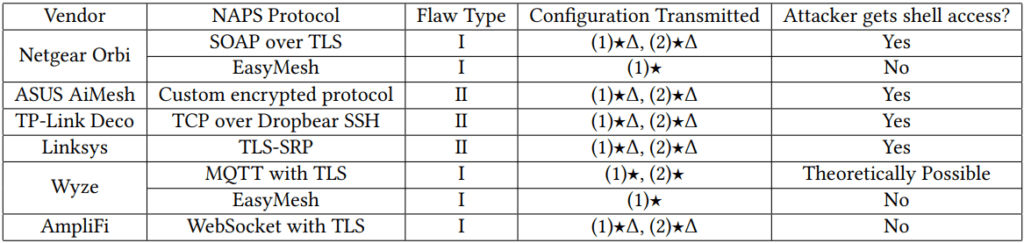
The researchers tested six popular mesh network products, including those from major vendors like Netgear, ASUS, TP-Link, Linksys, Wyze, and AmpliFi. The impact on each vendor varies, with some implementing partial fixes while others are still vulnerable.
- Netgear Orbi: Netgear's Orbi devices were found to use self-signed certificates for TLS connections between devices, making them susceptible to man-in-the-middle attacks. While Netgear has released patches, the underlying issue of insecure certificate handling remains a concern.
- ASUS AiMesh: ASUS devices were vulnerable due to weak cryptographic practices and poor implementation of network policy synchronization. Despite issuing patches, the fixes do not address all possible attack vectors, leaving users at risk.
- TP-Link Deco: TP-Link's Deco series relied on weak RSA keys for SSH authentication between devices, making it easy for attackers to gain unauthorized access. TP-Link has not yet fully addressed this issue.
- Linksys Velop: Linksys devices were found to store passwords in clear text and were vulnerable to command injection attacks. Although patches have been released, the reliance on outdated cryptographic practices raises concerns about the overall security posture.
- Wyze and AmpliFi: Both Wyze and AmpliFi were found to use insecure methods for managing MQTT communications, making it possible for attackers to impersonate devices and intercept communications. Wyze has acknowledged the issue but has yet to release a comprehensive fix.
Recommendations
The discovery of these vulnerabilities highlights the critical need for vendors to implement robust and coordinated security measures across all layers of network communication. Users of affected mesh networks are advised to apply the latest firmware updates provided by their vendors and to monitor their networks for any unusual activity.
Users of Wyze and AmpliFi WiFi mesh products that do not have the option to apply security updates should be aware of the risks and take precautions to limit risky guest connections.







Not surprised by aimesh as expressway its predecessor never really disappeared & is still causing stability issues for non-zen routers.
Amplifi has been eol by ubi for years