
Researchers at Check Point have uncovered the extensive use of Rafel RAT, an open-source remote administration tool, by various threat actors for espionage and ransomware operations on Android devices. This discovery highlights the persistent and evolving challenges posed by Android malware to users' privacy and security.
Rafel RAT leverages Android's open-source flexibility, enabling attackers to execute remote administration tasks, including data theft, device manipulation, and covert surveillance.
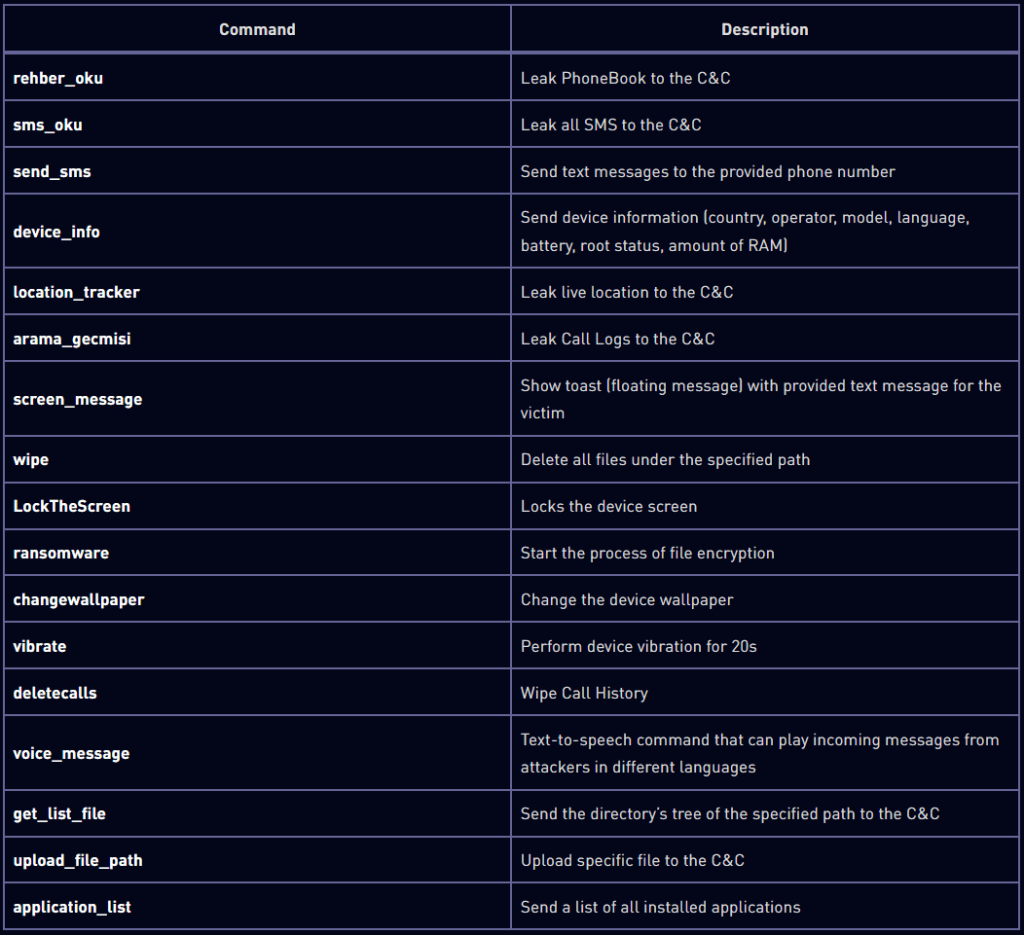
The malware's complete feature set includes:
- Remote access and control
- Data exfiltration (phone books, SMS, call logs)
- Device manipulation (screen lock, wallpaper change, device vibration)
- Ransomware operations (file encryption, data wiping)
- Surveillance (live location tracking, voice message playback)
Check Point
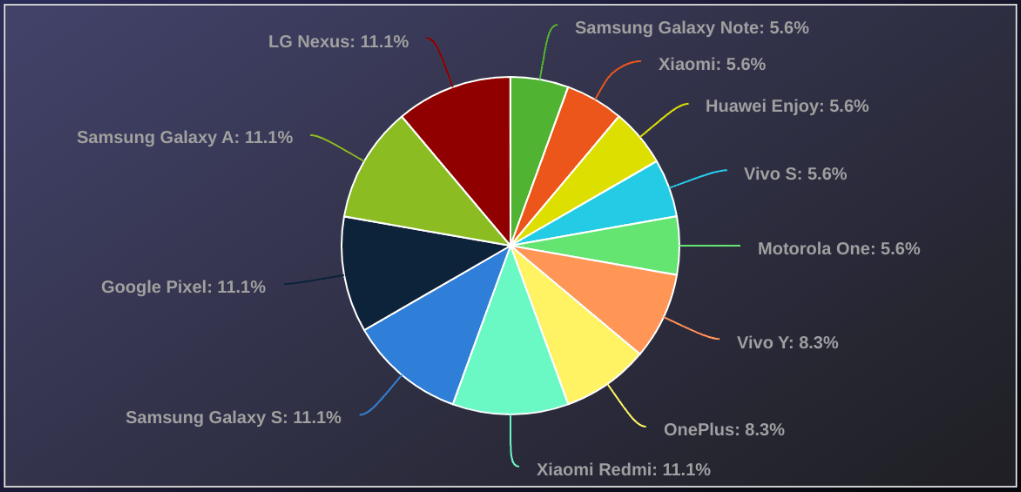
Check Point Research identified approximately 120 malicious campaigns utilizing Rafel RAT, targeting high-profile organizations such as military sectors, predominantly in the United States, China, and Indonesia. Victims primarily used Samsung, Xiaomi, Vivo, and Huawei devices, with a notable prevalence (87.5%) of Android versions no longer receiving security updates.
Check Point
The malware infiltrates devices primarily through phishing campaigns, masquerading as legitimate applications like Instagram, WhatsApp, and various e-commerce and antivirus platforms. Upon installation, it requests critical permissions to ensure persistence, such as access to SMS, call logs, contacts, and device admin rights.
Check Point
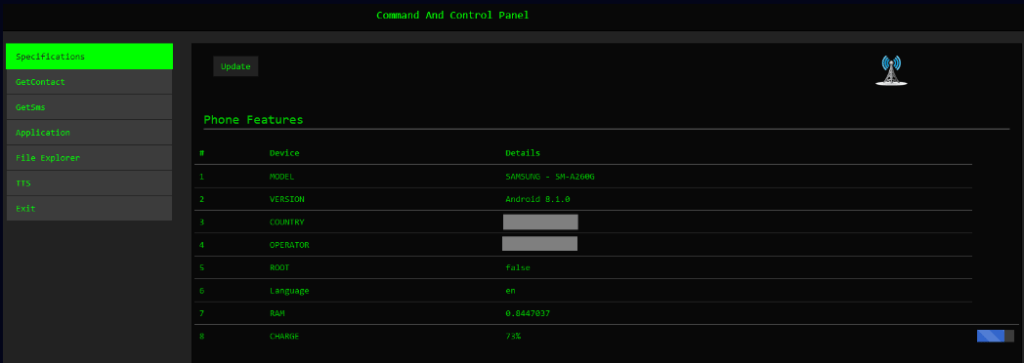
