
A verified Twitter vulnerability from January has been exploited by a threat actor to gain account data allegedly from 5.4 million users. While Twitter has since patched the vulnerability, the database acquired from this exploit is now being sold on a popular hacking forum, posted earlier today.
Back in January, a report was made on HackerOne of a vulnerability that allows an attacker to acquire the phone number and/or email address associated with Twitter accounts, even if the user has hidden these fields in the privacy settings.
The bug was specific to Twitter’s Android client and occurred with Twitter’s authorization process.
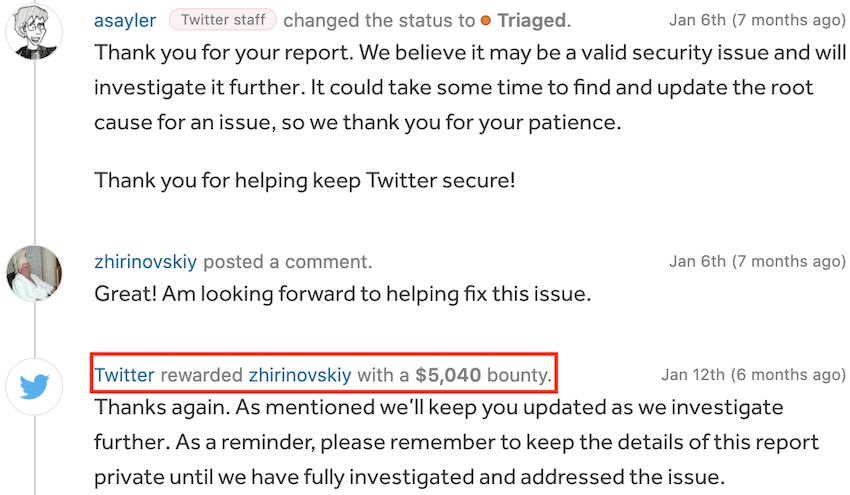
The HackerOne user “zhirinovskiy” submitted the bug report on January 1st of this year. He described the potential consequences of this vulnerability as a serious threat that could be exploited by threat actors.
This is a serious threat, as people can not only find users who have restricted the ability to be found by email/phone number, but any attacker with a basic knowledge of scripting/coding can enumerate a big chunk of the Twitter user base unavaliable to enumeration prior (create a database with phone/email to username connections). Such bases can be sold to malicious parties for advertising purposes, or for the purposes of tageting celebrities in different malicious activities– HackerOne user zhirinovskiy
The HackerOne report subsequently lays out exactly how to replicate the vulnerability and acquire the data from a targeted Twitter account.
Five days after posting the report, Twitter staff acknowledged this to be a “valid security issue” and promised to investigate further. After further investigating the issue and working to fix the vulnerability, Twitter awarded user zhirinovskiy with a $5,040 bounty.
Exploiting this vulnerability with the Twitter Android client is described as follows on the HackerOne report:
The vulnerability allows any party without any authentication to obtain a twitter ID (which is almost equal to getting the username of an account) of any user by submitting a phone number/email even though the user has prohibitted this action in the privacy settings. The bug exists due to the proccess of authorization used in the Android Client of Twitter, specifically in the procces of checking the duplication of a Twitter account.– HackerOne user zhirinovskiy
Today, however, we see the consequences of this vulnerability come to fruition.
Hacker lists database of 5.4 million Twitter users for sale
Exactly as the HackerOne user zhirinovskiy described in the initial report in January, a threat actor is now selling the data allegedly acquired from this vulnerability.
Earlier today we noticed a new user selling the Twitter database on Breached Forums, the famous hacking forum that gained international attention earlier this month with a data breach exposing over 1 billion Chinese residents.
The post is still live now with the Twitter database allegedly consisting of 5.4 million users being for sale. The seller on the hacking forum goes by the username “devil” and claims that the dataset includes “Celebrities, to Companies, randoms, OGs, etc.”
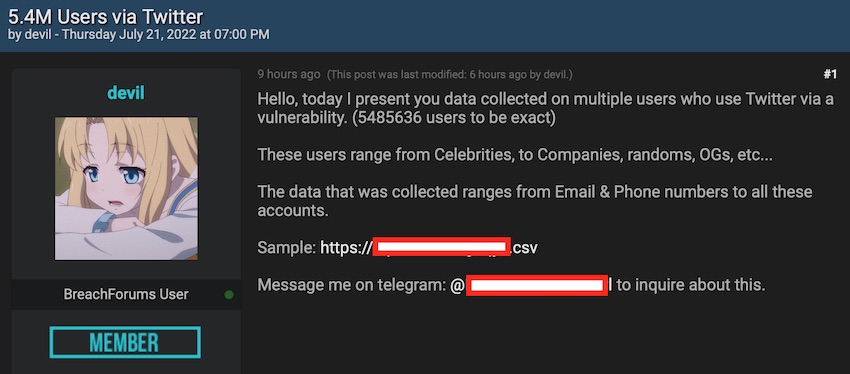
A few hours after the post was made, the owner of Breach Forums verified the authenticity of the leak and also pointed out that it was extracted via the vulnerability from the HackerOne report above.
