
ENC Security, a Dutch company that provides encryption solutions to Lexar, SanDisk, Western Digital, and Sony, has had an API key data leak due to database misconfiguration.
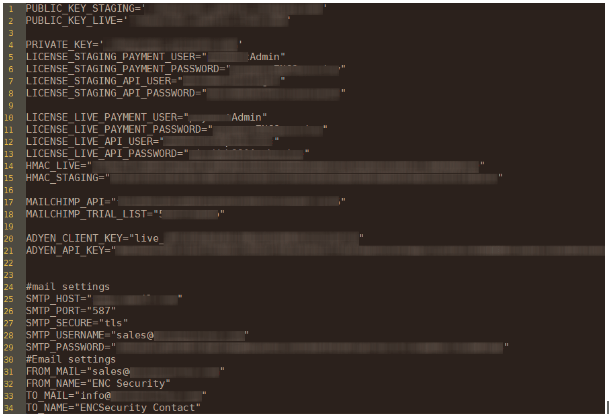
The exposed instance contained configuration data, certificate files, API keys, Mailchimp keys, email marketing details, HMAC authentication codes, asymmetric encryption keys (public and private pairs), and more.
The data was discovered by Cybernews researchers who were scanning the web for potentially exposed instances, and according to their report, it was publicly accessible from May 27, 2021, until November 9, 2022.
This was when ENC Security closed access to the exposed database, explaining that the incident occurred due to a misconfiguration by one of its third-party suppliers.
Impact and Risk
ENC Security is the vendor of the ENC DataVault product, a data encryption solution for Windows and Mac, enabling users to lock their data with a password and keep them safe even in the case of someone stealing their drives.
SanDisk, Lexar, Sony, and Western Digital use custom versions of DataVault to offer their customers out-of-the-box data encryption features on their hard disks and pen drives.
According to ENC, apart from the product sales of its partners, ENC DataVault is downloaded 2,000 times every month and used by 12 million individuals.
Exposing administrator API keys means allowing attackers to explore the organization's internal network, take over control of servers, and access payment or identification information of clients.
Cybernews
While it's unlikely that someone breaks DataVault's encryption scheme from this exposure, malicious actors could take advantage of their access to ENC's servers via alternative routes.
For example, they could replace files in download servers with laced installers to disseminate malware via the official ENC Security channels.
Also, the exposure of Mailchimp API keys could have fueled massive phishing campaigns, enabling the threat actors to send out a large number of phishing emails to ENC Security clients.
For example, sales communication channels could be used to phish clients by sending them fake invoices or spreading malware via trusted email addresses.
Cybernews researcher Martynas Vereikis
In this case, none of these scenarios manifested in reality. Still, the possibility for subtle exploitation like stealthy data exfiltration, access, and live database monitoring cannot be ruled out.
If you have an account at the ENC Security website or any of its products, it would be advisable to reset your password and wipe any sensitive data stored in it, like payment card data.
Even though the company has not sent out notices to its customers to perform such an action, it is recommended that you follow these steps out of an abundance of caution.






Hi RP,
This article is well out of my range of my technical understanding, though I can grasp at the potential consequences.
My threat model means (hopefully) that if this exploit was ever harnessed by a sophisticated actor, that they would not be interested in me.
May the good people of the world, be safe.