Rafel RAT's C&C infrastructure utilizes a PHP panel with JSON-based storage, facilitating real-time monitoring and control of infected devices. Commands executed from the panel include data exfiltration, device manipulation, and surveillance operations. Notably, the malware can intercept notifications, allowing attackers to capture 2FA codes and other sensitive information.
Deployment cases
- Ransomware operations: Attackers leverage Rafel RAT's capabilities to lock devices and encrypt files, demanding ransoms via SMS. One observed operation involved locking a victim's screen with the message “Loda Pakistan” and demanding ransom through a Telegram channel.
- Two-factor authentication bypass: The malware's ability to intercept and exfiltrate 2FA messages poses significant risks, enabling attackers to bypass additional security layers and access sensitive accounts.
- Government infrastructure targeting: In one instance, attackers compromised a Pakistani government website, using it as a C&C server for Rafel RAT. The hack was publicly boasted on a Telegram channel, indicating a targeted and coordinated effort by the threat actor.
Check Point's recommendations for users and organizations include:
- Regularly updating Android devices to the latest OS and app versions
- Avoiding downloads from untrusted sources (third-party app stores)
- Implementing robust endpoint protection solutions
- Use an up-to-date mobile security/antivirus product
- Keep ‘Play Protect' active on the device and run regular scans
The Rafel RAT exemplifies the sophisticated and versatile nature of modern Android malware. Its widespread usage underscores the critical need for continuous vigilance, advanced threat intelligence, and comprehensive security strategies to safeguard against evolving threats.







Leave a Reply