
Just days after Apple implemented a significant update to its XProtect malware signature system, new variants of the notorious Adload adware have surfaced, already circumventing the new protective measures. This rapid adaptation highlights the ongoing cat-and-mouse game between cybercriminals and cybersecurity defenses.
On May 1, 2024, Apple rolled out 74 new rules in XProtect version 2192, followed by an additional 10 in version 2193, aimed predominantly at combating the widespread Adload adware. Historically, before this update, XProtect had 207 rules, including about two dozen targeting Adload specifically. The latest updates represented a 24% increase in the rule count, indicating a robust attempt by Apple to disrupt Adload's operations significantly.
Despite Apple's intensive efforts, involving thorough research and testing to prevent false positives, the adware developers quickly adjusted their strategy. SentinelOne detailed observations of new Adload versions that evade the updated XProtect signatures as early as last week. While many were still detected by other vendor engines, by the weekend, certain samples were bypassing detection across multiple platforms, including VirusTotal.
New Adload variant
The newly observed Adload variant, with minimal detections on VirusTotal, is an x86_64 Intel architecture-specific dropper with a file size of 4.55MB. This variant does not show any linkage to a parent executable, application, or disk image, and lacks code signing—common indicators of distribution through cracked or trojanized apps via malicious websites or torrents.
This variant interacts with several custom domains registered under NameCheap that follow known Adload patterns, such as:
- api.deployquest.com
- api.searchwebmesh.com
- api.generalmodules.com
Upon execution, the dropper uses the ioreg utility to gather system information and resolves a hardcoded domain name to download a payload, which is then written to a temporary directory. Notably, if the payload is not a compressed archive, the directory contains an HTML 404 response, indicating an unsuccessful download.
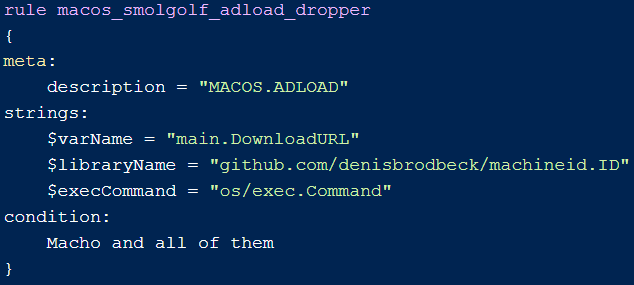
Analyzing the binaries from a static perspective, these employ legitimate external Go packages for machine ID determination and command execution. However, they've adjusted from previous detection methods. For instance, the malware authors replaced “main.DownloadURL” with “main.dwnldUrl”, helping to bypass Apple's signature rules such as the one targeting these specific strings in macos_smolgolf_adload_dropper.
SentinelOne
As malware authors continue to evolve their strategies, enterprises must remain vigilant and employ comprehensive security solutions. Apple is likely to update its signatures in response to these new developments, but the transparent nature of XProtect's YARA rules means that any changes could quickly be circumvented again.







Leave a Reply