
A newly identified vulnerability in the WordPress plugin “Email Subscribers by Icegram Express,” tracked as CVE-2024-2876, has been disclosed.
Carrying a critical CVSS score of 9.8, this security flaw threatens the integrity and confidentiality of over 90,000 websites, making it a prime target for malicious attacks through SQL injection.
Vulnerability details
The security loophole manifests as an SQL injection vulnerability found in all plugin versions, including 5.7.14. The issue arises from the plugin's handling of user-supplied data and its preparation of SQL queries within the ‘IG_ES_Subscribers_Query' class. Specifically, the flaw allows attackers to manipulate SQL commands by inserting unauthorized SQL queries directly into the WordPress database. This vulnerability compromises data integrity and exposes sensitive information like password hashes.
The exploitation of CVE-2024-2876 was brought to light by the WordPress security company Patchstack, which first reported it on March 13, 2024. However, significant exploitation began in May following the release of a Nuclei template on GitHub, which detailed how to exploit this vulnerability.
Since then, the Wallarm WAAP platform has detected over 3,000 malicious requests related to this flaw. These attempts typically involve unauthorized database queries and can even escalate to creating new admin accounts on affected sites, further compromising the sites' security.
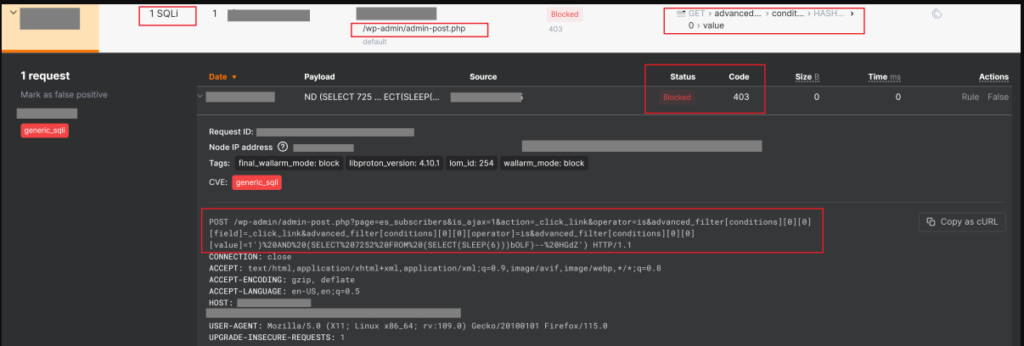
This revelation is part of a larger issue involving several other critical vulnerabilities in WordPress plugins, such as Forminator (CVE-2024-28890) and User Registration (CVE-2024-2417), notes Wallarm in its report. These vulnerabilities are equally severe, offering pathways for attackers to steal data, upload files, and gain unauthorized administrative privileges, potentially turning affected websites into launchpads for further malicious activities.
Remediation recommendations
To mitigate the risks associated with CVE-2024-2876, the following actions are recommended for website administrators:
- Ensure that “Email Subscribers by Icegram Express” is updated to version 5.7.15 or the latest release, 5.7.19.
- Patchstack users should enable automatic updates for plugins known to be vulnerable.
- Integrate a Web Application Firewall (WAF) or Web Application and API Protection (WAAP) solution, which could help block attacks even if those involve zero-day vulnerabilities.







Leave a Reply