
Threat actors have claimed a data breach against multinational tech giant General Electric, leading to accessing confidential information relating to the U.S. government defense R&D agency DARPA.
General Electric designs and manufactures aerospace tech, such as aircraft engines, and has a long-term partnership with DARPA, collaborating on various projects concerning advanced materials research, energy, and electronics used in defense applications.
The hackers, who belong to the notorious ‘CyberNiggers’ group, previously attempted to sell their alleged SSH and SVN access onto the networks of the two organizations, but after failing to find a suitable buyer, they decided to sell all data they had exfiltrated leveraging that access.
Samples of the data posted yesterday on a popular clearnet hacking forum include SQL database files, military documents, aviation systems technical descriptions and guides, and maintenance reports.
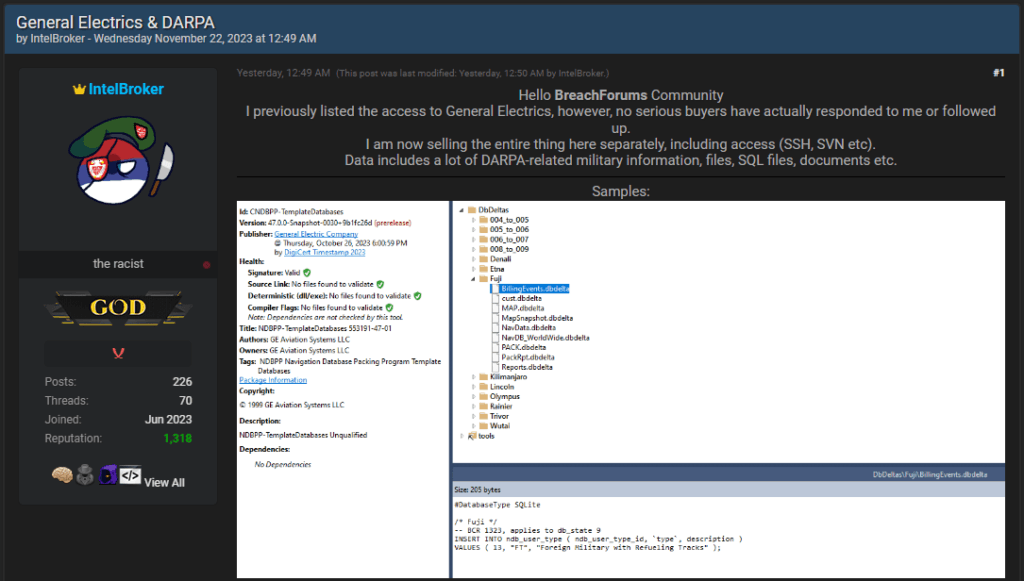
The seller has not specified how much data they hold and hasn’t set a selling price publicly. Instead, interested buyers are directed to contact the seller privately.
RestorePrivacy has emailed General Electric to ask about the authenticity of the leaked samples and the validity of the threat actor’s claims, but a response wasn’t immediately available.
Dynamic return
It is worth noting that the user selling the alleged General Electic data is IntelBroker, a member of the ‘CyberNiggers’ group. The threat actor is known for previously leaking datasets belonging to large companies such as Autotrader, Volvo, Hilton Hotels, Verizon, AT&T, and the U.S. Immigration Service. These successive breaches and data leaks raised attention by law enforcement.
This heat was a bit more than they would like another leading member of the cybergang explained in a forum post yesterday, so they had to lay low for a while. The period of idleness has now ended, and the group announced they are back in full action.
