
The BlackBerry Research and Intelligence Team has identified a sophisticated .NET banking Trojan, named “Coyote,” which is targeting Brazilian financial institutions.
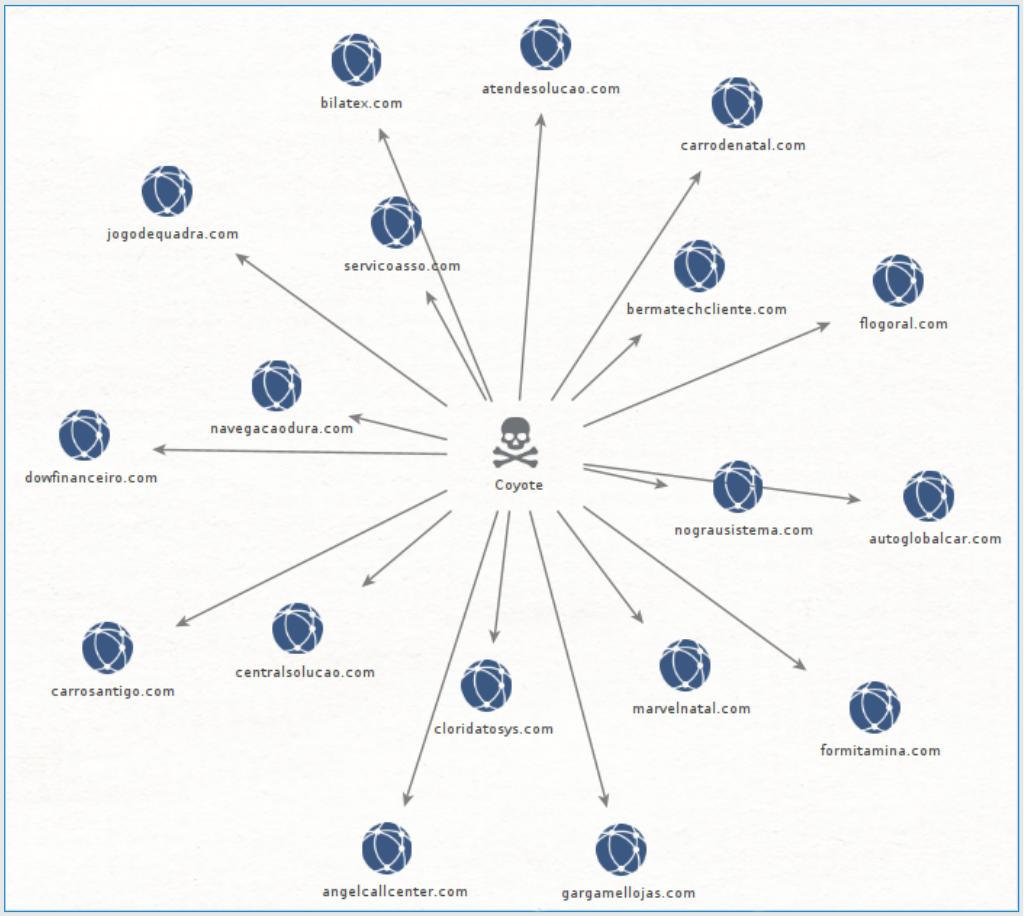
Coyote targets several major Brazilian financial institutions and cryptocurrency exchanges, including Banco do Brasil, Bradesco, Santander, Itaú, and Binance. The full list of targeted domains comprises over 50 financial and cryptocurrency platforms, emphasizing the threat's extensive reach and potential impact.
Coyote operation details
BlackBerry first identified the Coyote Trojan in February 2024, naming it for its abuse of the Squirrel software, a legitimate tool for managing Windows application updates. The Trojan injects a compromised dynamic link library (DLL) into legitimate files, using the Nim programming language to load the malware and steal user financial information while maintaining persistence on the infected system.
Coyote is typically delivered via phishing attacks, where users are tricked into clicking a malicious link. The Trojan's large file size (over 170 MB) makes it impractical to send as an email attachment.
Upon execution, the malware initiates the Squirrel update process, running commands that eventually load a compromised DLL. This DLL, chrome_elf.dll, acts as a Nim loader to execute the Coyote banking Trojan in memory.
