
A new “Antidot” Android banking trojan disguises itself as a Google Play update app. It targets Android users across various regions to harvest credentials using VNC and overlay techniques.
Cyble Research and Intelligence Labs (CRIL) identified the Antidot Trojan earlier this month. The trojan is noted for its complex features, including overlay attacks and keylogging, which compromise devices to steal sensitive information.
Technical details
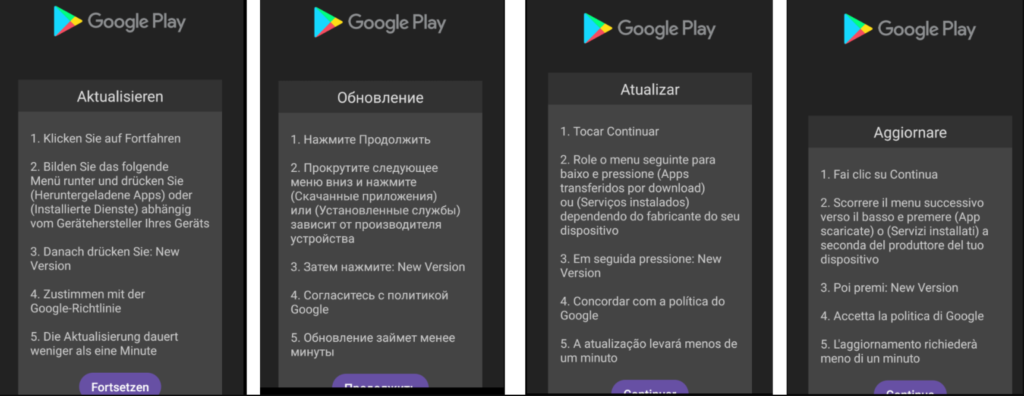
Antidot's primary method of operation involves masquerading as a Google Play update application. Upon installation, it displays a fake update page crafted in multiple languages, including German, French, Spanish, Russian, Portuguese, Romanian, and English, covering a broad targeting scope.
Cyble
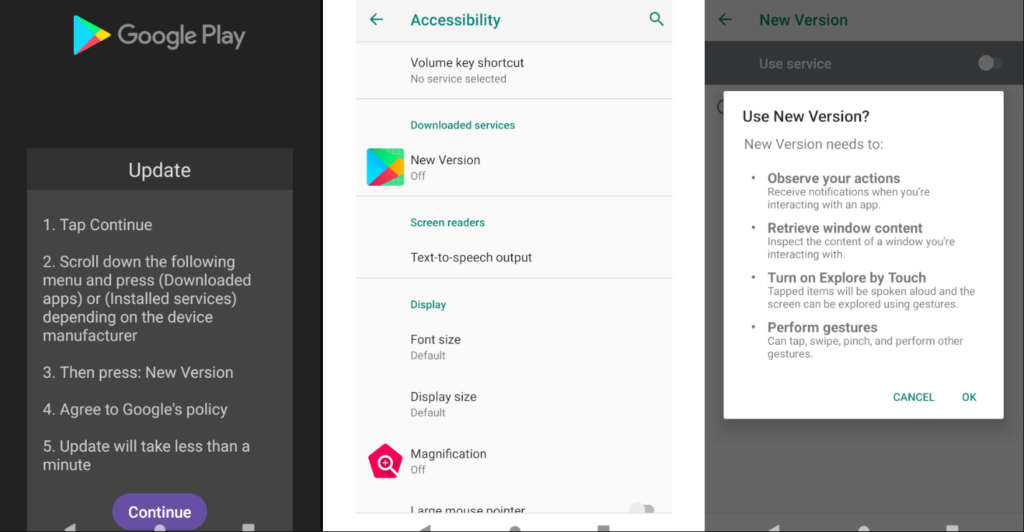
Once the fake update page is shown, the malware prompts users to grant Accessibility service permissions, which it exploits to execute its malicious activities.
Key features of Antidot include:
- VNC (Virtual Network Computing): Allows remote control of infected devices using MediaProjection.
- Overlay Attacks: Creates fake overlay windows to capture user credentials.
- Keylogging: Records and transmits keystrokes to steal information.
- Screen Recording: Captures screen content for further exploitation.
- Call Forwarding and SMS Collection: Gathers and forwards SMS messages and call data.
- Device Control: Remotely locks/unlocks the device, controls the camera, and performs USSD requests.
Antidot communicates with its C&C server through WebSocket, enabling real-time interactions. The malware sends “ping” messages with encoded data such as application names, device information, and locale settings. In return, the server responds with “pong” messages containing commands for the Trojan to execute. These commands range from collecting SMS messages and contacts to controlling device features like the camera and screen lock.
List of Commands Executed by Antidot:
- speedMod: Updates application scope list
- pauseInject: Pauses overlay activity
- stopCamera: Stops the camera
- unlockDevice: Unlocks the device
- getSms: Collects SMS messages
- callForward: Makes calls from the infected device
- startVnc: Initiates VNC activity
- lockDevice: Locks the device
- sendPush: Sends push notifications
- getContacts: Collects contact lists
Antidot employs HTML phishing pages to mimic legitimate banking or cryptocurrency apps. These pages are loaded into WebView, creating an overlay on the actual application to capture user credentials. The malware uses the package name list of installed applications to identify targets and then deploys the phishing pages accordingly.
In addition to overlay attacks, Antidot's keylogging feature transmits keystrokes to its C&C server. The VNC feature allows remote control of the infected device's screen, enabling actions such as tapping, swiping, and accessing recent apps. These actions are executed through abuse of the Accessibility service, making the malware particularly dangerous.
Cyble
If the device is not the intended target, the C&C server can send an “SOS” command. This command prompts the user to uninstall the malware, preventing further malicious activity on that device.
Defense tips
The Antidot Android Banking Trojan represents a significant threat due to its advanced features and stealthy operations. Its ability to perform overlay attacks, keylogging, and remote control via VNC poses a severe risk to user privacy and financial security.
To mitigate this threat and most Android malware risks, apply the following:
- Install software only from official app stores like Google Play and the iOS App Store.
- Use reputable antivirus and internet security software on all devices.
- Employ strong passwords and multi-factor authentication wherever possible.
- Be cautious with links received via SMS or email.
- Enable Google Play Protect on Android devices.
- Carefully review app permissions before granting access.
- Keep all devices and applications up to date with the latest security patches.







Leave a Reply