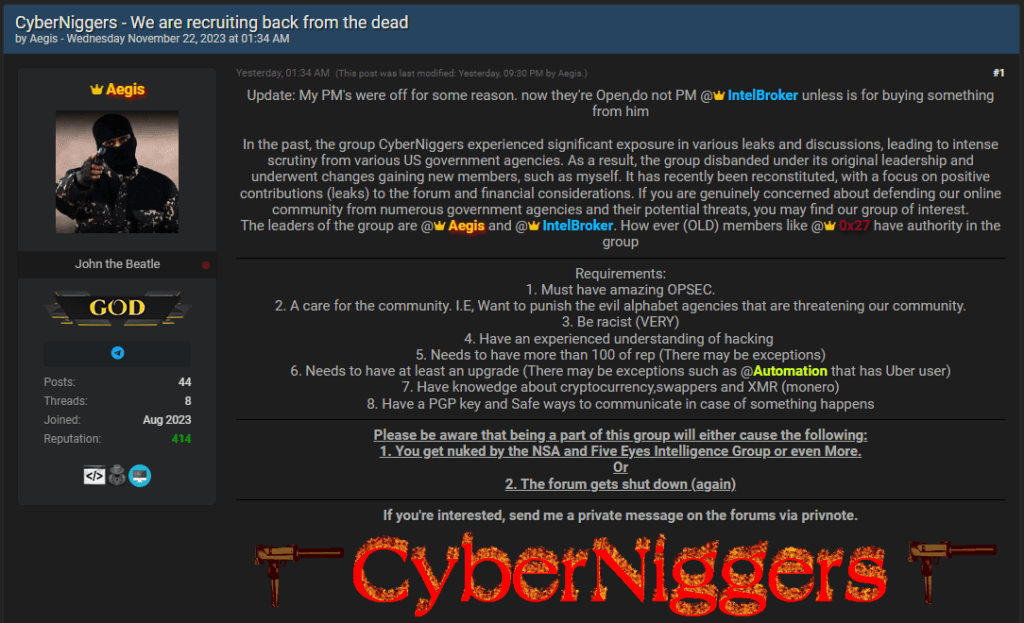
The threat group is looking to recruit new members with exceptional OPSEC skills, a community spirit, a racist mentality, knowledge about Monero and crypto swapping, and knowledge of secure communications based on the use of PGP keys. This signifies a return for the cybercriminals, which could produce more high-profile data leaks in the upcoming weeks/months.
KitchenPal attack
Another claimed attack by IntelBroker and ‘CyberNiggers’ concerns the Android meal prep planning app ‘KitchenPal,’ which has 100k downloads on Google Play.
On Monday, the data broker posted on the forums, offering to sell a KitchenPal database containing the following information in 146,000 lines:
- User ID and Username
- Full name and Profile picture
- Email address
- Hashed password
- Gender
- Language, Country, and Provider
- Apple ID, Facebook ID, Google ID, and Firebase ID
- BMI, Height, and Weight
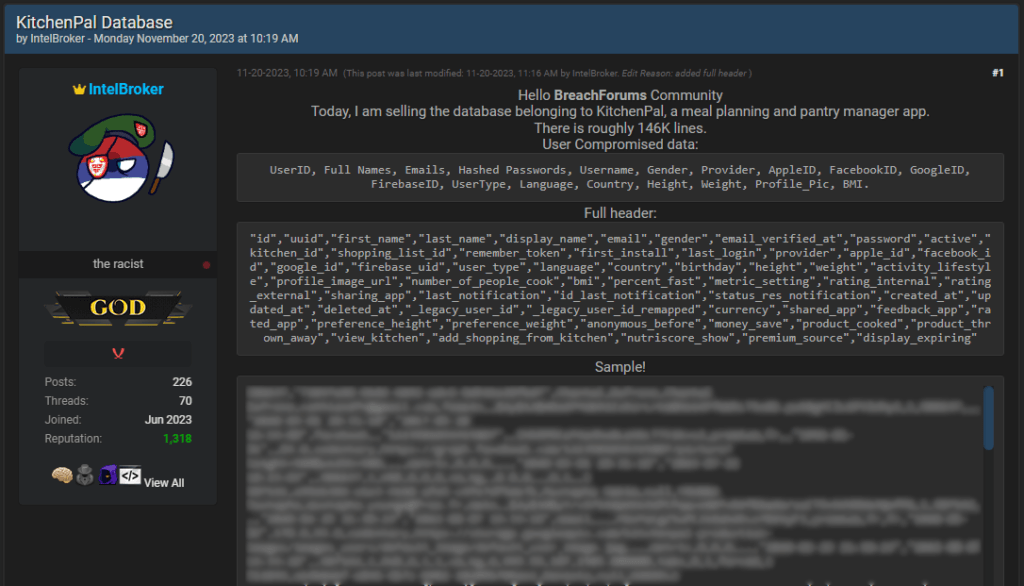
The threat actor also posted a hefty sample to back the data breach claims, exposing the sensitive personal data of 28 people, including full names, email addresses, gender, and other details.
RestorePrivacy has contacted the developer of KitchenPal with a relevant query. In an email to RestorePrivacy, KitchenPal confirmed there was an attempted attack on their servers earlier this week, resulting in limited user data exposure.
While we have rectified the problem because of which this hack occurred, we are also running a system-wide audit again to ensure there are no other vulnerabilities. We are also in the process of reaching out to users whose data may have been compromised in any manner.– KitchenPal’s statement to RestorePrivacy







Leave a Reply