
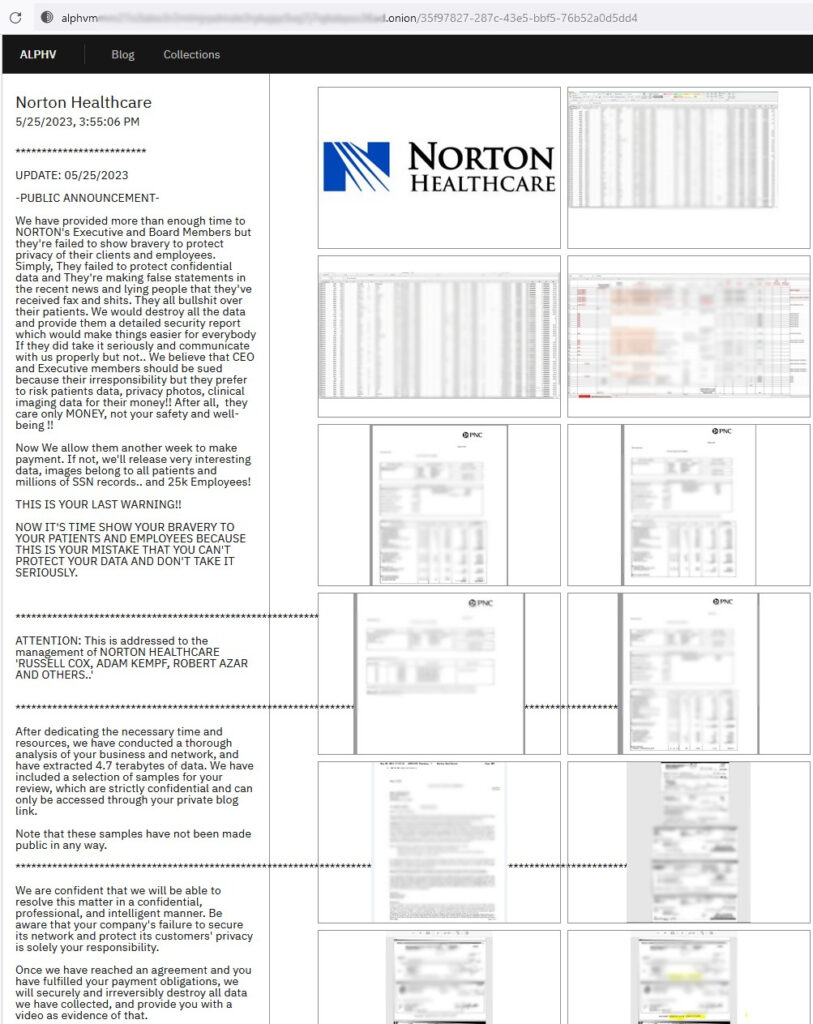
The BlackCat ransomware group, also known as ‘ALPHV,’ has claimed responsibility for the cyberattack that caused problems earlier in the month to Norton Healthcare, a healthcare provider that operates over 40 clinics and hospitals in the U.S. state of Kentucky.
The hackers claim to hold millions of medical records stolen from the healthcare system’s network, including SSNs (social security numbers), clinical images, test results, and more. Apart from patients, they claim to have information on 25,000 employees of Norton Healthcare.
The threat delivered by BlackCat is that the entire package of 4.7 terabytes they exfiltrated will be published, irreversibly exposing a large number of patients who received care in one of the organization’s medical centers.
Should Norton Healthcare choose to meet the threat actors’ demands by paying the ransom within a week (until June 1, 2023), the hackers have committed to deleting all stolen data. Moreover, they have pledged to supply video evidence of this action, although a video is far from a guarantee and cannot be deemed credible proof of deletion.
RestorePrivacy.com
Unfortunately, medical data are precious to threat actors, as they are rich in information and incredibly exposing for affected individuals, opening many possibilities for phishing, scams, and even social engineering. Hence, they are almost always resold to other cybercriminals for a significant profit.
Norton Healthcare Facing Problems
Visitors of the Norton Healthcare website will see a warning about a cyberattack that took place on May 9, 2023. The notice does not give away any other details about the incident, though. The organization claims that the ongoing investigation, which takes place with the help of contracted IT experts, does not allow extensive communication with patients and kindly requests patience.
“Norton Healthcare is working with third-party specialists to carefully examine and safely restore all network applications following the cyber event. This process is a time-consuming but critical part of the restoration process. We appreciate your patience as the investigation continues.”Norton Healthcare
An update on the organization’s news section mentions that by May 24, 2023, all online scheduling systems had returned to fully operational status, and so have the billing and doctor communication platforms. However, problems with the distribution of medical testing and imaging results in Norton Healthcare persist. Also, some scheduled procedures, exams, and appointments may have to be rescheduled, and the organization relies on the providers to communicate this need with impacted patients.
RestorePrivacy contacted Norton Healthcare to request more information about the cyberattack and ask about the veracity of BlackCat’s allegations, but, we have not received any official response at the time of publication.







Why they don’t encrypt sensitive data… I don’t understand.
Humdrum. Ransomware is the new normal. This is the grim reality that many organizations face today with their lazy IT admins.
All you need is a good backup system, a strong password/passphrase, and a healthy dose of skepticism. Don’t open suspicious attachments, don’t click on shady links, and don’t pay the ransom. It’s as simple as that.