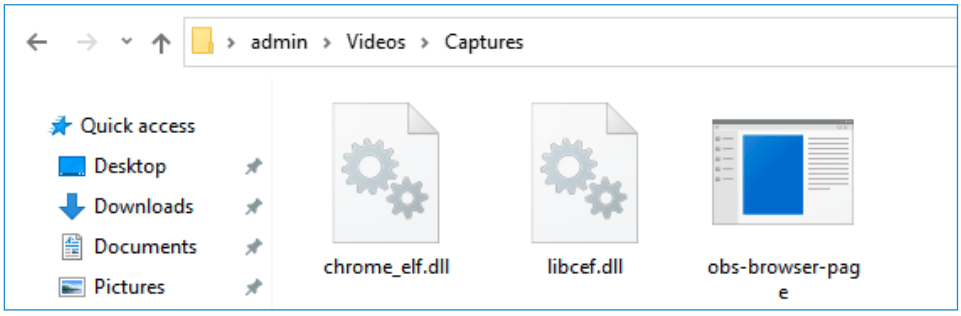
The Trojan achieves persistence by modifying the Windows Registry, ensuring it remains active across system reboots.
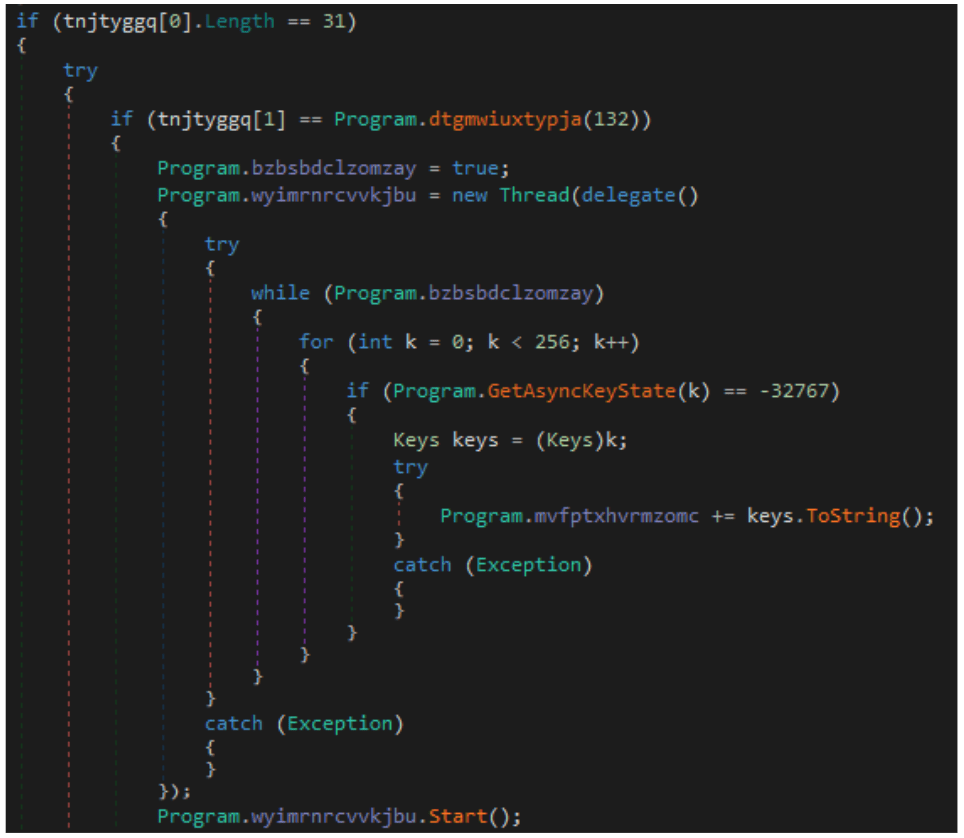
Coyote can execute 24 different commands, including:
- Keylogging: Captures keystrokes to steal sensitive information such as usernames and passwords.
- Screen capture: Takes screenshots of user activity to gather additional information.
- Full-screen overlay windows: Displays fake banking app overlays to deceive users into entering their credentials.
- Registry changes: Modifies the Windows Registry to achieve persistence and evade detection.
- Mouse control: Moves the user's mouse to interact with the system and execute additional commands.
- Machine shutdown: Forces the infected system to shut down to disrupt normal operations or to cover tracks.
- Communication with C2 servers: Establishes encrypted channels to communicate with command-and-control servers for instructions and data exfiltration.
Blackberry
Risk outlook
While Coyote's operation primarily targets Brazilian financial institutions, tracking this banking Trojan is crucial for global cybersecurity because cybercriminals often sell access to such malware to other threat actors in Europe and the U.S., who then augment its functionality to target banking institutions in those regions.
Blackberry
This practice of selling malware access facilitates the spread of sophisticated cyber threats across borders, necessitating vigilant monitoring and proactive defense measures worldwide to protect against evolving financial cyber attacks.







Leave a Reply