The Breach Forums user selling the database also posted a sample of the data.
Analysis and verification of the data sample
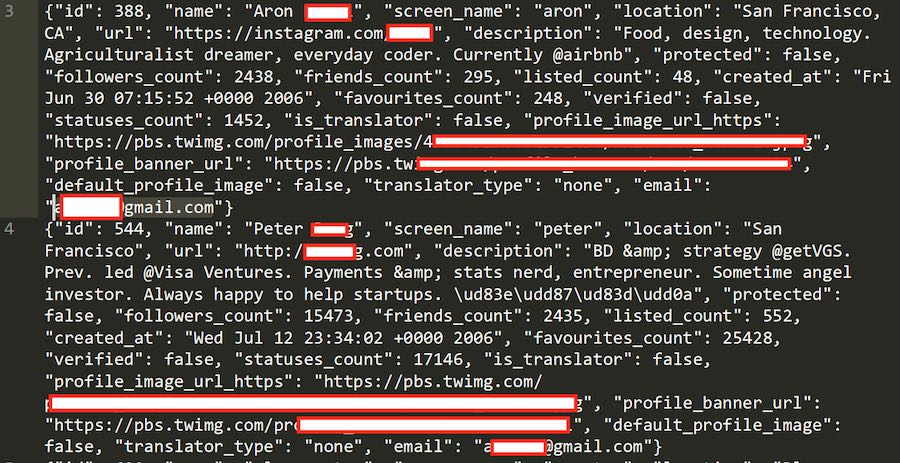
We downloaded the sample database for verification and analysis. It includes people from around the world, with public profile information as well as the Twitter user’s email or phone number used with the account.
Below are two samples from the database we examined. All samples we looked at match up with real-world people that can be easily verified with public profiles on Twitter.
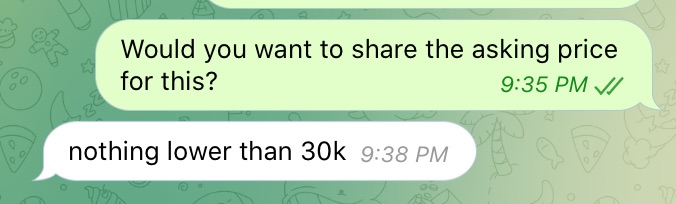
We reached out to the seller of this database to gather additional information.
He told RestorePrivacy that all of the information was already disclosed in the HackerOne report. The seller is asking for at least $30,000 for the database, which is now available due to “Twitter’s incompetence” according to the seller.
We reached out to Twitter for comment on this situation on July 21, 2022.
Update July 24, 2022: Twitter has confirmed they are investigating the situation.







Rather weird request, but I’m a journalist based in India covering crime and cybersecurity. I wanted to ask if I could use the images from this write up with my own article. I’d be happy to give credit to Restore Privacy, if that is required.
My name is Gautam S. Mengle, and I work for the Free Press Journal in Mumbai, India.
Please permit me to thank you in advance.
Hi Gautam, provided you credit this site and link to our report, no problem, go right ahead. Thanks for asking.
I’ve had it with Twitter.
I agree we need a workaround against websites who insist on Two-factor authentication (2FA) where they only send texts which can’t be received on landlines.
Many people, especially our elders, don’t have a cell phone (they have a landline) and they use a tablet. They don’t have a mobile number. It’s not just them, but many now. We also want to keep our cellphone number private to reduce the likelihood of such breaches.
We need some options here, Sven. Can you research the subject on which services will accept short (sms) codes?
Hi Sven,
Great reporting!
I would only echo the point made by Judy A Zwyghuizen in the comments below.
Judy A Zwyghuizen: “So how would we know if we were Breached ????”
Has Twitter informed the affected users?
Regards,
BoBeX
Isn’t 2FA the same as providing your mobile number to Twitter when they decide to be stupid and insist you provide a valid non sip VoIP number? That’s what’s happening lately and none of the third party websites work as Twitter recognizes them as non carrier specific numbers.
Can Sven provide a review or tutorial for a workaround?
Hi Sven, If the hackers obtained the phone numbers of the Twitter accounts, would the two-factor identification (SMS) be compromised? So, is it safe to use SMS two-factor authentication ?? Maybe not finally
No, 2FA should not be affected.
Hack Twitter
Twitter should buy the database. It’s the least they could do to protect their users.
Yes. Which forum this database are?
Twitter should pay more for vulnerabilities that affect users in line,
Yes
I agree with the and all public media
Elon Musk looking away.
It’s strategic. Musk will probably end up buying Twitter anyway.
Was probably him trying to drive down price
And twitter still insists on you providing them a legitimate non-voip phone number to verify your identity
So how would we know if we were Breached ????
So what is the relationship between Zhirinovskiy on Hacker One and Devil on that hacking forum?
Yup. That’s the first thing that popped into my head.
“”I don’t want to white hat in trouble who reported it on H1. I guess a lot of people are trying to connect him to me, I would be pissed if I was him. So I cant stress this enough I have nothing to do w him nor H1,” the threat actor told BleepingComputer.”
oh yep, it’s definitely him