
The adoption of two-factor authentication (2FA) as an account protection method pushes phishing actors to turn to reverse-proxy solutions that are becoming increasingly popular.
According to a report from Unit 42 of Palo Alto Networks, these attacks, otherwise called ‘meddler in the middle,' are effective enough to get around existing defenses and break down the brittle wall of perceived security.
The increased demand for reverse-proxy services that help phishing actors snatch two-factor authentication codes from their victims has resulted in the opening of two new platforms in 2022, assisting the technique to proliferate further.
How MitM Attacks Work
In traditional phishing attacks, the victim is lured into entering their credentials (username/email + password) on a phishing site. Then the threat actors may use the stolen pairs to log in to the victim's account.
If two-factor authentication is active on the account, the account owner will receive a one-time password (OTP) on their mobile via SMS or email. In other cases, authentication apps are used, which generate OTPs periodically for this purpose.
Whatever the method, the 2FA step would block account takeover attacks as the threat actors wouldn't have a way to guess the correct OTP.
This problem is solved by reverse proxy services such as Elivginx2, Modlishka, Muraena, EvilnoVNC, and EvilProxy. The last two were launched in 2022, offering more advanced features and user-friendly GUI-based environments.
Unit42
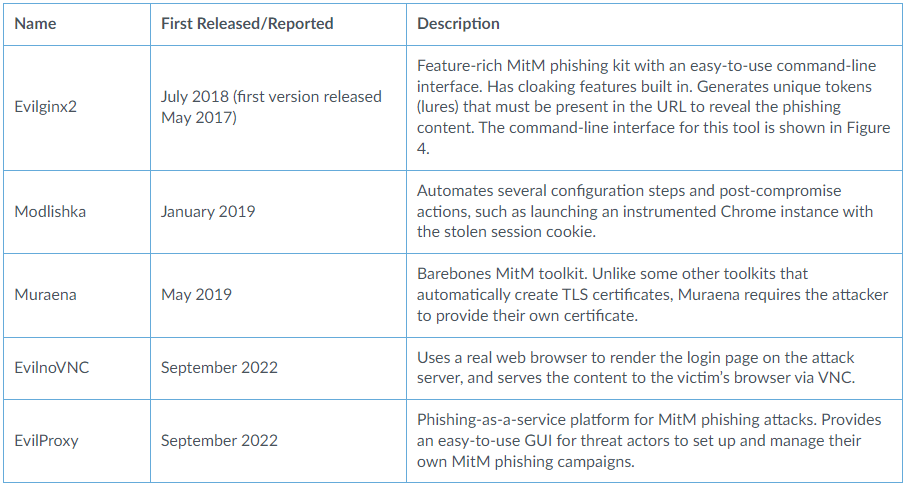
The platforms help phishing actors forward login requests to the actual services, relay 2FA requests back to the victims, and then forward the codes to the server, all happening using a reverse proxy.
A reverse proxy is a server that acts as an intermediary between Internet users and web servers located behind a firewall. It receives requests from Internet users and forwards them to the appropriate servers, then returns the servers' responses to the users. This setup allows web servers to serve requests without being directly exposed to the Internet.
The trick is that the phishing actor sits in the middle of this information exchange, snatching the authorization cookie the real service server generates once the correct 2FA code is provided.
Unit42
In summary, it's like facilitating the complete login process for the victim on the real service, logging them in and stealing their session while keeping the victim on the fake site the whole time.
Recent Campaigns
Unit42's report highlights three recent cases of MitM campaigns targeting valuable accounts using reverse proxy services.
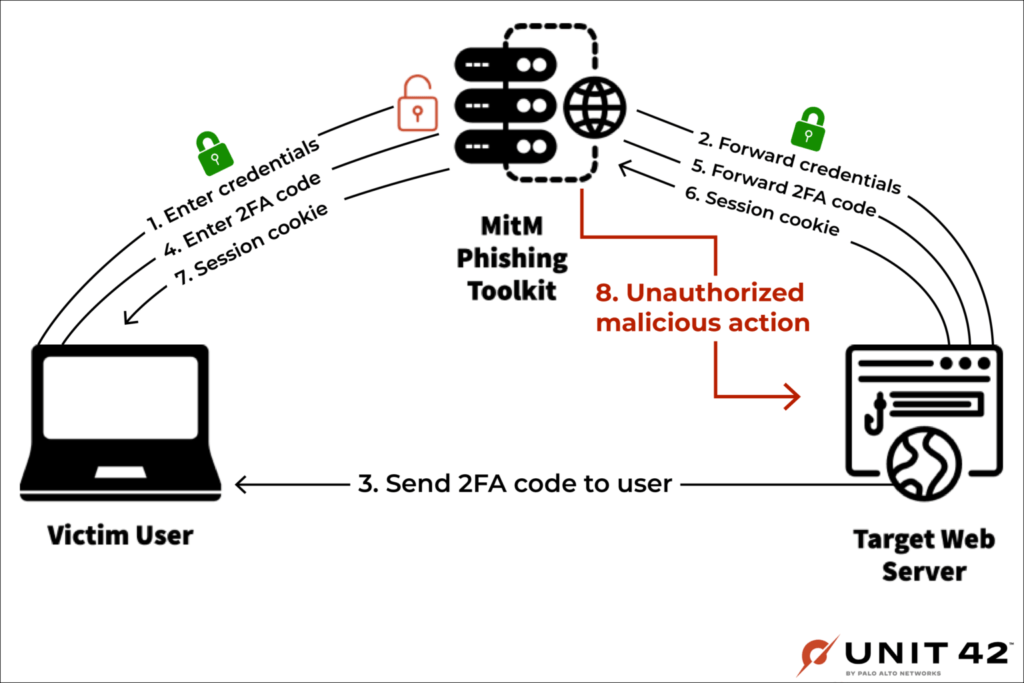
The first case was reported by Microsoft in July 2022, where the threat actors used Evilginx2 to steal Microsoft accounts after they lured targets with fake notices via email.
