
Tens of millions of credentials obtained from info stealer logs were posted to Telegram channels and misused to extort companies for bug bounties by falsely claiming the data originated from their services, according to a report by Troy Hunt, creator of Have I Been Pwned (HIBP).
Scott Helme of Report URI was one of the affected individuals who received a concerning email titled “Bug bounty Program – PII leak Credentials more than 170.” The email alleged that a substantial number of user credentials and sensitive documents linked to Report URI had been leaked and were publicly accessible. The sender attached a text file containing 197 lines of email addresses and passwords, sparking immediate concern that Report URI had been compromised.
Report URI is a web monitoring and reporting service that provides security-related reports for websites. Founded by Scott Helme, the service has become a trusted resource in the cybersecurity community. The incident highlights the increasing sophistication and frequency of scams targeting such services.
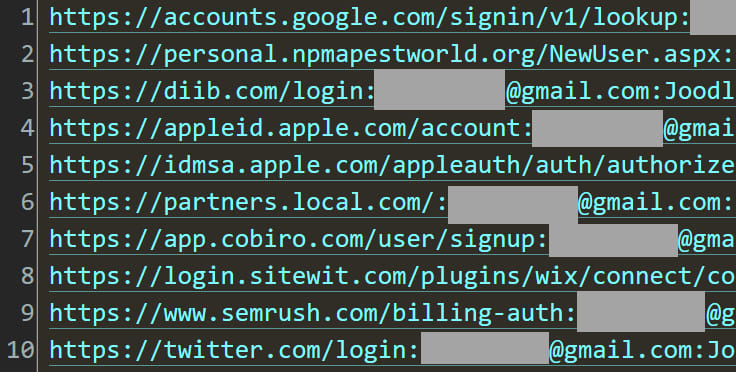
Upon closer investigation, Hunt and Helme discovered that the credentials did not result from a breach of Report URI. Instead, they originated from info stealer logs, data collected by malware from infected users’ machines. These logs are typically harvested by malware that captures data as users fill out online forms. The stolen information is then logged on the attacker’s server, hence the term “info stealer logs.”
Mechanics of the scam
The email sent to Helme followed a common scam pattern, where supposed “security researchers” use automated tools to identify vulnerabilities and then seek bounties under false pretenses. In this case, the email claimed severe repercussions due to the alleged leak, such as mass account takeovers, exposure of sensitive data, unauthorized transactions, and financial and reputational damage. However, by cross-referencing the email addresses in the “breach” with data from HIBP, Hunt quickly identified a pattern indicating that the credentials came from stealer logs already known to HIBP.
To illustrate this, Hunt examined the original data source and found that the email addresses in the file sent to Helme appeared in stealer log files, not in a breach of Report URI. This verification process confirmed that the malicious actor was attempting to extort a bug bounty by leveraging previously stolen credentials.
In the broader context, the discovered stealer logs contained 26,105,473 unique email addresses and were part of a 22GB data dump found on Telegram channels. Hunt noted that 89.7% of these addresses had been seen in previous data breaches, meaning nearly 2.7 million were new to HIBP. This underscores the ongoing threat posed by malware and the extensive reach of cybercriminal networks.
Troy Hunt
Data added to HIBP
HIBP added the compromised accounts to its platform today. This means that impacted individuals will receive notifications via email so they can take appropriate action to protect themselves from the exposure.
For companies, this incident serves as a reminder to stay vigilant against extortion attempts masquerading as bug bounty reports. Key defensive measures include:
- Verify any claims of data leaks against known data breach repositories like HIBP.
- Train staff to recognize and respond to phishing attempts and scam emails.
- Implement robust monitoring systems to detect unusual login attempts or account takeovers.
- Ensure all endpoints are protected with up-to-date anti-malware solutions.
Ultimately, Hunt’s report highlights the dual scams at play—victims having their credentials stolen and malicious actors attempting to extort organizations using that stolen data.







Leave a Reply