Unit42 spotted a similar campaign in recent weeks, which appears to be targeting Microsoft 365 accounts.
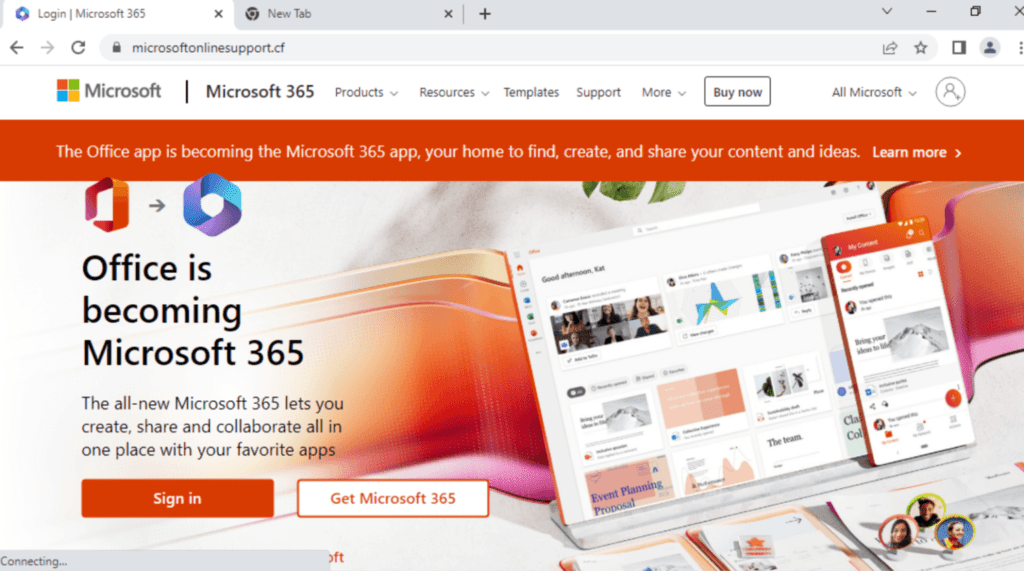
In September 2022, threat actors set up a MitM attack targeting CircleCI users and their GitHub credentials using a clone site that looked exactly like the real one.
Unit42
“For targets with OTP-based 2FA set up, the MitM server also prompted them to enter the OTP, which was then forwarded to GitHub, allowing for a successful login,” reads the Unit42 report.
“From there, attackers would persist in their access by quickly creating personal access tokens (PATs) or adding their own SSH keys to the victim's account.”
Unit42
Most recently, in November 2022, Dropbox disclosed it had fallen victim to a sophisticated MitM attack that resulted in the breach of 130 private repositories.
This incident convinced Dropbox it was time to abandon the 2FA account protection scheme for more robust, WebAuthn-based schemes.
How to Defend
Unfortunately, there's not much users can do to protect their accounts against MitM attacks besides being very cautious when requested to enter credentials and double-checking the URL of the site they're on.
User authentication servers could identify and filter out malicious forwarding requests only by implementing TLS fingerprinting on the client side, but the industry is quite far from that stage at the moment.
Currently, the only widely employed defense against these attacks is to use IP-based blocklists refreshed daily, which is obviously not good enough.






Can someone explain this risk and how these criminals harvest your account information like a five year old could understand or at least a 5th grader? That illustration is too complex for this old mind.
Some tips to prevent phishing MITM attacks:
1. Ad blocker like AdNauseam or Ublock Origin has a function to block phishing sites. Go to settings > Filter list > Malware > Check phishing URL blocklist.
2.. You can use Yubikey if you can.
https://www.yubico.com/phishing-attacks-are-getting-smarter/
3. You can check for phishing sites on checkphish.ai. .
4. Browser extensions like Bitwarden extension or KeepassXC extension can check whether that site is real or not. This works because the browser extension won’t autofill the password unless you’re on the correct website.
I have found 2FA is more hassle than it’s worth. One could be subject to mobile (network) outages and more preventing accessing their own account. Rarely does a website have more than one method of 2FA eg. SMS. email, landline, etc.
If someone is determined to hack your account, there’s very little you can do…unless perhaps you pay for a special service. I’m not convinced a DNS service is the solution like some people who believe they know “it all”. Besides, why should I pay be secure? That [should be] he role of the website admin.
I thought Cloudfare(1.1.1.1) was one of the best Secure DNS for browsing. I have all my browsers set to use it.
Is Quad9 or NextDNS better or in the same category?
Sven, you should do an article on this topic. Thanks.
That’s why a good DNS service, which protects from such attacks, is mandatory. For good security and privacy on DNS level you can try Quad9 or NextDNS.